Cutting down the time it takes to complete security questionnaires
Share This Article

Enhancing Cybersecurity Measures
In the ever-evolving landscape of cybersecurity, staying ahead of potential threats is paramount. Two key areas that security and compliance officers, IT managers, and SaaS startups should focus on are regular employee training and system and software updates.
Regular Employee Training
Regular employee training on cybersecurity measures is not just advisable; it's essential. Over 3.4 billion phishing emails are sent globally, serving as a common method for hackers to access secure databases.
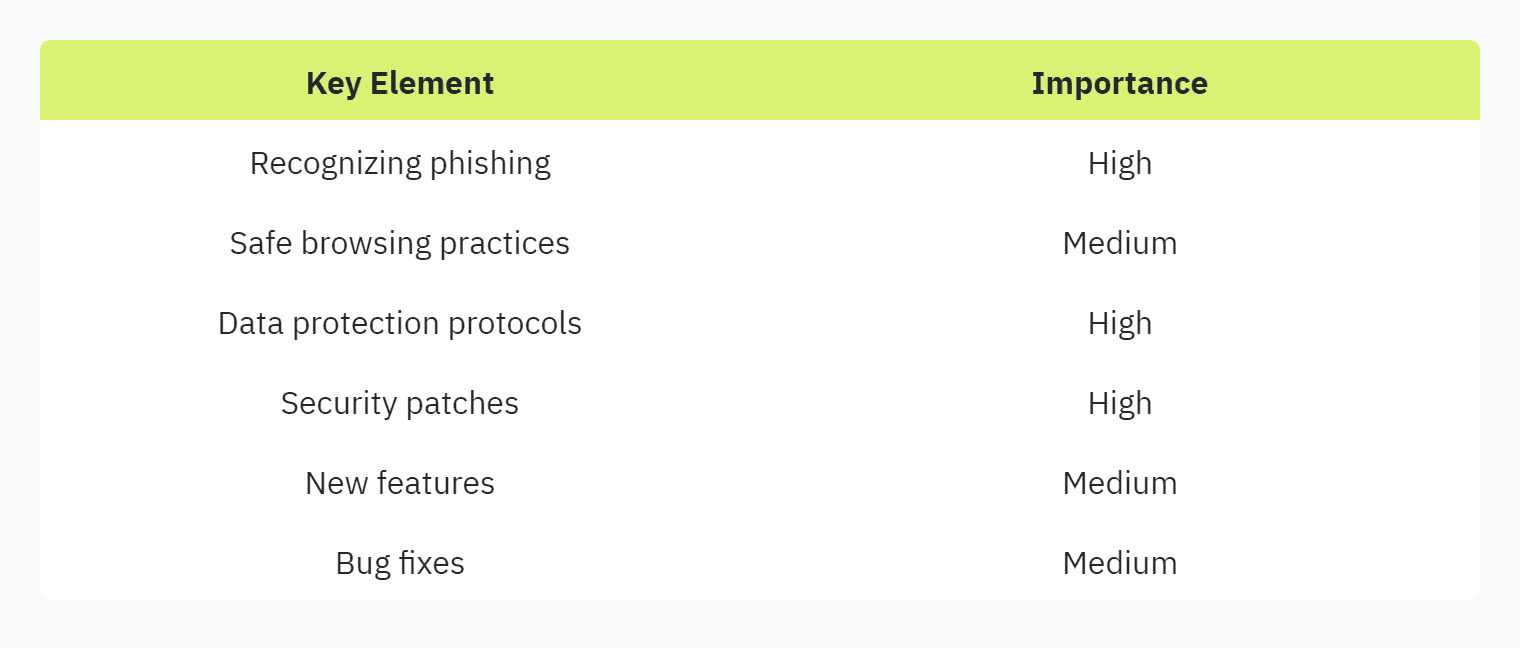
Employee training should encompass:
Recognizing phishing attempts: Simulated phishing exercises can help employees identify suspicious emails.
Safe browsing practices: Educating employees about secure websites and the risks of downloading content from untrusted sources.
Data protection protocols: Teaching employees best practices for handling sensitive data.
By regularly updating the training materials and incorporating the latest cybersecurity threats and trends, organizations can substantially reduce their vulnerability to attacks.
System and Software Updates
Keeping systems and software updated is crucial for enhancing cybersecurity. Updates serve multiple purposes: they fix bugs, add features, and, most importantly, patch security flaws that hackers can exploit.
The importance of regular updates includes:
Security patches: Immediate addressing of vulnerabilities significantly reduces the risk of exploitation.
New features and improvements: Better functionality can often provide additional layers of security.
Bug fixes: Ensuring smoother operation and reducing system crashes that could be exploited for malicious purposes.
A proactive approach to managing updates should include automated tools and scheduled check-ins to ensure no critical updates are missed.
For more information on why security questionnaires are crucial, visit our article on why security questionnaires are a nightmare or learn about tools to simplify security questionnaires to further secure your organization.
By focusing on regular employee training and ensuring system and software updates, organizations can create a robust cybersecurity framework that mitigates risks effectively.
Strengthening Password Practices
Strengthening password practices is crucial for any organization's cybersecurity strategy. This ensures the protection of sensitive information and helps in reducing the time to complete security questionnaires. Implementing complex passwords and multi-factor authentication (MFA) significantly mitigates risks associated with unauthorized access and data breaches.
Complex Passwords
Complex passwords are essential for safeguarding user accounts and sensitive data. Over 80% of organizational data breaches are caused by weak passwords. A strong password typically includes a mix of:
Upper and lower case letters
Numbers
Special characters

Organizations should enforce the use of complex passwords by setting stringent password policies and regular updates. Tools like password managers can assist in creating and storing unique passwords, thereby enhancing security.
For more on best practices, visit our article on best practices for security questionnaires.
Multi-Factor Authentication
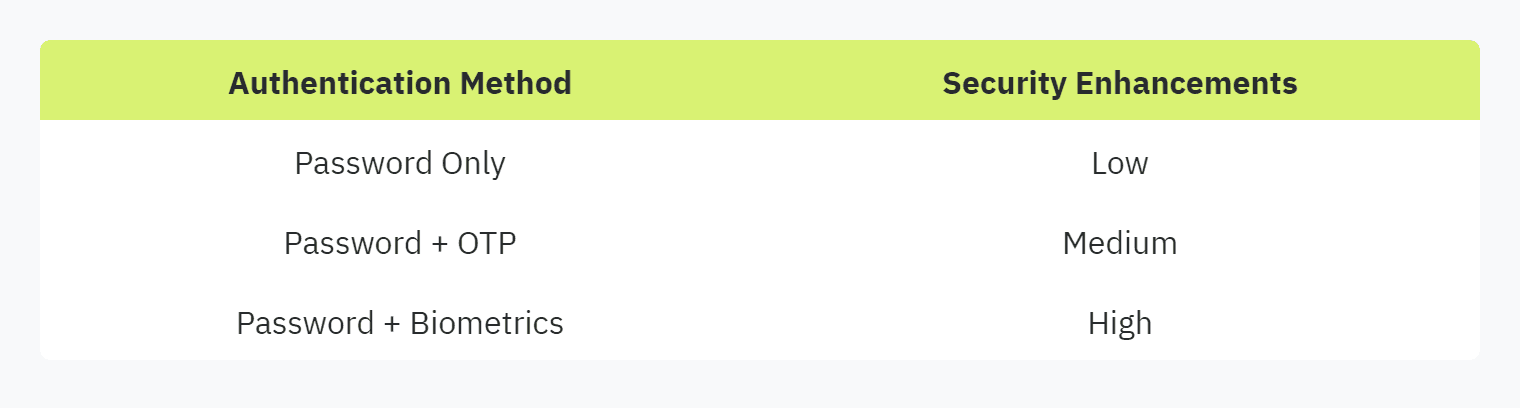
Multi-factor authentication adds an extra layer of security, requiring two or more verification methods:
Something you know (password)
Something you have (verification code)
Something you are (biometrics)
Using MFA significantly reduces the risk of unauthorized access, even if a password is compromised. This method is widely recognized as a secure practice for protecting sensitive information and is integral to cybersecurity risk mitigation (Hyperproof).
Implementing robust password practices and MFA not only strengthens security but also aids in the efficient completion of security questionnaires as part of automating security questionnaire responses.
For more detailed guidance on streamlining security questionnaires, check out our extensive resources on streamlining security questionnaires and automating security questionnaires.
Mitigating Third-Party Risks
When dealing with third-party vendors, it is essential to mitigate potential risks to maintain a robust cybersecurity posture. This involves effective vendor assessment strategies and thorough attack surface analysis.
Vendor Assessment Strategies
Conducting thorough vendor assessments plays a crucial role in reducing third-party risks. One effective approach is to establish a centralized, coordinated system for third-party evaluations. Assessing vendors in isolation across departments can lead to confusion, overlapping requests, and a lack of comprehensive understanding of supplier risk (3rdRisk).
By utilizing industry best practices in security questionnaires, organizations can streamline the process and ensure consistent data. Adhering to common frameworks like ISO 27001, NIST, or CIS and referencing these frameworks in questionnaires can significantly enhance the efficiency and precision of responses.
Implementing tools like Vanta’s Questionnaire Automation can further streamline the process. This tool allows software companies to save time and resources by automating the completion of security questionnaires. This approach not only increases the accuracy and completeness of responses but also facilitates a more efficient assessment process (Vanta). For a deeper dive into automating these processes, check out our article on automating security questionnaires.
Attack Surface Analysis
Another key aspect of mitigating third-party risks is conducting a comprehensive attack surface analysis. This involves identifying and quantifying the points of potential exposure to cybersecurity threats stemming from third-party vendors. Attack surface analysis helps in ensuring that all vulnerabilities are accounted for and properly managed.
Implementing a centralized system for attack surface analysis can help streamline the process and improve accuracy. This approach ensures that all third-party interactions are tracked and evaluated consistently, preventing gaps that could be exploited by cyber attackers. For more on this, you may refer to our article on automating vendor security assessments.
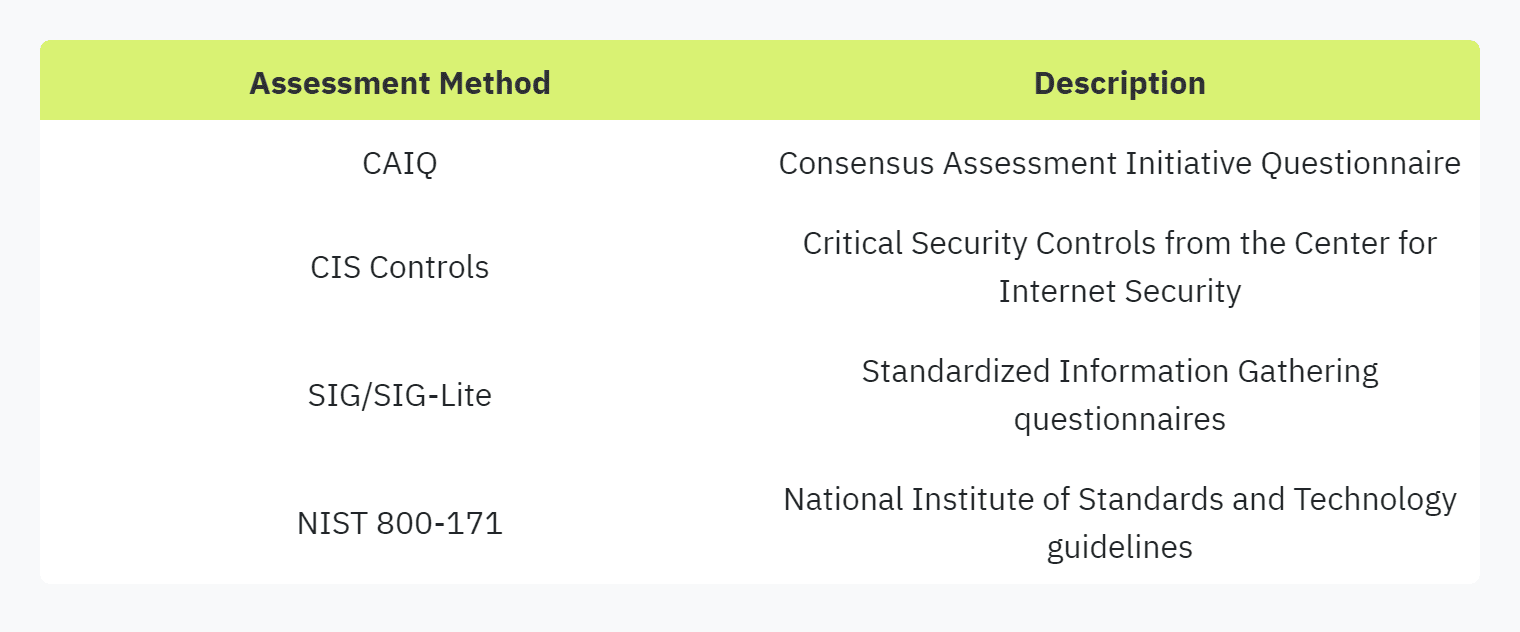
Engaging in industry-standard security assessment methodologies is crucial for effective attack surface analysis. Utilizing comprehensive frameworks such as CAIQ, CIS Critical Security Controls, SIG/SIG-Lite, and NIST 800-171 helps organizations in effectively managing vendor risks as part of the procurement process.
By integrating vendor assessment strategies and attack surface analysis, organizations can significantly enhance their approach to mitigating third-party risks. This, in turn, leads to more efficient and effective completion of security questionnaires, supporting the overall goal of reducing time to complete security questionnaires.
Streamlining Security Questionnaires
Security questionnaires can often be time-consuming and complex. Here are some strategies to simplify and tailor these questionnaires effectively.
Simplification Techniques
To reduce the time it takes to complete security questionnaires, several techniques can be employed. One way is to simplify the questionnaire by focusing on the critical aspects of security. By emphasizing essential questions, respondents are less likely to experience fatigue.
Focus on Critical Aspects: Prioritize questions that address the most significant security concerns. Avoid unnecessary details that can overwhelm respondents.
Use Closed Questions: Closed questions that require a simple yes or no answer can expedite the response process. This reduces ambiguity and ensures clear, concise answers.
Implement Automation Tools: Utilize automation and software tools to streamline the questionnaire process. Tools like Vanta’s automated compliance software can simplify compliance efforts and ensure accuracy. For more on this, explore tools to simplify security questionnaires.
Structured Questionnaires: Use a structured format to organize questions logically. This helps respondents navigate the questionnaire more efficiently.
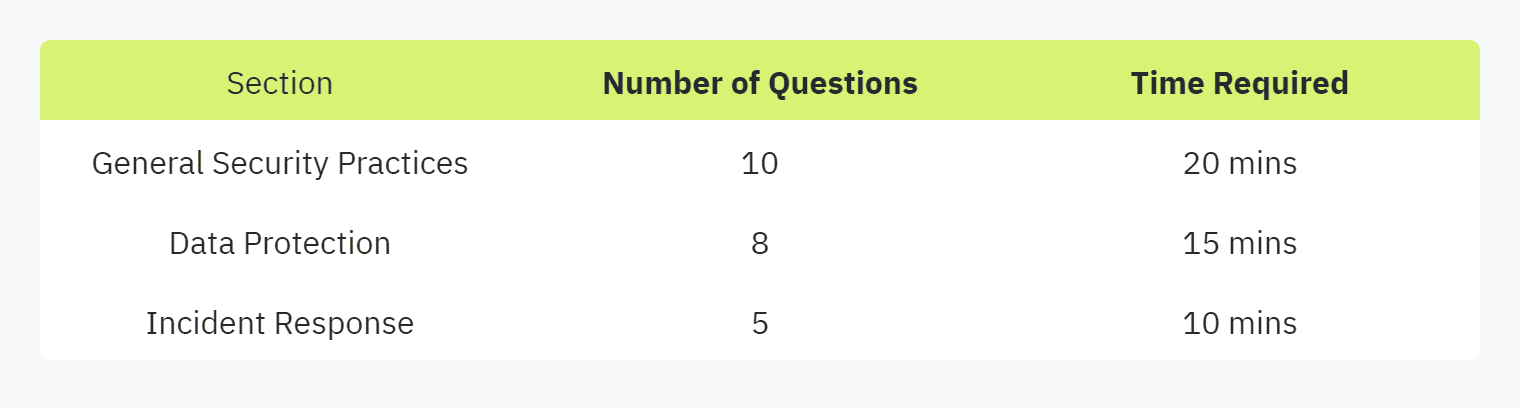
Example of a Simplified Questionnaire Structure:
For more guidelines, refer to best practices for security questionnaires.
Tailoring Questionnaires
A one-size-fits-all approach does not work for security questionnaires. Tailoring the questionnaire to the specific needs and risk profiles of different vendors can make the process more effective and relevant.
Risk-Based Questionnaire: Develop questionnaires based on the risk level of each vendor. Higher-risk vendors should undergo more detailed assessments, whereas lower-risk vendors can be assessed with a basic questionnaire (3rdRisk).
Tiered Questionnaires: Implement tiered questionnaires to categorize vendors. This method involves varying levels of detail based on the vendor's importance and the sensitivity of the information they handle.
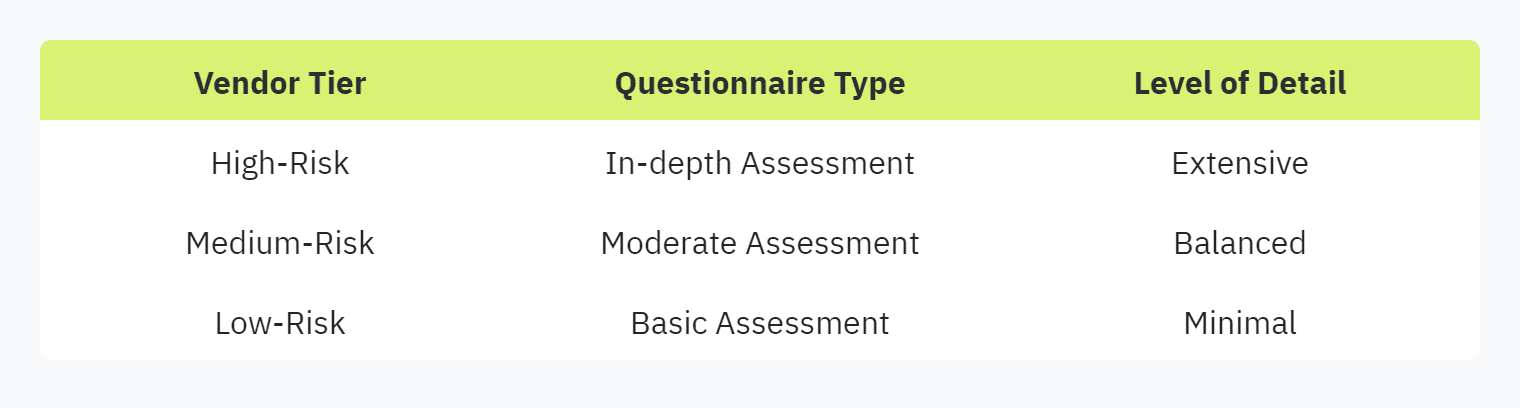
Industry Standards: Use industry-standard methodologies such as CAIQ, CIS Critical Security Controls, SIG/SIG-Lite, and NIST 800-171 to design questions that are comprehensive and universally recognized (Hyperproof). These standards help maintain consistency and reliability in the assessment process.
By incorporating these simplification and tailoring techniques, security officers and IT managers can significantly reduce the time it takes to complete security questionnaires while ensuring thorough and accurate assessments. For additional strategies, check out our detailed guide on streamlining security questionnaires.
Enter your email to start accelerating your sales today.
















