Simplifying security questionnaire language to avoid confusion
Share This Article

Understanding Security Questionnaires
Security questionnaires are fundamental tools in today's business environment, especially for ensuring trust and compliance between vendors and organizations. This section focuses on the importance of these questionnaires and how they can be customized for specific needs.
Importance of Security Questionnaires
Security questionnaires serve as a bridge of trust in vendor relationships, ensuring that partners adhere to security standards and protect sensitive data. They are crucial for mitigating legal and financial risks. In the wake of increasing cybersecurity threats, these questionnaires are indispensable for maintaining the integrity and security of business operations.
Key Purposes:
Assessing Security Measures: Organizations use these questionnaires to evaluate the security protocols of potential vendors and partners, thereby ensuring compliance with industry standards.
Mitigating Risks: They help in identifying vulnerabilities in the systems of third-party vendors, allowing organizations to take preventive measures.
Ensuring Data Protection: They ensure that sensitive information shared with vendors is safeguarded according to regulatory requirements.
To learn more about the challenges and frustrations of dealing with security questionnaires, refer to our article on common frustrations with security questionnaires.
Customizing Security Assessments
Customizing security assessments to address specific concerns and industry needs is essential for effective risk management. Tailoring the questions and criteria to align with the unique systems and goals of an organization can provide more accurate and relevant insights.
Key Customization Points:
Industry Needs: Different industries have varying security requirements. Customizing questionnaires to include sector-specific questions ensures that the assessment is comprehensive.
Specific Concerns: Addressing particular vulnerabilities and risks pertinent to a company's infrastructure can help in creating more focused and useful assessments.
Company Policies: Tailoring the questionnaire to align with internal policies and procedures ensures that the responses are in sync with the company's security objectives.
Utilizing automated tools can further streamline this customization process, as outlined in our guide on automating security questionnaires.
Customization Benefits:

Explore more about improving the efficiency of security questionnaires through tailored content and automation to make the process less cumbersome.
To sum up, understanding the importance and customizability of security questionnaires can greatly enhance their effectiveness and the security posture of an organization. For further insights on efficiently managing these questionnaires, our article on streamlining security questionnaires is a valuable resource.
Types of Security Questionnaires
Understanding the differences between various security questionnaires is crucial for effective vendor risk management. This section covers standardized versus customized questionnaires, and third-party versus regulatory assessments.
Standardized vs. Customized Questionnaires
Standardized Questionnaires
Standardized security questionnaires provide a uniform set of questions designed to assess general security practices across various vendors. These questionnaires can include industry-standard formats such as CAIQ, CIS Critical Security Controls, SIG/SIG-Lite, and NIST 800-171 (Hyperproof). These formats offer a structured approach, ensuring comprehensive and consistent evaluations.

Using standardized questionnaires allows for easier comparison between vendors and reduces the burden on security and compliance officers through uniform assessment criteria.
Customized Questionnaires
Customized security questionnaires are tailored to address specific security concerns unique to an organization or industry. These assessments can be designed to focus on bespoke systems, particular compliance requirements, or unique security goals.
Custom questionnaires can vary greatly and include specific inquiries relevant to an organization's operational environment or proprietary systems. They provide greater flexibility in addressing precise security needs but may require more effort to develop and analyze.
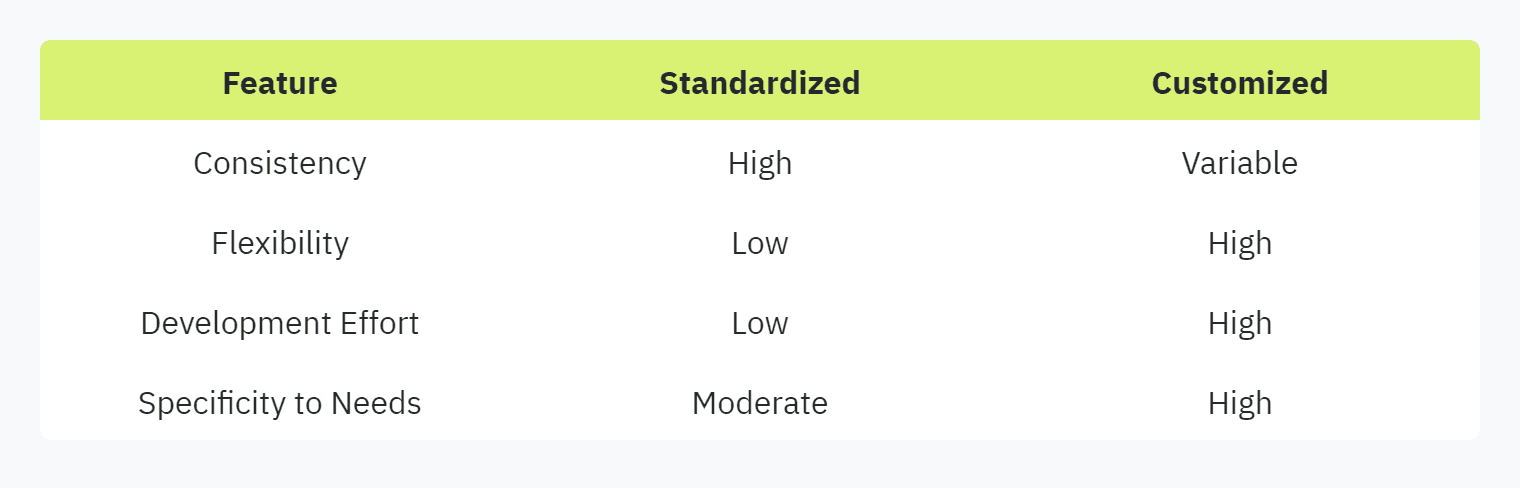
For organizations with unique security requirements or advanced security postures, customized questionnaires can offer valuable insights that standardized ones might miss.
Third-Party and Regulatory Assessments
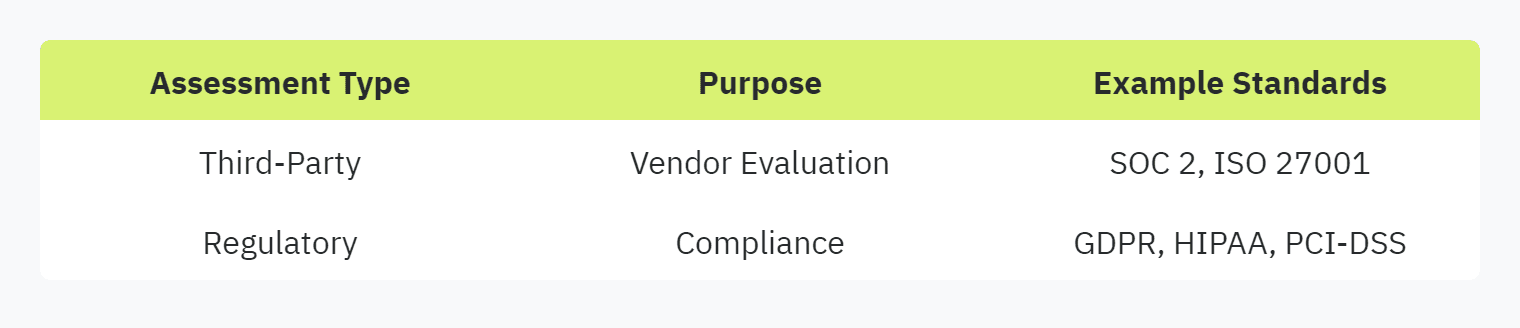
Third-Party Assessments
Third-party security assessments focus on evaluating the security measures implemented by external vendors or partners. These questionnaires aim to ensure that third parties adhere to acceptable security standards, thereby reducing risks associated with external dependencies (Vendict).
Third-party assessments can be both standardized and customized, depending on the organization's needs and the level of scrutiny required. They are essential for maintaining trust and accountability in business relationships.
Regulatory Assessments
Regulatory assessments are designed to ensure compliance with specific laws, regulations, and industry standards. These questionnaires often follow strict formats mandated by regulatory bodies, focusing on areas such as data protection, privacy, and industry-specific security requirements (Vendict).
Some common regulatory frameworks include GDPR for data protection, HIPAA for healthcare, and PCI-DSS for payment card security. These assessments are crucial for avoiding legal and financial repercussions due to non-compliance.
For security and compliance officers, understanding these different types of assessments is key to effectively managing vendor security assessments and ensuring adherence to relevant standards and regulations. Automating these processes can streamline the workflow, making it easier to manage and respond to multiple questionnaires (tools to simplify security questionnaires). For more insights on automation, visit our guide to automating security questionnaires.
Streamlining with Automation
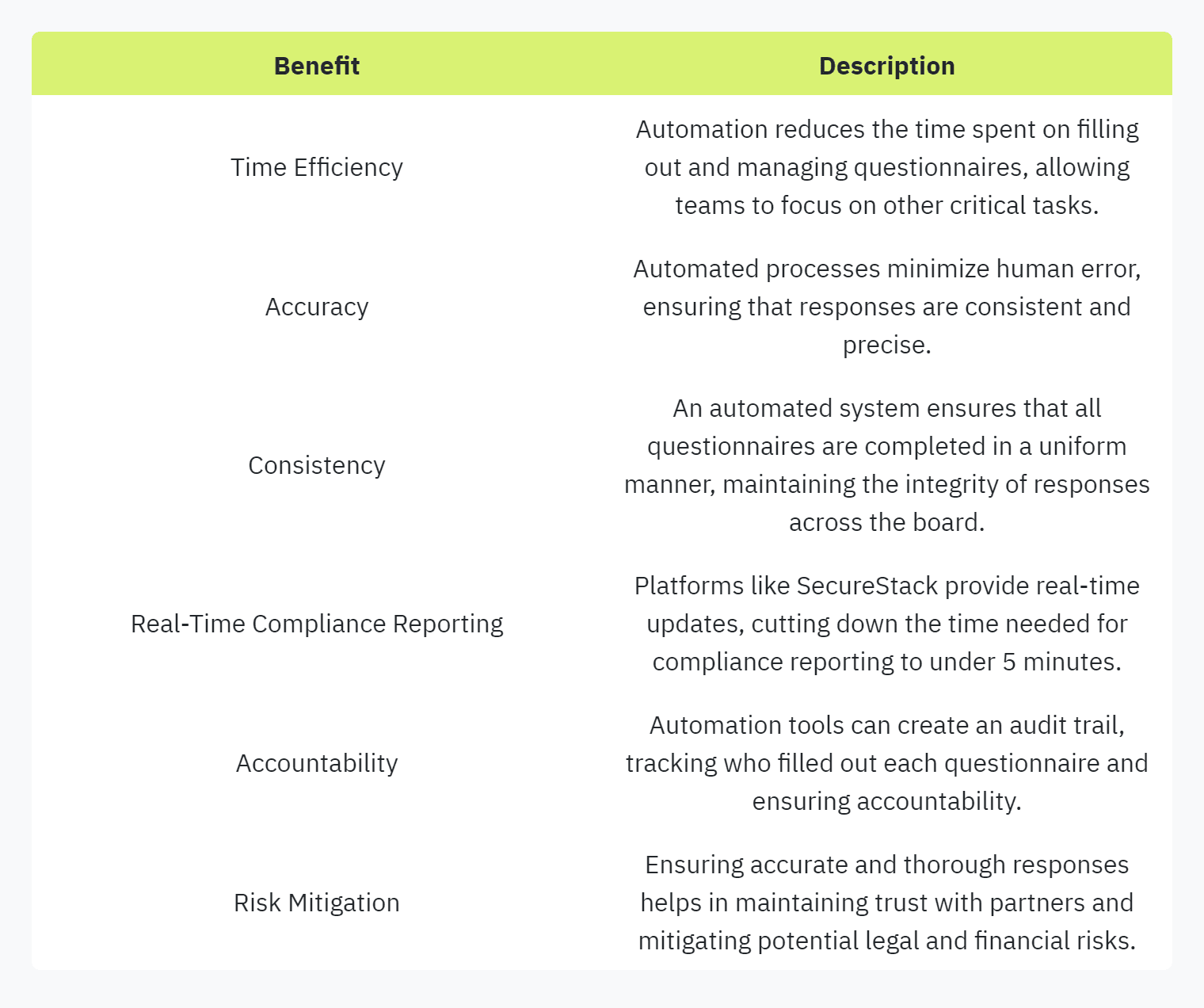
Benefits of Automated Questionnaire Processes
Automating the security questionnaire process can provide numerous benefits, especially given the increasing complexity and volume of assessments faced by organizations. Automation tools help streamline responses, improve accuracy, and significantly increase efficiency.
Tips for Efficient Responses
Implementing a streamlined and efficient response process for security questionnaires is essential. Here are some tips to enhance the efficiency and effectiveness of your assessments:
Establish an Intake Process: Develop a systematic approach for receiving and categorizing questionnaires. This process helps in organizing and prioritizing tasks effectively.
Build a Security Questionnaire Answer Library: Create a centralized repository of standard responses to common questions. This library can be referenced and reused, saving time and ensuring consistency.
Create a Trust Profile: Develop a trust profile that includes your organization’s security policies, certifications, and compliance status. This profile can be shared with vendors to address frequently asked questions.
Track Critical Metrics: Monitor key performance indicators such as response time, the number of questionnaires completed, and accuracy rates. Tracking these metrics helps in identifying areas for improvement.
Provide Required Documentation: Ensure that all necessary documentation and evidence are readily available to support your responses. This step helps in building credibility and meeting the questionnaire requirements.
Meet Deadlines: Timely submission of questionnaires is crucial. Set reminders and establish workflows to ensure that deadlines are met consistently.
Focus on Details and Be Honest: Pay attention to the details of each question and provide honest responses. Inaccurate or misleading information can damage trust and lead to compliance issues.
By following these tips and leveraging automation, organizations can enhance their security questionnaire processes, ensuring accuracy, efficiency, and trust in their vendor relationships. For further details on improving security questionnaire efficiency, visit our guide on streamlining security questionnaires. Additionally, explore our guide to automating security questionnaires for more insights into the benefits of automation.
Focus on SIG Questionnaires
When tackling third-party risk management, SIG questionnaires offer a comprehensive and structured approach to evaluate your vendors' security postures. Understanding these tools can significantly enhance the effectiveness of your cybersecurity and compliance efforts.
Overview of SIG and SIG Lite
The SIG (Standard Information Gathering) questionnaire, created by Shared Assessments, is designed to help organizations manage various risks such as cybersecurity, operational risks, business resiliency, and third-party risks within a Third-Party Risk Management (TPRM) program. This tool plays a critical role in [simplifying security questionnaire language] and streamlining assessments across multiple domains.
The SIG questionnaire comprises 21 risk domains in its Core version, including areas like data security, compliance, and privacy. The tool provides valuable insights into a vendor's security posture through customizable questionnaires tailored to specific vendor relationships.
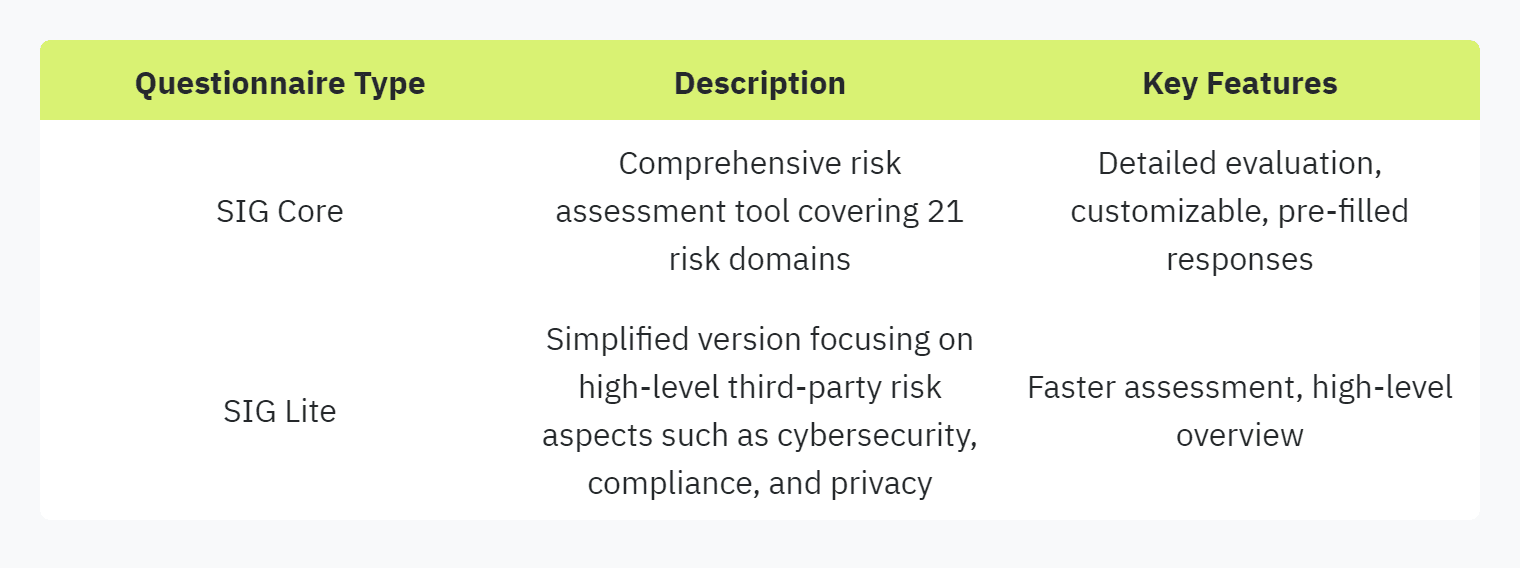
The SIG Lite questionnaire is a streamlined version of the SIG Core, focusing on core aspects of third-party risk. It's designed for quick assessments of vendor risk exposure, emphasizing key areas like cybersecurity, compliance, and privacy (UpGuard).
Structured Approach to Vendor Risk Management
One of the significant benefits of using SIG questionnaires is their structured approach to collecting third-party risk information. The process involves evaluating a vendor's security posture through various risk domains, ensuring comprehensive risk assessment.
The questionnaire is annually updated to align with industry standards and changes in the cybersecurity landscape. This ensures its relevance and effectiveness in managing third-party risks (UpGuard). Key updates include expanded privacy tools and additional risk domains, enhancing the depth and breadth of the assessments.
For security and compliance officers, IT managers, and SaaS startups, understanding the structured approach of SIG questionnaires can be invaluable. By leveraging tools like SIG and SIG Lite, organizations can improve their [vendor risk management] and overall cybersecurity posture. For more information on automating security questionnaires and improving efficiency in your processes, consider visiting our automating security questionnaire responses page.
These tools facilitate the collection, analysis, and management of third-party risk data, making it easier to [simplify security questionnaire language] and streamline the overall assessment process. To explore more about integrating SIG questionnaires into your risk management strategy, check out our guide on integrating security questionnaires.
Enter your email to start accelerating your sales today.















