Improving the experience of filling out security questionnaires
Share This Article

Enhancing Security Questionnaire Responses
Understanding Security Questionnaires
Security questionnaires serve as a bridge for businesses to share and evaluate security information. They are integral to assessing security postures, compliance, and risk management in vendor relationships. However, their traditional format can be lengthy, complex, and overwhelming for vendors. Understanding the intricacies of these questionnaires is the first step toward improving the response experience.
A security questionnaire typically includes sections on:
Security Frameworks and Policies
Data Protection Measures
Compliance with Regulations
Incident Response Plans
Access Controls
Given their importance, it's crucial for organizations to fill them out accurately. However, the manual process can be arduous, error-prone, and resource-intensive Vendict.
For those new to this process, our article on understanding security questionnaires can offer deeper insights into their structure and purpose.
Importance of Questionnaire Automation
Automation is becoming a cornerstone in modern security questionnaire processes. By leveraging tools and technologies, organizations can streamline the process, ensuring efficiency and accuracy. Automation addresses several critical challenges:
Efficiency: Automated tools can process questionnaires up to 50 times faster than traditional methods Vendict.
Accuracy: Utilizing technologies like Natural Language Processing (NLP), automation ensures precise and consistent answers, minimizing human error.
Risk Management: Automation proactively prevents potential risks by maintaining high standards of accuracy and consistency.
Here's a comparison of manual versus automated processes:
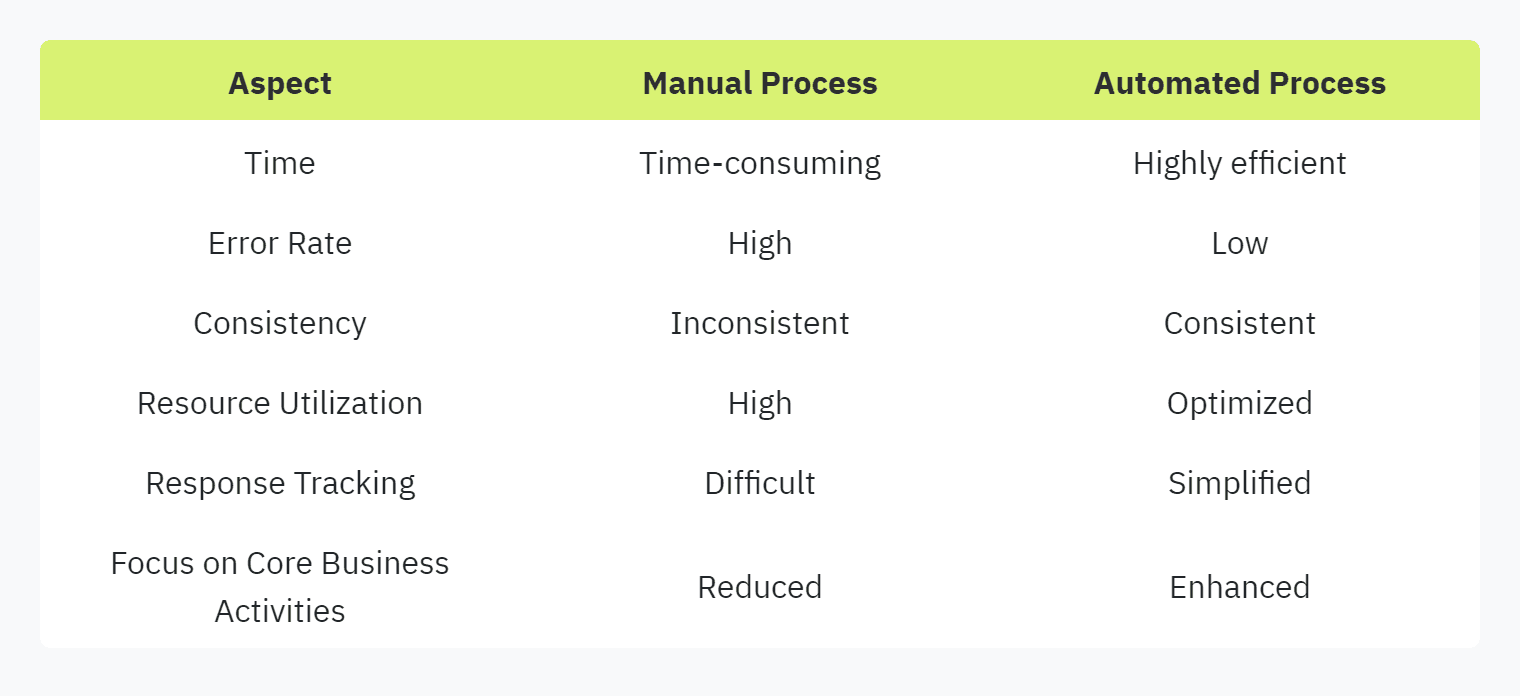
Adopting automation can transform the experience of filling out security questionnaires, allowing security and compliance officers, IT managers, and SaaS startups to reap significant benefits Vendict.
For practical advice on selecting and using these tools, explore our guide to automating security questionnaires.
By automating security questionnaires, organizations can not only improve efficiency and accuracy but also fortify their risk management strategies. This shift underscores the broader trend toward leveraging technology to solve complex compliance and security challenges. For more information on the benefits and best practices, please refer to automating security questionnaires.
Challenges in Manual Questionnaire Filling
Manually filling out security questionnaires presents several challenges for [security and compliance officers], IT managers, and SaaS startups. This section will delve into the main obstacles encountered in this process.
Time-Consuming Process
Manual completion of security questionnaires can be incredibly time-consuming. According to Vendict, the process is resource-intensive and requires significant investment in both time and human resources.
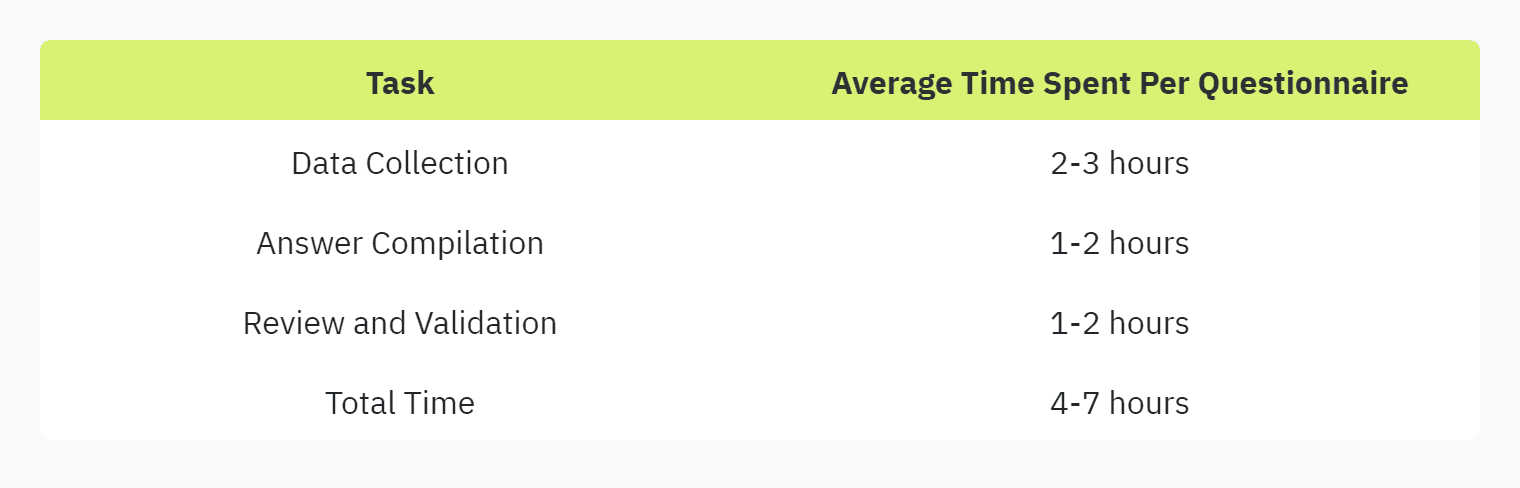
This extensive time commitment can lead to increased job-related stress, especially among audit firm personnel who often face stringent time pressures. Protecht Group highlights that streamlining processes like manual questionnaire filling can significantly alleviate this stress, freeing up valuable time for other critical tasks.
Prone to Errors and Inconsistencies
Manual processes are inherently prone to human error and inconsistencies. Varying interpretations of questions can lead to discrepancies in the responses. This issue is well-documented by the OneTrust blog, which points out that answers may differ based on individual understanding, compromising the uniformity and reliability of the data.
Moreover, the tedious nature of manually filling out these questionnaires often leads to mistakes, further undermining the integrity of the responses. The W3C Security and Privacy Questionnaire highlights that the manual process can introduce errors and inconsistencies, which can compromise accuracy and reliability.
For organizations looking to enhance data integrity and streamline their questionnaire processes, automation presents a viable solution. For more insights into dealing with these common frustrations, refer to common frustrations with security questionnaires.
Benefits of Security Questionnaire Automation
Automating security questionnaires offers compelling benefits. This process ensures the efficient handling of security-related inquiries, accuracy in responses, and effective risk management.
Efficiency and Accuracy
Filling out security questionnaires manually can be a labor-intensive and error-prone task (Vendict). Automation streamlines this process, significantly reducing the time required to complete each questionnaire.
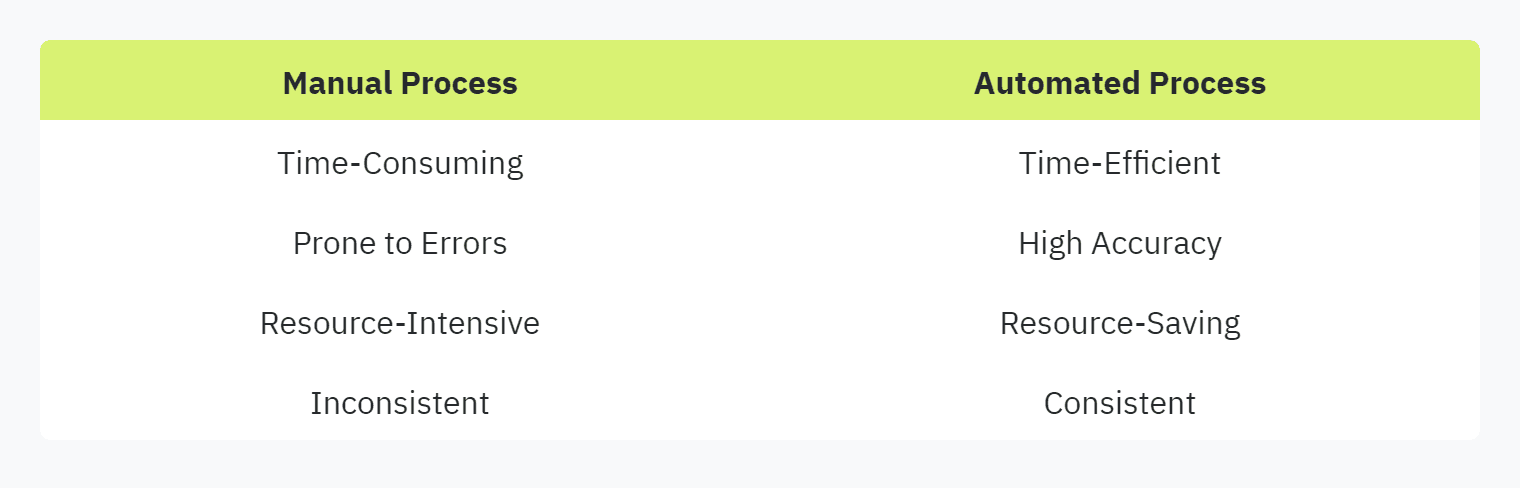
Automated solutions ensure responses are accurate and consistent across all forms, reducing the chance of human error. By leveraging pre-populated answers and an extensive database of common questions, organizations can ensure that responses are both detailed and consistent.
For more on reducing the time to complete security questionnaires, visit reducing time to complete security questionnaires.
Risk Prevention and Management
Implementing automation in security questionnaires is crucial for robust risk management. Automation acts as a safeguard, ensuring all data provided is consistent and reliable (Vendict). This consistency helps in mitigating potential risks associated with inaccurate or incomplete data.
A well-structured risk culture within an organization ensures everyone understands what is 'right' and 'wrong' in terms of security practices. Automating the questionnaire process aligns with this culture by reinforcing accurate and reliable data handling.
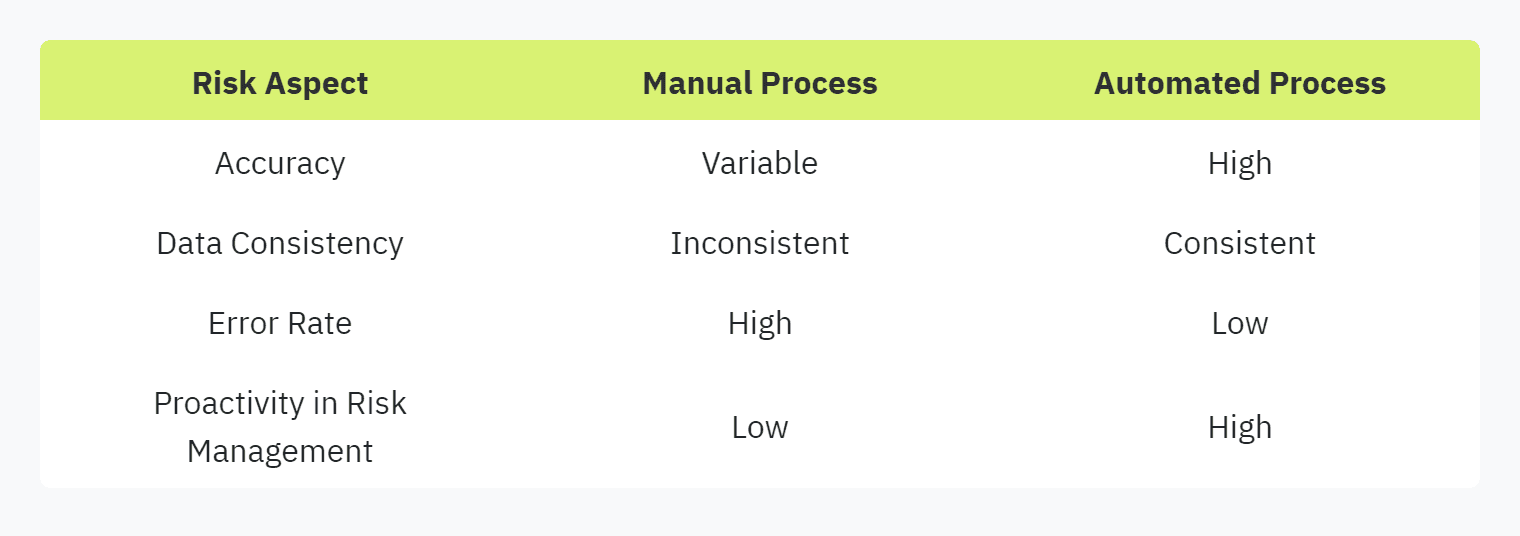
By utilizing automation tools to handle security questionnaires, organizations can better manage and prevent risks. This approach supports the overall goal of maintaining a secure and compliant environment. Learn more about automating security questionnaires by visiting automating security questionnaires.
Incorporating automation in security processes not only enhances efficiency and accuracy but also significantly contributes to effective risk management, making it an essential practice for organizations focused on improving their security posture. Explore how this can be achieved through our guide to automating security questionnaires.
Best Practices for Security Questionnaire Responses
Customizing Security Frameworks
To effectively respond to security questionnaires, organizations need to customize their security frameworks. Rather than relying solely on common standards, it's crucial to assess vendors based on their unique access levels to internal systems and data. Customization ensures that the evaluation is relevant and comprehensive, covering the critical security dimensions such as Information Security Policies and Procedures, Security Controls and Safeguards, Data Privacy and Compliance, and Incident Response and Breach Notification.
Customizing your framework involves:
Identifying Core Security Areas: Focus on key areas that align with your organizational priorities and regulatory requirements.
Tailoring Questions: Develop questions specific to the security practices and controls pertinent to your industry.
Avoiding Irrelevant Queries: Streamline the process by eliminating unnecessary questions. For instance, Cloud SaaS solutions hosted on major providers like AWS, GCP, or Azure should not be treated like licensed software (Vendict).
Regular Updates: Continuously refine and update your questionnaires to reflect the latest security threats and compliance requirements.
For a thorough understanding of customizing security frameworks, visit our detailed guide on best practices for security questionnaires.
Leveraging Automation Tools
Automating security questionnaire responses significantly improves efficiency and accuracy. Leveraging advanced tools like Vendict's automation solution, which uses Natural Language Processing (NLP), can transform the process, completing tasks 50 times faster than manual methods (Vendict). These tools ensure precise and accurate answers, freeing up valuable time for security and compliance officers to focus on core business tasks while maintaining robust security measures.
Table: Benefits of Automation Tools
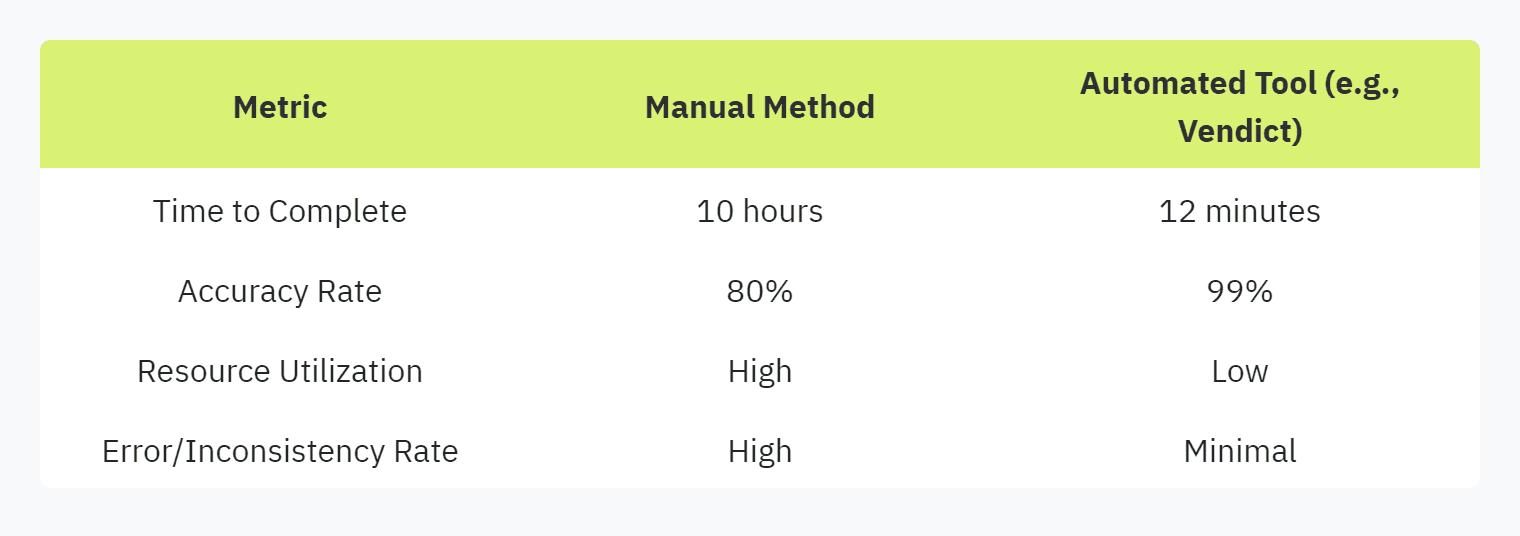
When selecting and implementing automation tools, consider the following best practices:
Choose the Right Tool: Select an automation tool that integrates well with your existing systems and meets your specific needs.
Training and Adoption: Provide adequate training for your team to effectively use the tool and maximize its potential (training for security questionnaire automation).
Measure ROI: Track key metrics to evaluate the return on investment of the automation tool (measuring roi of security questionnaire automation).
Continuous Feedback: Establish feedback loops to continually improve the tool's performance and update the questionnaire template based on real-world insights (feedback loops in security questionnaires).
Automation tools not only enhance the overall process of security questionnaires but also help in reducing time to complete security questionnaires.
By adhering to these best practices—customizing security frameworks and leveraging automation tools—organizations can greatly improve the experience of filling out security questionnaires, ensuring efficiency, accuracy, and comprehensive risk management. For further reading, explore our articles on automating security questionnaires and tools to simplify security questionnaires.
Enter your email to start accelerating your sales today.
















