Key metrics to track for successful security questionnaire automation
Share This Article

Importance of Security Questionnaire Automation
Enhancing Efficiency and Compliance
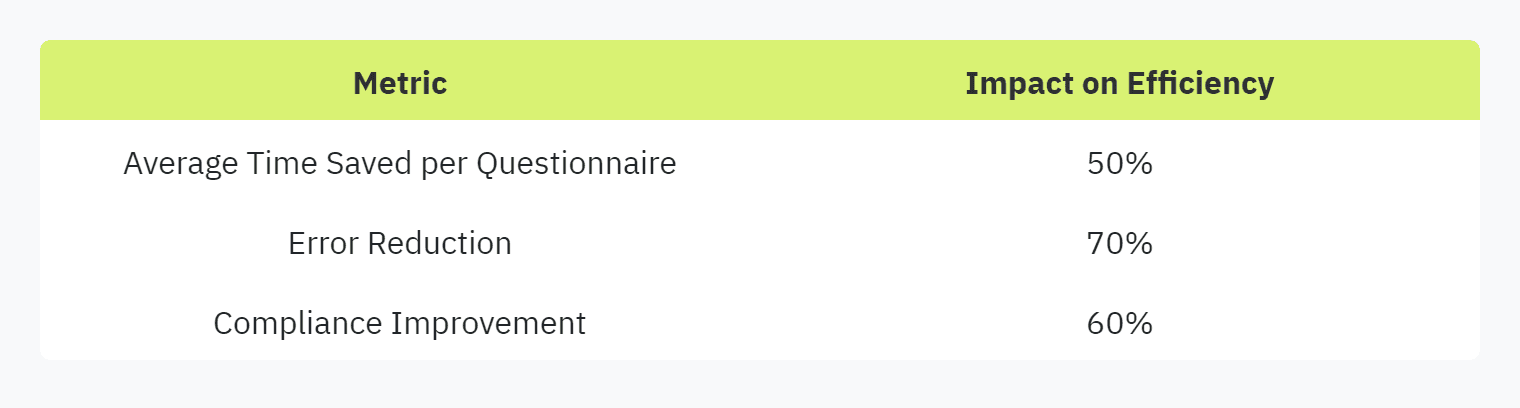
Security questionnaire automation plays a critical role in enhancing both efficiency and compliance within organizations. Completing security questionnaires can be a tedious and time-consuming task, often requiring significant resources. Automation tools, such as Vanta's Questionnaire Automation, allow vendors to quickly and accurately answer security questionnaires in minutes. This streamlines the process that historically required substantial time and effort from software companies (Vanta's Questionnaire Automation).
One of the key advantages of automation is the auto-fill feature, which saves valuable time by utilizing accurate and up-to-date information from previous responses. This feature not only accelerates the completion process but also reduces the chances of errors and inconsistencies, enhancing compliance efforts. With the ability to sync with policies and documents, automation tools ensure teams have access to the most recent information, further improving accuracy and compliance (Vanta's Questionnaire Automation).
Streamlining the questionnaire completion process also frees up resources that can be allocated towards security program development. It reduces the administrative burden on security and compliance officers, allowing them to focus on critical tasks. To explore more about reducing time spent on security questionnaires, visit our article on reducing time to complete security questionnaires.
Impact on Security Practices
Automation in security questionnaires not only boosts efficiency but also significantly impacts security practices. By ensuring that the information provided in questionnaires is accurate and up-to-date, automation tools mitigate the risks associated with outdated or incorrect data. This proactive approach to risk management strengthens the overall security posture of organizations.
Syncing information automatically with policies and documents ensures that teams are always prepared with the latest data when completing security questionnaires. This constant access to current information helps maintain high standards of security and compliance, reducing potential vulnerabilities (Vanta's Questionnaire Automation).
In addition to its direct impact on security practices, automation fosters a culture of continuous improvement. With reduced time and effort needed for questionnaire completion, organizations can invest more in enhancing their security measures and staying ahead of emerging threats. Learn more about continuous enhancement in security questionnaires by visiting our article on continuous improvement in security questionnaires.
The following table highlights the enhanced security metrics achieved through automation:

For more detailed insights on how automation influences security measures, check out our guide on automating security questionnaires.
In summary, the automation of security questionnaires is vital for boosting efficiency, ensuring compliance, and enhancing overall security practices within organizations. By leveraging advanced tools and technologies, businesses can streamline their questionnaire completion process, reduce risks, and focus on continuous security improvements. Explore our extensive resources to understand more about the benefits and implementation of security questionnaire automation.
Metrics for Assessing Security Questionnaire Automation
Tracking the right metrics is essential for evaluating the success of security questionnaire automation. Key metrics such as deployment frequency, vulnerability patch time, percentage code automatically tested, and automated tests per application provide valuable insights into the efficiency and effectiveness of automated security practices.
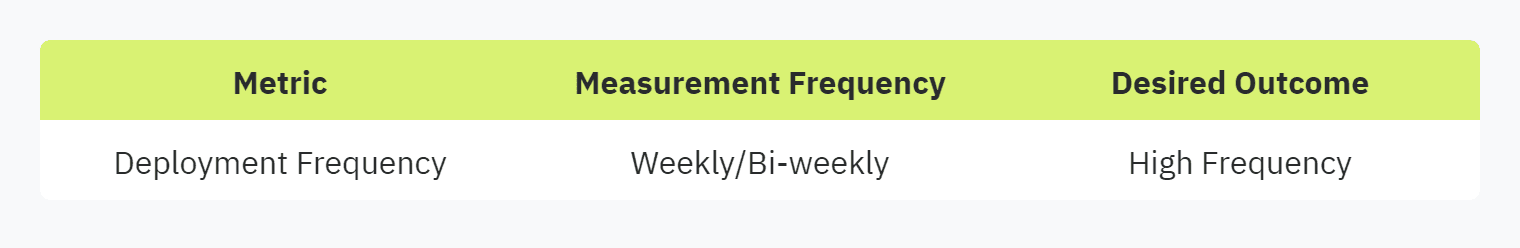
Deployment Frequency
Deployment frequency measures how often updates and changes are deployed to production. In the context of security questionnaire automation, frequent deployments indicate an agile and responsive system capable of adapting to new threats and regulatory requirements swiftly. Monitoring deployment frequency helps security teams enhance efficiency and improve software quality through continuous integration and delivery practices.
For more on streamlining security processes, see our article on reducing time to complete security questionnaires.
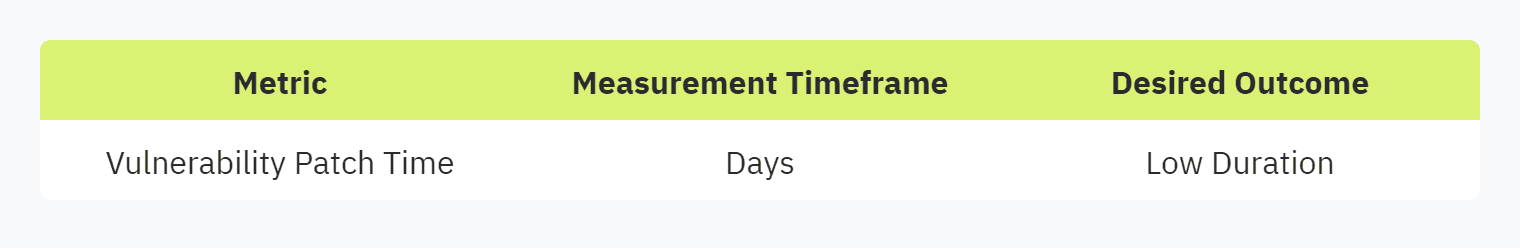
Vulnerability Patch Time
Vulnerability patch time tracks the duration between the discovery of a security vulnerability and the deployment of a patch to mitigate it. A shorter patch time reflects a robust and responsive security framework, essential for preventing potential breaches. Efficient patch management is critical in maintaining compliance and protecting sensitive data.
Read more about common frustrations with security questionnaires to understand the impact of vulnerabilities.
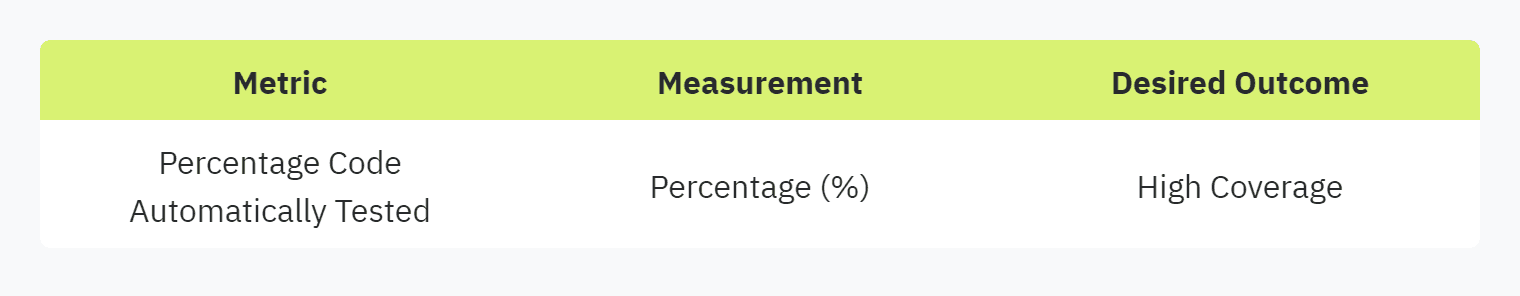
Percentage Code Automatically Tested
Automated code testing is a cornerstone of reliable security practices. This metric indicates the proportion of the codebase covered by automated tests and is crucial for early detection of security issues. A higher percentage ensures comprehensive testing, reducing the likelihood of undetected vulnerabilities reaching production.
For further insights on code testing, explore automating security questionnaire responses.
Automated Tests per Application
This metric measures the number of automated tests employed per application. A higher number of automated tests signify thorough validation and robust security controls. Automated tests per application help in maintaining the integrity and security of each system component, providing a reliable defense mechanism against security threats.
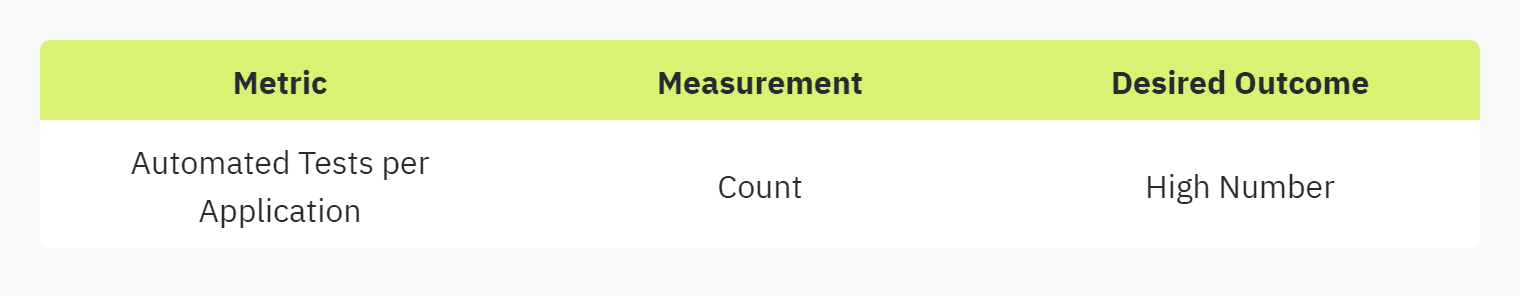
Understanding the granular details of automated tests is essential. For best practices, refer to best practices for security questionnaires.
Monitoring these key metrics ensures that security questionnaire automation initiatives are not only effective but also continuously improving. By emphasizing metrics such as deployment frequency, vulnerability patch time, percentage code automatically tested, and automated tests per application, organizations can achieve significant gains in security efficiency and compliance. For additional insights and tools, consider exploring our resources on ai in security questionnaires and automating vendor security assessments.
Tools and Technologies for Security Questionnaire Automation
To harness the full potential of security questionnaire automation, it’s essential to integrate several tools and technologies. These can streamline processes, enhance security measures, and ensure compliance.
Password Managers and Antivirus Software
Password managers and antivirus software play a pivotal role in maintaining the security of automated systems. Antivirus solutions are crucial for detecting and blocking malware attacks, safeguarding systems from threats like viruses, spyware, and bots (Vanta). Password managers help in managing and protecting login credentials, ensuring that sensitive information is securely stored and inaccessible to unauthorized users.
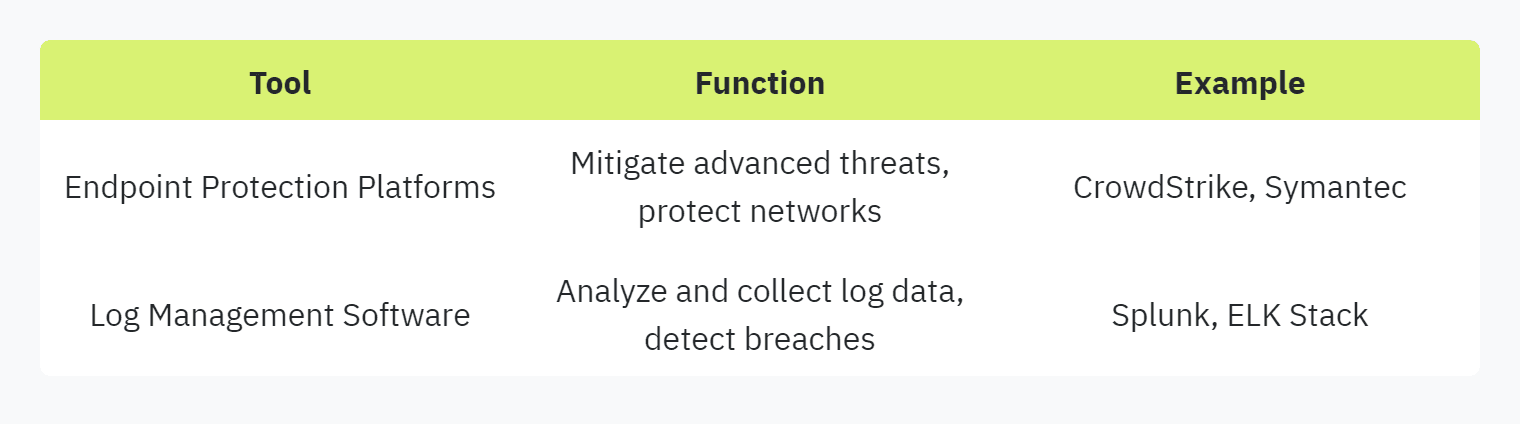
Endpoint Protection Platforms and Log Management Software
Endpoint Protection Platforms (EPP) are indispensable for organizations aiming to protect their network integrity. They provide a cloud-based management system that mitigates advanced threats, recognizing and neutralizing malware before it causes damage. Log management software, on the other hand, collects and analyzes log data from various sources within the organization. This data can be pivotal in detecting security breaches and ensuring compliance.
Mobile-Device Management (MDM) Software
With the rise of remote work, Mobile-Device Management (MDM) software has become increasingly important. MDM tools help organizations safeguard and monitor all mobile devices, ensuring that data and applications on these devices are protected from security risks. This is especially critical for companies with employees working from various locations, as it helps maintain the integrity and security of corporate data.
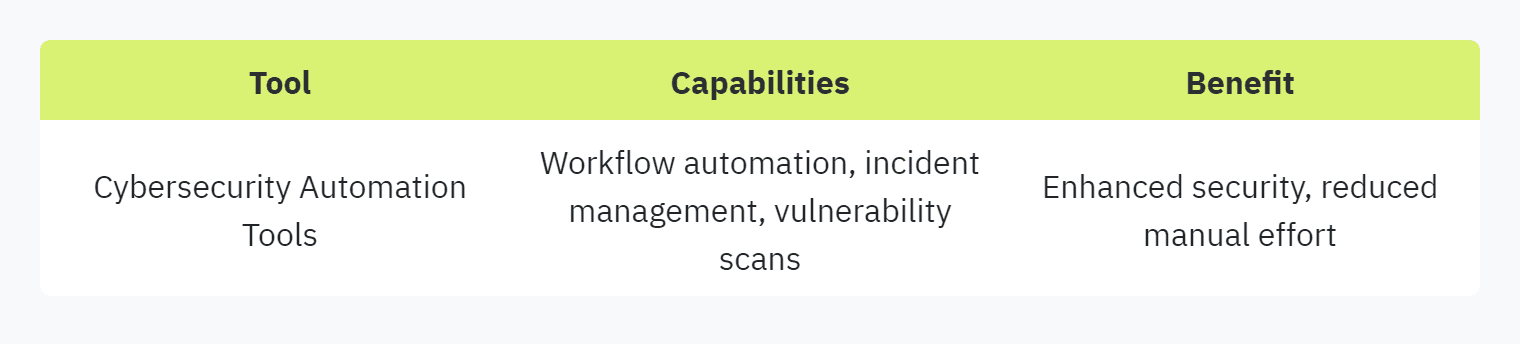
Cybersecurity Automation Tools
Cybersecurity automation tools leverage machine learning and AI to enhance security operations management. These tools offer capabilities such as workflow automation, incident management, compliance automation, and vulnerability scans. Astra Security, for instance, provides automated penetration testing software that uses AI to conduct extensive tests and compliance checks efficiently, ensuring cost savings and operational effectiveness (Sprinto Blog).
Implementing these tools and technologies is a strategic step towards achieving successful security questionnaire automation. By integrating them into the existing system, organizations can significantly improve security measures, streamline processes, and achieve better compliance. For more insights, refer to articles on tools to simplify security questionnaires and streamlining security questionnaires.
Best Practices for Implementing Security Questionnaire Automation
Implementing security questionnaire automation brings efficiency, accuracy, and swiftness to an otherwise resource-intensive process. Below are some best practices to help you leverage this technology effectively.
Centralized Answer Library and Documentation
Creating a centralized answer library is pivotal. This library should store common answers to frequently asked questions, improving the speed and consistency of responses. A comprehensive documentation process aids in maintaining up-to-date and accurate information.
Benefits:
Reduced response time
Consistency in answers
Easy access for the team
For more details on simplifying these processes, explore automating security questionnaires.
Engagement with Key Stakeholders
Involving key stakeholders is crucial for the successful implementation of security questionnaire automation. This includes security officers, IT managers, and compliance officers. Their input can identify potential pitfalls and areas for improvement.
Engagement Activities:
Regular meetings for feedback
Collaborative workshops
Training sessions
Refer to collaboration in security questionnaires for more insights on involving stakeholders effectively.
Streamlining Request Intake Process
Streamlining the request intake process ensures that incoming questionnaires are handled promptly and efficiently. This step involves setting up an organized and standardized way to receive and categorize questionnaires.
Methods:
Using intake forms
Categorizing by urgency and complexity
Automated routing to appropriate teams
Learn about reducing processing time in our article on reducing time to complete security questionnaires.
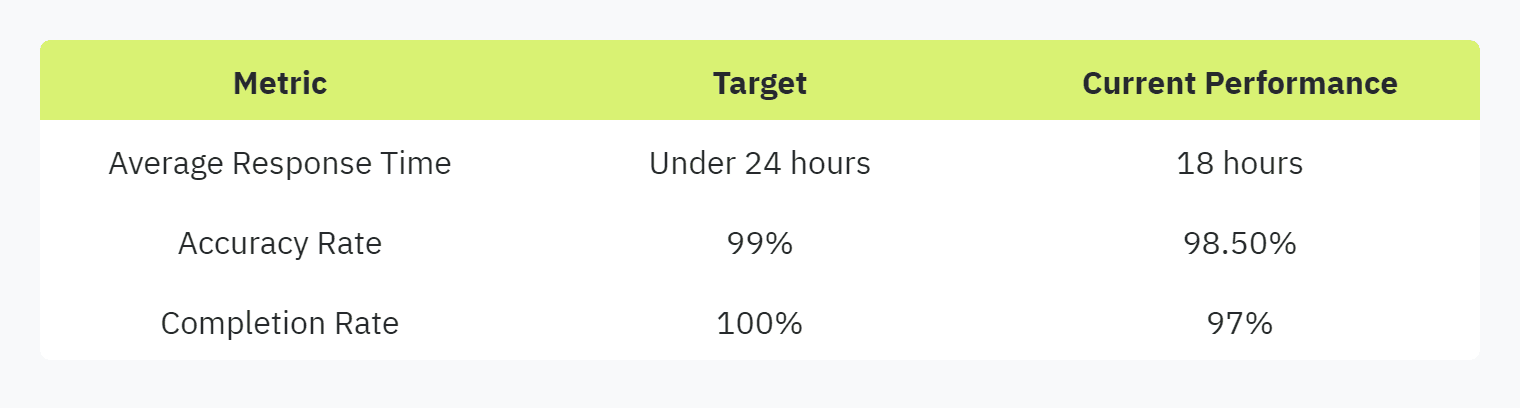
Setting Performance Goals
Setting clear performance goals helps track progress and measure the effectiveness of your security questionnaire automation. Establish metrics like response time, accuracy, and completion rates.
Performance Metrics:
Average response time
Percentage of accurate responses
Questionnaire completion rate
To delve deeper into measuring success, read our article on measuring ROI of security questionnaire automation.
Key Metrics Table
A well-structured table helps visualize critical performance indicators for your operations.
By following these best practices, security and compliance officers, IT managers, and SaaS startups can optimize their security questionnaire processes for better efficiency and reliability. For further reading, check out our guide on best practices for security questionnaires.
Enter your email to start accelerating your sales today.















