Best practices for managing security questionnaires efficiently
Share This Article
Understanding Security Questionnaires
Importance of Security Questionnaires
Security questionnaires are vital for vetting vendors before onboarding, ensuring responsible data handling by third-party vendors. They help organizations avoid risks such as data breaches, regulatory actions, financial losses, litigation, and reputational damage. Properly managed questionnaires also help maintain customer trust and facilitate acquiring new customers (UpGuard).
According to a recent study by Deloitte, 70% of companies rate their dependency on vendors as moderate to high. Since 2016, half of the respondents experienced a breach due to insecure vendor relationships (OneTrust). This statistic underscores the significance of thorough vetting processes, making [best practices for security questionnaires] a crucial aspect of vendor management.
Role in Vendor Risk Assessment
Security questionnaires play a pivotal role in assessing an organization's cybersecurity posture. They aid in evaluating the operational practices and internal controls of potential partners. Common questions focus on how server environments are secured, such as network segmentation and password complexity. Over time, the scope has expanded to include inquiries about multi-factor authentication, secure software development practices, and vulnerability scanning (LinkedIn).
Key areas covered often include:
Data Handling Procedures: Ensuring data is processed, stored, and transmitted securely.
Access Controls: Examining how access to sensitive information is controlled.
Employee Training: Assessing the level of cybersecurity awareness and training amongst the partner's staff.
Security and compliance officers, IT managers, and SaaS startups can benefit from understanding and implementing these questionnaires. The process helps in identifying potential security gaps and ensuring that partners adhere to the required standards.
For more on overcoming common pitfalls in security questionnaires, such as providing inconsistent information, visit our section on common frustrations with security questionnaires.
By adhering to best practices for security questionnaires, organizations can streamline response processes and enhance their overall security posture. For those interested in leveraging technology for improvement, our article on tools to simplify security questionnaires provides valuable insights.
By incorporating these practices into their security questionnaires, organizations can ensure a robust vendor risk assessment process, essential for maintaining a secure ecosystem.
Best Practices for Security Questionnaires
Security questionnaires are essential tools for evaluating vendor risk and ensuring compliance. Adopting best practices for creating and responding to these questionnaires improves efficiency and enhances security measures.
Creating Effective Questionnaires
Crafting effective security questionnaires starts with a well-thought-out plan. Here are several key practices to consider:
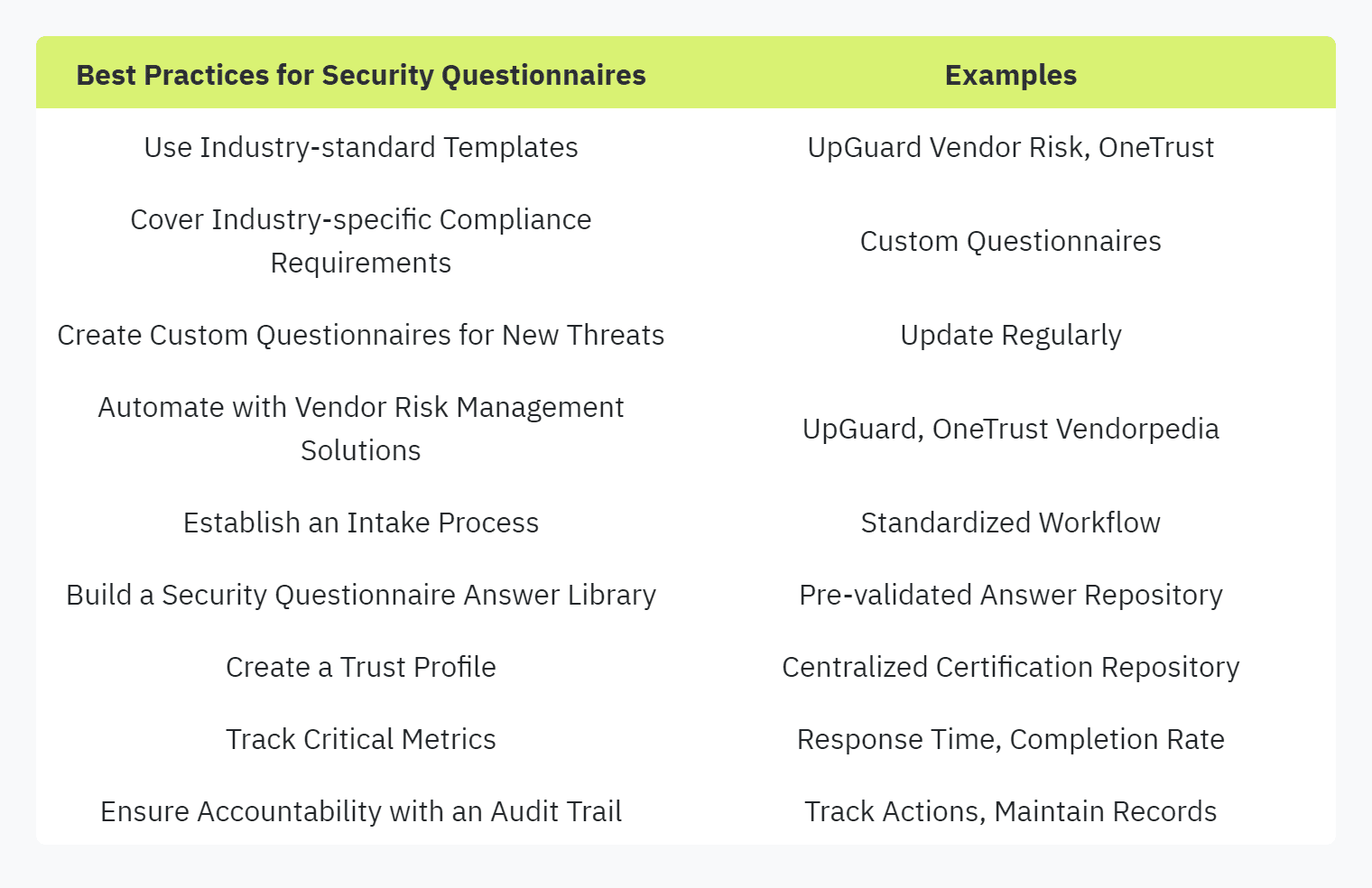
Use Industry-standard Templates: Utilize widely accepted templates as a baseline. This ensures that all essential security areas are covered and facilitates smoother communication with vendors. UpGuard Vendor Risk, for example, provides templates that align with industry-specific compliance requirements (UpGuard).
Cover Industry-specific Compliance Requirements: Customize questionnaires to address specific compliance requirements pertinent to your industry. This helps in capturing all necessary data from vendors, ensuring no compliance aspects are overlooked.
Create Custom Questionnaires for Emerging Threats: Stay ahead of new security threats by regularly updating and creating custom questionnaires. This proactive approach helps in identifying and mitigating evolving risks effectively.
Automate with Vendor Risk Management Solutions: Leverage tools like UpGuard Vendor Risk to automate the creation and management of security questionnaires. Automation reduces the manual workload and ensures a consistent approach to vendor assessment (OneTrust).
For a comprehensive guide on creating efficient questionnaires, refer to our article on automating security questionnaires.
Streamlining Response Processes
Responding to security questionnaires can be a complex and time-consuming task, especially with the involvement of multiple stakeholders and tight deadlines. Adopting a streamlined approach can significantly enhance efficiency:
Establish an Intake Process: Set up a standardized intake process to manage incoming questionnaires. This ensures a systematic approach and helps in tracking all requests efficiently.
Build a Security Questionnaire Answer Library: Develop a repository of pre-validated answers to frequently asked questions. This library speeds up the response process and ensures consistent information across all questionnaires (OneTrust).
Create a Trust Profile: Maintain a comprehensive profile that includes all relevant certifications, policies, and security documentation. This centralized repository can be shared with vendors to address common queries quickly.
Track Critical Metrics: Monitor key performance indicators such as response time, the number of completed questionnaires, and areas of improvement. Tracking these metrics helps in identifying bottlenecks and continuously enhancing the response process. For more on this, see our article on key metrics for security questionnaire automation.
Ensure Accountability with an Audit Trail: Implement an audit trail to track all actions and responses. This guarantees accountability and provides a clear record for future reference or audits.
By following these best practices, organizations can significantly improve the efficiency of their security questionnaire processes and ensure accurate, timely responses. To dive deeper into strategies for streamlining these processes, visit our article on streamlining security questionnaires.
For more insights on automation and best practices, check out our comprehensive guide to automating security questionnaires.
Overcoming Common Pitfalls
Navigating security questionnaires presents several challenges. Two significant pitfalls are rushing through questionnaires and providing inconsistent information. Addressing these issues can enhance accuracy and efficiency, supporting best practices for security questionnaires.
Rushing Through Questionnaires
One major pitfall in completing security questionnaires is the tendency to rush through them, especially when pressured to meet deadlines. This haste can compromise the accuracy and quality of the responses, potentially leading to mistakes or omissions. These errors can affect your organization’s credibility and increase the risk of non-compliance.
A better approach involves allocating sufficient time and resources for the task. It is advisable to start the process early and adhere to a structured plan. Implementing a review process where multiple team members verify the answers before submission can also mitigate errors.
Here’s a recommended workflow to manage the process efficiently:
Initial Review: Conduct a preliminary scan to understand the scope and complexity.
Delegate Tasks: Assign sections to relevant experts within the organization.
Draft Responses: Prepare detailed answers for each section.
Internal Review: Cross-check responses to ensure accuracy and completeness.
Final Review: Perform a final check before submission.
For more detailed strategies, see our guide on reducing time to complete security questionnaires.
Providing Inconsistent Information
Another common issue is the provision of inconsistent information across different security questionnaires. This inconsistency can arise due to the lack of a centralized repository of responses or having multiple individuals working on different questionnaires without adequate communication.
Maintaining a centralized repository of standard responses can significantly reduce this risk. Using automation tools to track and suggest consistent answers also helps. These tools can draw from previously given responses, ensuring that the information provided remains uniform across all questionnaires.
A reliable system for tracking responses should include:
Centralized Storage: A repository containing all standard responses.
Version Control: Maintain records of changes to each response.
Automated Suggestions: Tools that use previous responses to suggest answers.
Regular Updates: Periodically review and update the repository to reflect any policy or procedure changes.
By using these methodologies, organizations can maintain consistency and avoid contradictory responses. For a deeper understanding of how automation can help, read our article on automating security questionnaires.
Implementing these best practices will not only streamline the process but also ensure accuracy and reliability in your security questionnaire responses. Explore our resources on streamlining security questionnaires for more insights on improving your approach.
Enhancing Security Questionnaires
Enhancing the efficacy of security questionnaires can significantly streamline vendor risk assessment processes. Implementing automation tools and utilizing additional assessment methods are key strategies to achieve this.
Leveraging Automation Tools
Automation tools play a crucial role in managing security questionnaires efficiently. By automating repetitive tasks, organizations can save time, reduce errors, and ensure consistency in responses. Here are some best practices for leveraging automation in security questionnaires:
Utilize Vendor Risk Management Solutions: Tools like UpGuard's Vendor Risk UpGuard provide templates based on industry standards, covering specific compliance requirements, and allow customization to address emerging threats.
Automate Response Processes: Incorporate platforms such as SecureStack's continuous compliance module LinkedIn, which automates responses to security questionnaires, ensuring real-time compliance reporting.
Create a Library of Standard Answers: Build a repository of pre-approved responses to common questions. This library can be integrated into automation tools for quick and consistent answers.
Implement Metrics and Analytics: Use tools that track key metrics and provide visibility into questionnaire response times, accuracy, and compliance alignment (OneTrust).
For more on leveraging these tools, explore our comprehensive guide to automating security questionnaires.
Additional Assessment Methods
Beyond automation, incorporating additional assessment methods can further enhance the effectiveness of security questionnaires. These methods provide a comprehensive understanding of the vendor's security posture:
Vulnerability Analysis and Compliance Alignment: SecureStack’s platform offers tools for continuous vulnerability analysis and alignment with compliance frameworks like ISO27001, SOC2, and NIST 800-53 (LinkedIn). This approach ensures up-to-date and accurate assessments.
Trust Profiles and Documentation Sharing: Establish trust profiles for vendors that include detailed security documentation, certifications, and previously approved responses. This not only speeds up the process but also enhances transparency.
Audit Trails: Maintain an audit trail of questionnaire responses and interactions to ensure accountability and traceability. This is particularly important for meeting regulatory requirements.
Collaboration Platforms: Use collaboration tools to facilitate communication and coordination among stakeholders involved in responding to and managing security questionnaires (OneTrust).
For more insights on utilizing additional assessment methods, check out our article on tools to simplify security questionnaires.
By incorporating automation tools and supplementary assessment techniques, security and compliance officers can significantly enhance the management and efficiency of security questionnaires, ensuring thorough and reliable evaluations. For further reading, refer to our articles on streamlining security questionnaires and improving security questionnaire experience.
Enter your email to start accelerating your sales today.
















