How automation can help with compliance in security questionnaires
Share This Article

Understanding Security Questionnaires
In the realm of vendor risk management, security questionnaires play a pivotal role. They help organizations evaluate the security measures of potential partners, ensuring that these partners do not present a risk to data integrity and compliance standards. This section explores the significance of security assessments and the common compliance topics they cover.
Importance of Security Assessments
Security assessments are essential for safeguarding an organization's data and ensuring that third-party vendors adhere to stringent security protocols. With 2 out of 3 companies requiring proof of safety compliance from their software vendors (Responsive), it is clear that security questionnaires are a critical component of the vendor selection process. These assessments help organizations understand the risks posed by potential vendors and make informed decisions about third-party partnerships (Hyperproof).
Security questionnaires are designed to evaluate a vendor's security posture before engagement. They facilitate secure data and information exchanges between organizations, ensuring sustainable partnerships in a digital enterprise landscape (SecurityPal Blog). These evaluations often include inquiries about vulnerability scans, penetration tests, and external audits such as SOC 2 Type I or Type II.
Common Compliance Topics
Security questionnaires cover a wide array of compliance topics to assess the adequacy of a vendor's security measures. Below is a table detailing some of the most common compliance frameworks and standards that these questionnaires address:
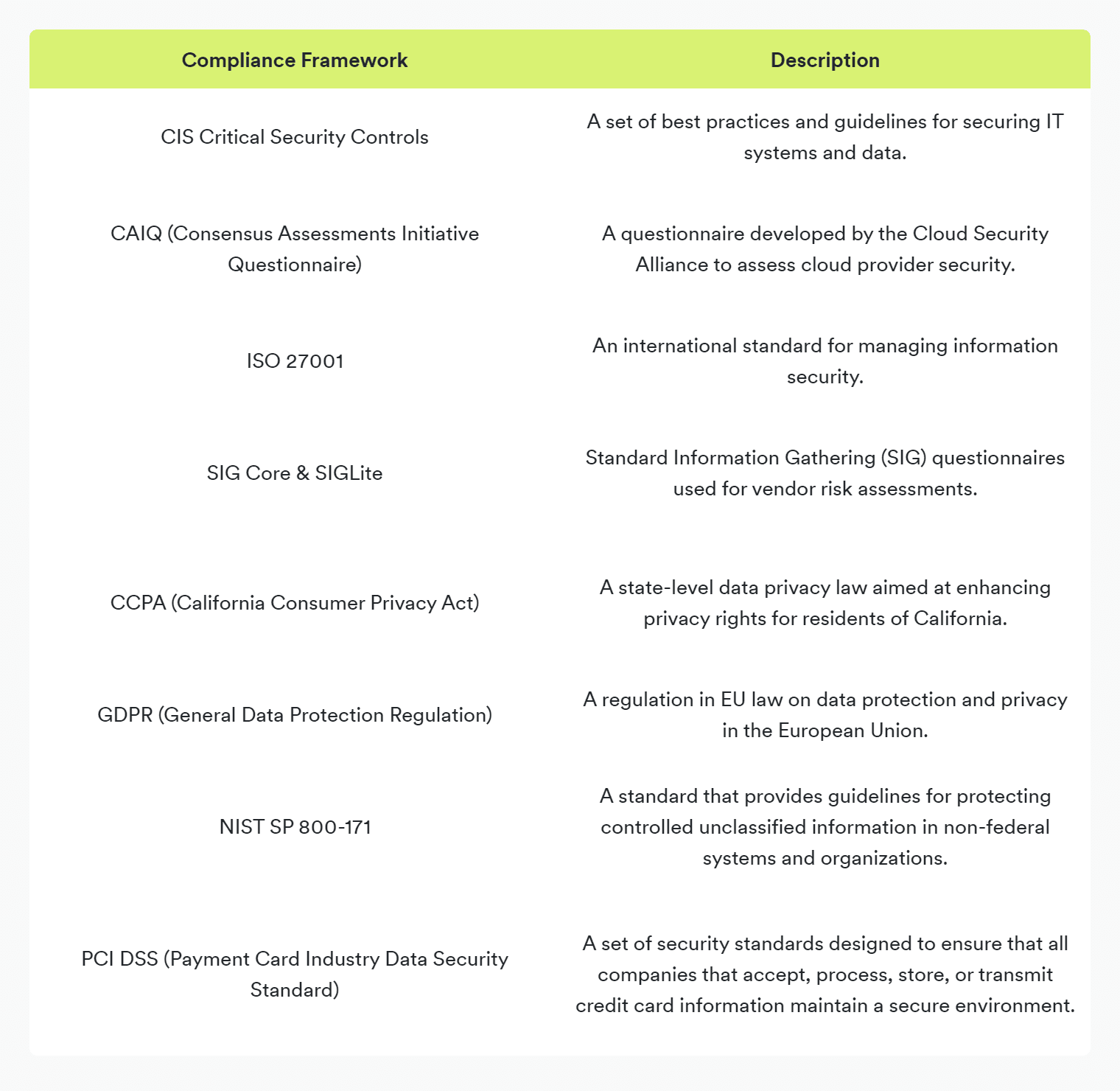
By leveraging these comprehensive questionnaires, organizations can perform precise vendor risk assessments and ensure that their partners are equipped with the necessary security safeguards to protect sensitive information. For further insights into managing security questionnaires efficiently and effectively, refer to our best practices for security questionnaires.
Challenges in Security Questionnaires
Security questionnaires play an essential role in assessing an organization's security posture, but they also come with significant challenges. Among these, time and resource constraints and the impact on business deals stand out as critical issues.
Time and Resource Constraints
Answering security questionnaires manually can be both time-consuming and labor-intensive. Information Security (IS) teams often spend several weeks completing these questionnaires, making the process difficult to sustain, especially given the constantly evolving information security landscape (SecurityPal Blog). For instance, a report by Whistic shows that salespeople spend an average of 6.8 hours per month answering security questionnaires.
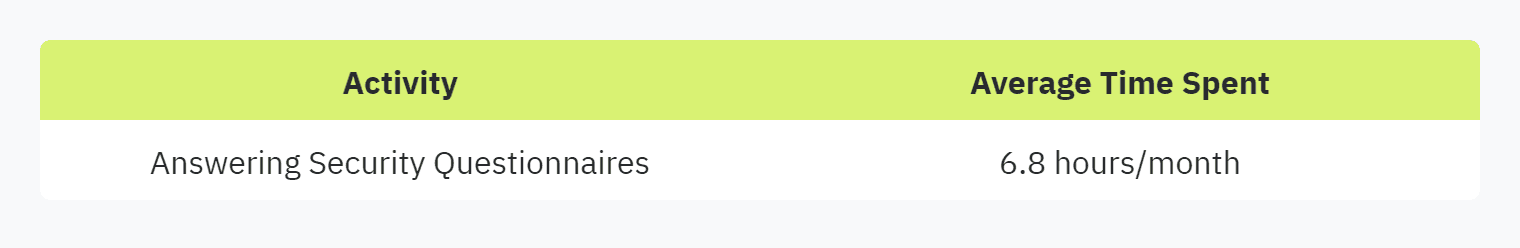
These questionnaires often require detailed answers to complex queries about hosting, authentication & password policies, and data privacy (Skypher). This extensive effort in manual processing diverts valuable resources from other critical tasks, contributing to resource constraints within the organization.
Impact on Business Deals
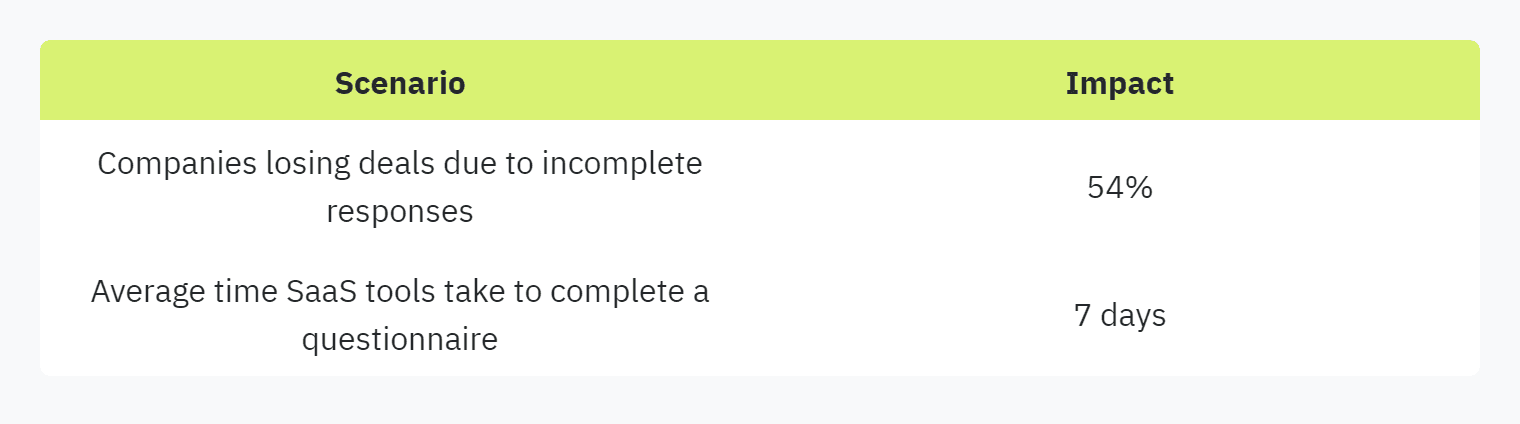
The time taken to complete security questionnaires can have a direct and negative impact on business deals. Delays caused by the manual, time-consuming process can lead to missed opportunities. The Whistic report highlights that 54% of companies have lost deals due to incomplete questionnaire responses.
Although automation through SaaS tools has been adopted to streamline this process, the accuracy remains a concern. SaaS tools are only 50% accurate on average and still take seven days to complete a questionnaire (SecurityPal Blog). This lag in completion time can delay closing deals and result in significant financial losses.
Navigating these challenges requires effective strategies and tools. Automation can play a crucial role here, and exploring options like automating security questionnaires can enhance efficiency. For more in-depth guidance, consider our detailed guide to automating security questionnaires.
Best Practices in Security Questionnaires
Effective handling of security questionnaires is essential for maintaining robust security practices and efficient compliance management. Below, we delve into best practices, focusing on structuring security questionnaires effectively and leveraging automation for efficiency.
Structuring Questionnaires Effectively
Ensuring that security questionnaires are well-structured can streamline the assessment process and enhance accuracy. A clear and concise structure aids in efficient data gathering and minimizes misinterpretation. Here are some key considerations:
Consistent Format: Using a consistent format for questions helps in easier comprehension and faster response times.
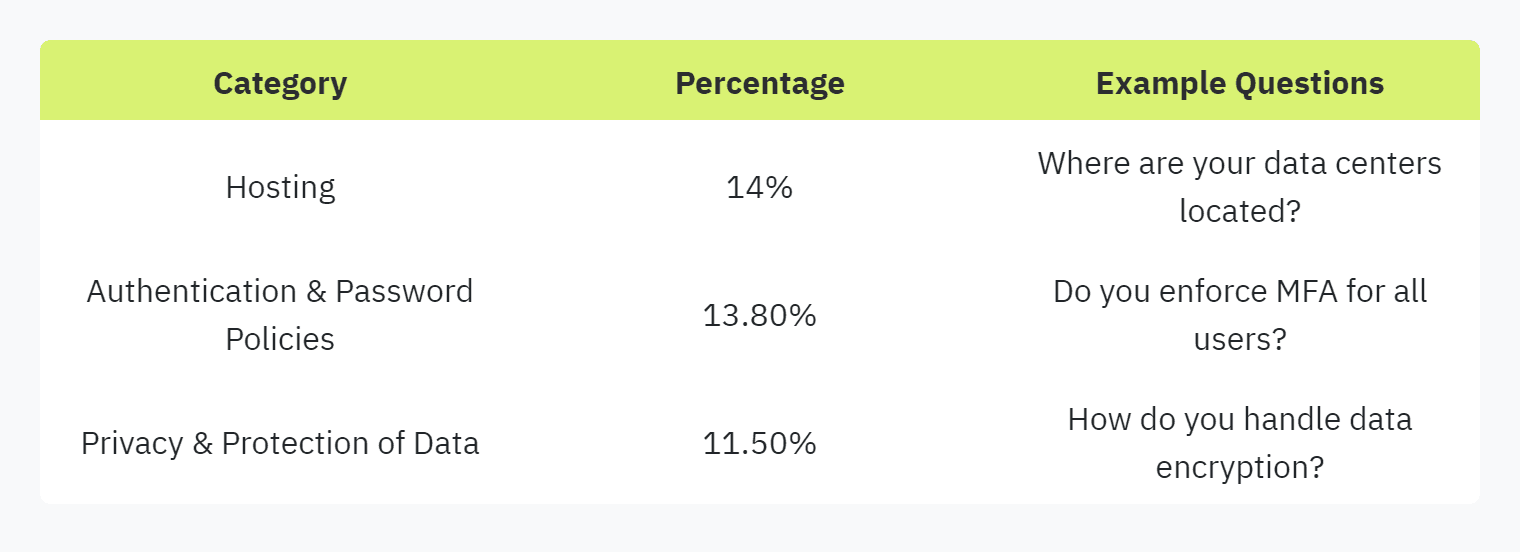
Categorize Questions: Group questions under relevant categories such as Hosting, Authentication & Password Policies, and Privacy & Data Protection, which together account for nearly 39% of all security questions (Skypher). This categorization helps in organized data collection.
Clear Instructions: Providing detailed instructions ensures that respondents understand what is required, thus reducing the chances of incomplete or incorrect answers.
Use of Standards: Leveraging industry standards such as SOC 2, ISO 27001, and other regulatory frameworks to formulate questions can enhance compliance.
Example Table for Categorized Questions:
Visit our section on efficient security questionnaires for more detailed guidelines.
Leveraging Automation for Efficiency
Automation can significantly improve the efficiency of handling compliance in security questionnaires. Automated tools can facilitate the process by pre-filling responses based on historical data, alerting users to incomplete sections, and maintaining consistency across responses.
SaaS Tools: Utilizing Software as a Service (SaaS) tools can streamline the questionnaire response process. While SaaS tools have a 50% accuracy rate on average and can take around seven days to complete a questionnaire (SecurityPal Blog), they offer a significant improvement over manual processes.
Outsourcing: Outsourcing to security specialists combines the benefits of manual processes, automation, and professional expertise. This approach ensures high accuracy and comprehensive results, maintaining a robust security posture for the organization (SecurityPal Blog).
Negative Impacts of Delays: Automating security questionnaires can help mitigate delays in business deals. Manual handling of questionnaires often leads to lost opportunities due to prolonged processing times.
To further ease the process, leveraging automated tools like RPA (Robotic Process Automation) and AI (Artificial Intelligence) can help in data extraction, pattern recognition, and response generation. Interested in how AI can aid in this process? Check out our article on ai in security questionnaires.
By structuring questionnaires logically and utilizing automation technologies, organizations can enhance their compliance management, streamline the security questionnaire process, and minimize the risks associated with manual handling. For insights on specific tools, visit our guide on tools to simplify security questionnaires.
Enhancing Security Posture with Questionnaires
Security assessment questionnaires are vital tools in helping businesses evaluate their security posture and ensure robust vendor risk management strategies. They not only help organizations identify and mitigate potential security risks but also ensure that vendors adhere to industry standards and best practices.
Vendor Risk Management Strategies
Vendor risk management is critical in maintaining a strong security posture, especially when engaging with third-party vendors. Security questionnaires play a crucial role in this process by facilitating the secure exchange of data and information between organizations (Hyperproof).
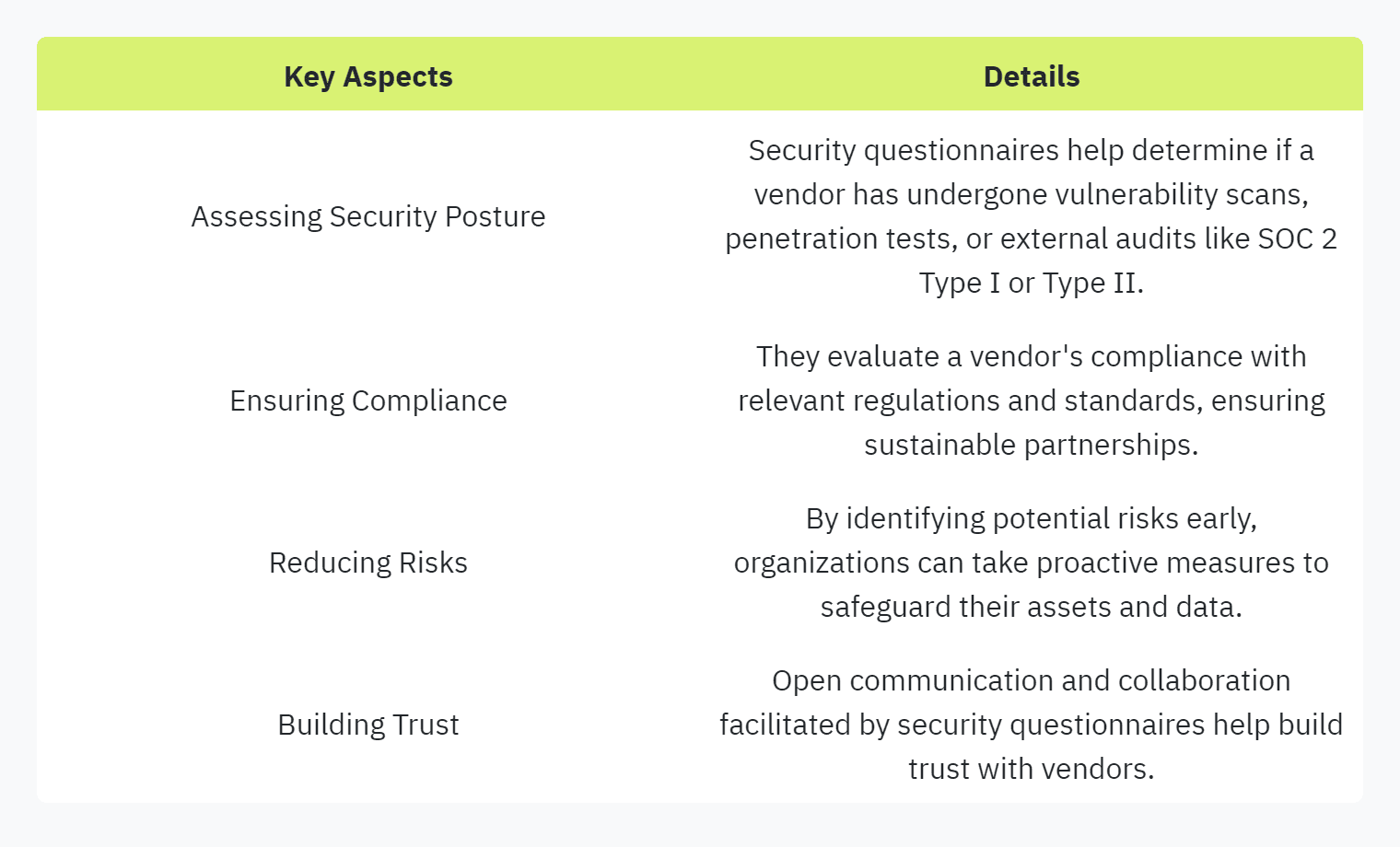
Vendor risk management should cover various security and privacy topics:
Security certifications (e.g., ISO 27001, SOC 2)
GRC (Governance, Risk, and Compliance) management
Continuous compliance efforts
Network security measures
Physical security controls (Secureframe)
For effective vendor assessment, read about automating vendor security assessments.
Utilizing Industry Standards
Utilizing industry standards in security questionnaires is vital for maintaining a high level of security. These standards provide a benchmark for evaluating a vendor’s capabilities and ensuring they align with best practices.
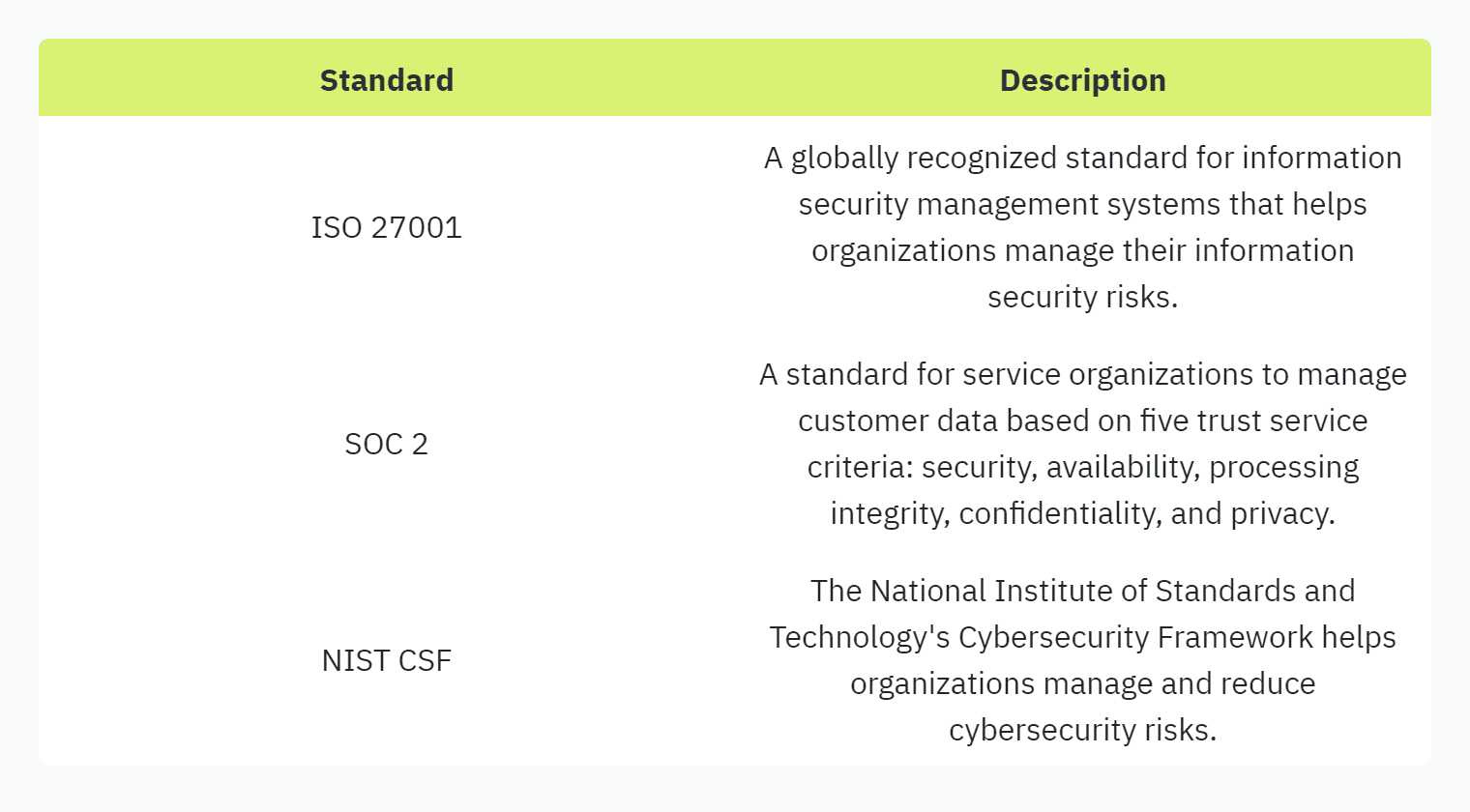
By adhering to these standards, vendors can demonstrate their commitment to maintaining a robust security posture. Incorporating these standards in security questionnaires can provide organizations with a comprehensive understanding of a vendor's security practices.
For more detailed strategies on managing vendor risks and ensuring compliance, check out our articles on common frustrations with security questionnaires and best practices for security questionnaires.
Security questionnaires serve as an essential tool in enhancing your security posture by facilitating diligent vendor risk management and adherence to industry standards. Employing these practices can significantly mitigate risks, ensure compliance, and strengthen overall security strategies in today’s complex digital landscape.
Enter your email to start accelerating your sales today.















