Common frustrations with security questionnaires and how automation helps
Share This Article

Security Questionnaire Challenges
Security questionnaires are critical tools for evaluating the cybersecurity and privacy measures of vendors. However, the process of managing these questionnaires often presents several challenges.
Escalating Cybersecurity Regulations
The surge in the number of security questionnaires sent to companies is largely driven by escalating cybersecurity and compliance regulations. As businesses strive to meet external audits and third-party vendor assessments, the demands for greater transparency and trustworthiness intensify. This constant flux can create numerous hurdles for security and compliance officers, IT managers, and SaaS startups.
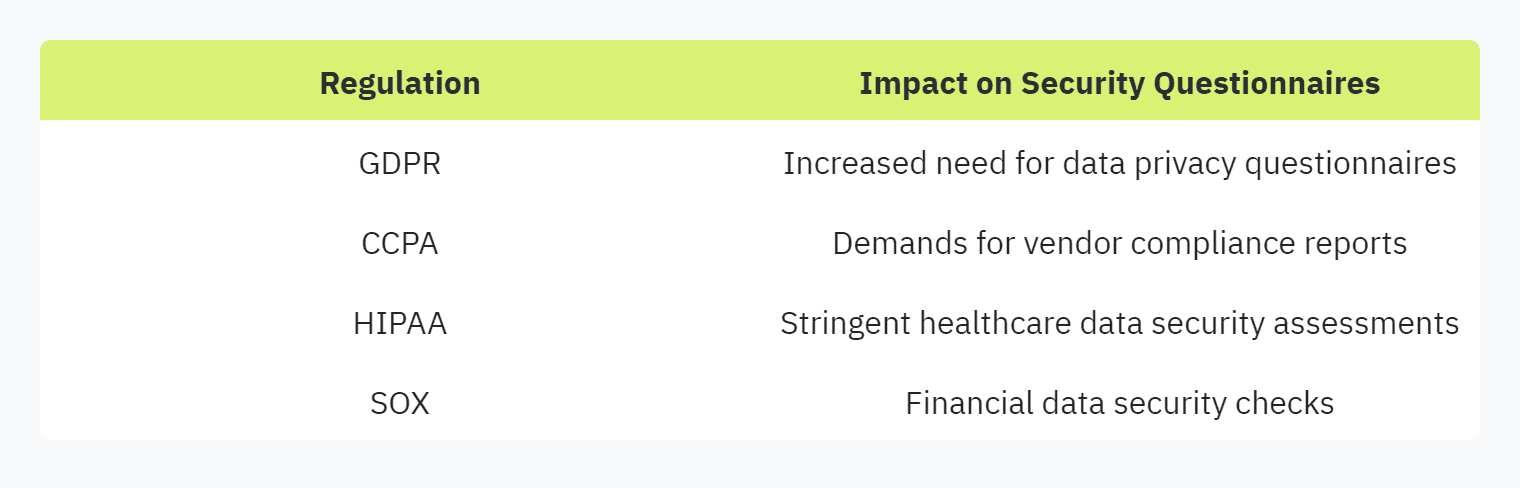
The evolution of these regulations and the addition of new mandates mean that organizations must continuously update their security questionnaires to stay compliant. This continuous adaptation can be both time-consuming and costly for businesses.
Scalability Issues with Manual Processes
Managing security questionnaires manually can be a daunting task, especially as the volume of requests increases. Manual processes often lead to scalability issues, making it difficult for organizations to keep pace with the demand.
Key challenges include:
Time Consumption: Manually filling out questionnaires can take hours, diverting valuable resources from other crucial tasks.
Inconsistency: Different team members might provide varying responses, leading to inconsistencies.
Error-Prone: Manual data entry is susceptible to human error, which can affect the accuracy of the responses.
Tracking Difficulties: Keeping track of multiple questionnaires and their statuses can become overwhelming without a streamlined process.
According to a Deloitte survey, 47% of businesses experienced a risk incident involving an outside vendor, underscoring the importance of thorough and accurate vendor assessments. Relying on manual processes to handle these assessments can undermine their effectiveness and increase an organization's exposure to risk.
To address these scalability issues, many businesses are turning to automation. By automating security questionnaires, organizations can ensure consistency, accuracy, and efficiency. For more information on automating this process, visit our guide to automating security questionnaires.
Understanding these challenges highlights the necessity for efficient security questionnaires and why automating vendor security assessments is becoming increasingly popular. Internal links such as best practices for security questionnaires offer further insights into creating a streamlined and effective questionnaire process.
By acknowledging these challenges, businesses can better prepare themselves to tackle the complexities of modern cybersecurity compliance. For additional tips and strategies, visit streamlining security questionnaires and reducing time to complete security questionnaires.
Benefits of Automation
Integrating automation into the process of completing security questionnaires offers significant advantages over traditional manual methods, especially for security and compliance officers, IT managers, and SaaS startups. Two primary benefits are the consistency and precision of responses, as well as the ability to manage increased workloads effectively.
Consistency and Precision
Manual processes often result in inconsistencies and inaccuracies due to human error. Automation provides a solution by ensuring that responses are uniform and precise across all security questionnaires. Machines do not suffer from fatigue or oversight, significantly reducing the chances of errors. According to Skypher, using innovative software solutions can act as a co-pilot, assisting teams in maintaining high accuracy.
Here are several ways automation enhances consistency and precision:
Standardized Responses: Automated systems can store and reuse pre-approved answers for common questions, ensuring that all responses adhere to the same standard.
Error Reduction: Minimizes human error, leading to more accurate assessments.
Quality Control: Automated systems frequently include checks and validations that ensure the data entered is accurate and complete.
By implementing automation, businesses can ensure that their security questionnaires are consistently accurate, reducing discrepancies that could lead to security vulnerabilities.
Control in Increased Workloads
As companies grow, the volume of security questionnaires they need to handle can become overwhelming. Automation helps manage this increased workload effectively, allowing organizations to maintain control without sacrificing quality. Panorays highlights that automated processes for sending and managing security questionnaires can streamline the process, increase efficiency, and enhance collaboration.
Consider the benefits of enhanced workload control through automation:
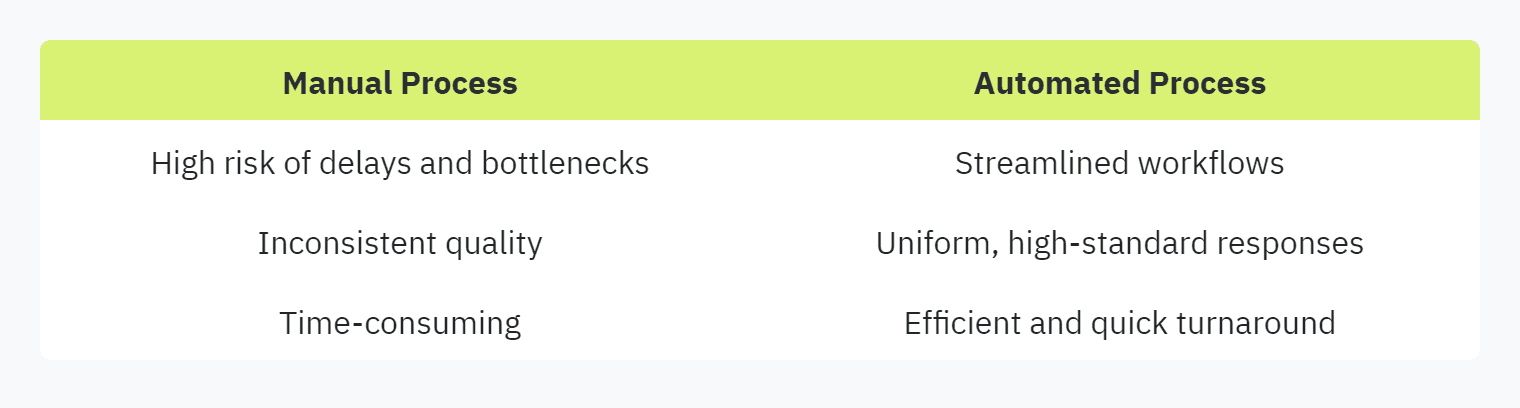
Automation also offers:
Scalability: As the number of questionnaires increases, automation ensures that each one is handled with the same level of detail and accuracy.
Efficient Resource Allocation: Resources previously tied up in manual review can be reallocated to more strategic tasks.
Enhanced Collaboration: Automation tools often come with features that facilitate collaboration among teams.
For more on how to leverage these benefits, visit our in-depth guide to automating security questionnaires.
Incorporating automation not only addresses common frustrations with security questionnaires, but also significantly improves the overall efficiency and reliability of the security assessment process. For a list of tools that can simplify this process, check out our article on tools to simplify security questionnaires.
Vendor Security Assessment
Vendor security assessment is a pivotal process for ensuring that service providers have implemented robust security measures. These assessments not only defend against potential cyber threats but also build trust and transparency between businesses. Understanding the essential components of a security program and the evolution of questionnaire frameworks can help vendors navigate the complexities of these assessments.
Essential Security Program Components
A thorough vendor security assessment evaluates several critical aspects of the vendor's security program. Some essential components include:
Information Security Policies: Documented policies that outline how information security is managed within the organization.
Internal Security Practices: Measures and protocols in place to protect sensitive data, including access controls and encryption.
Incident Response: Preparedness and strategies for identifying, responding to, and mitigating security incidents.
Disaster Recovery Plans: Plans to ensure the continuity of operations in the event of a disruption.
These elements are crucial for demonstrating a vendor's commitment to security. According to UpGuard, these assessments help prioritize risk management, mitigate cyber risks, and prevent data breaches involving third-party vendors and service providers.
To streamline and automate these assessments, tools like OneTrust's Vendorpedia can be invaluable.
Evolution of Questionnaire Frameworks
Security questionnaire frameworks have evolved to keep pace with the increasingly complex and regulated landscape of cybersecurity. These frameworks encourage open communication, transparency, and trust between parties by discussing topics like risk management, incident response, and compliance with industry regulations (Scytale).
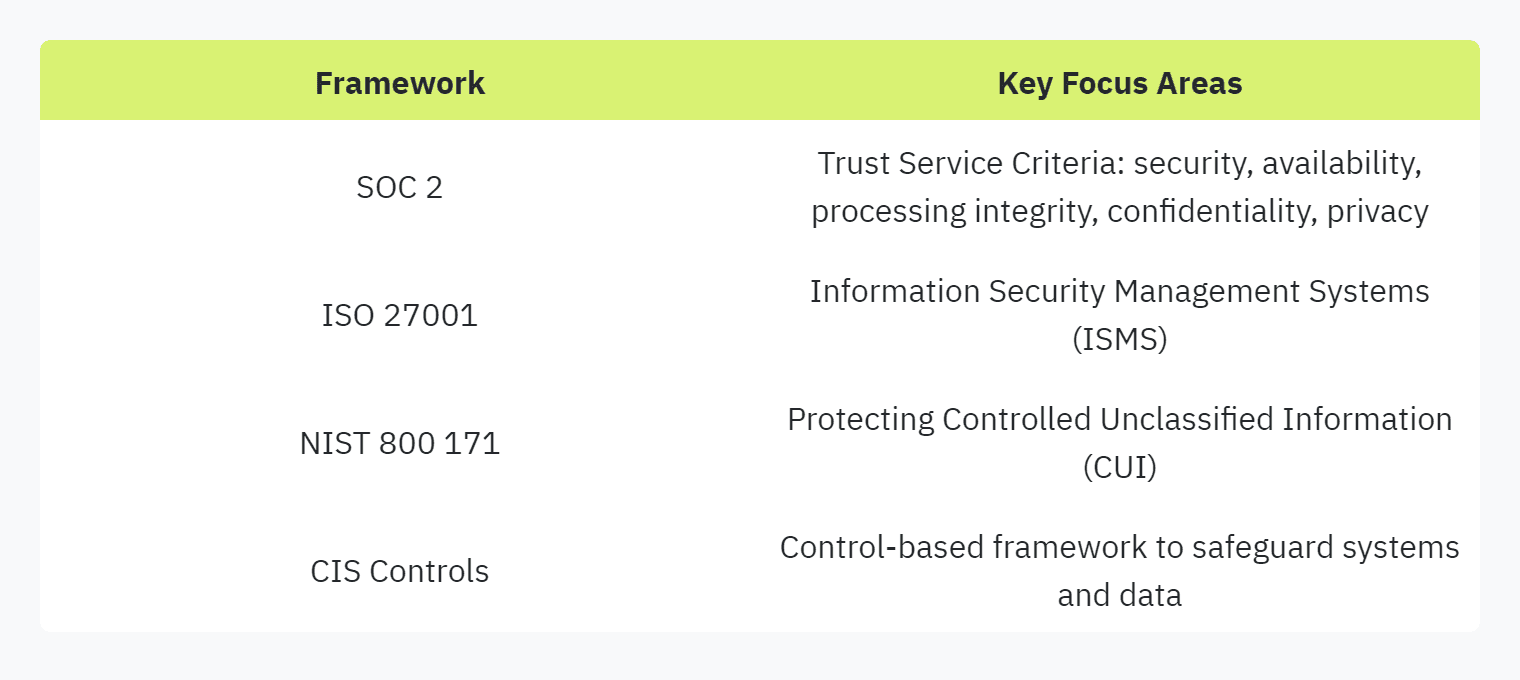
Compliance with Recognized Frameworks
Certification or compliance with recognized security frameworks such as SOC 2, ISO 27001, NIST 800 171, or CIS can significantly aid vendors in responding to security questionnaires (Carbide Secure). These frameworks provide a structured approach to security management and demonstrate a vendor’s commitment to robust security measures.
Modern Questionnaire Practices
Modern security questionnaires often incorporate automation to manage increased workloads efficiently. According to UpGuard, automated systems reduce manual effort and ensure consistent and precise responses. This is reinforced by the practical application of platforms like OneTrust's Vendorpedia.
By integrating these frameworks and leveraging automation tools, vendors can ensure they properly address security questionnaire requirements. For more on how automation helps, read our guide to automating security questionnaires. For best practices, check our article on best practices for security questionnaires.
Best Practices for Vendors
Security questionnaires can be a source of frustration for vendors, but following best practices can streamline the process. Two critical areas to focus on are creating customized questionnaires and using clear, direct language.
Customized Questionnaires
Vendors often receive generic security questionnaires from companies, resulting in lengthy assessments that are time-consuming and may lead to vendor fatigue. By tailoring questionnaires to specific vendor relationships, companies can align questions with their risk appetite and regulatory needs, significantly reducing frustration (Panorays).
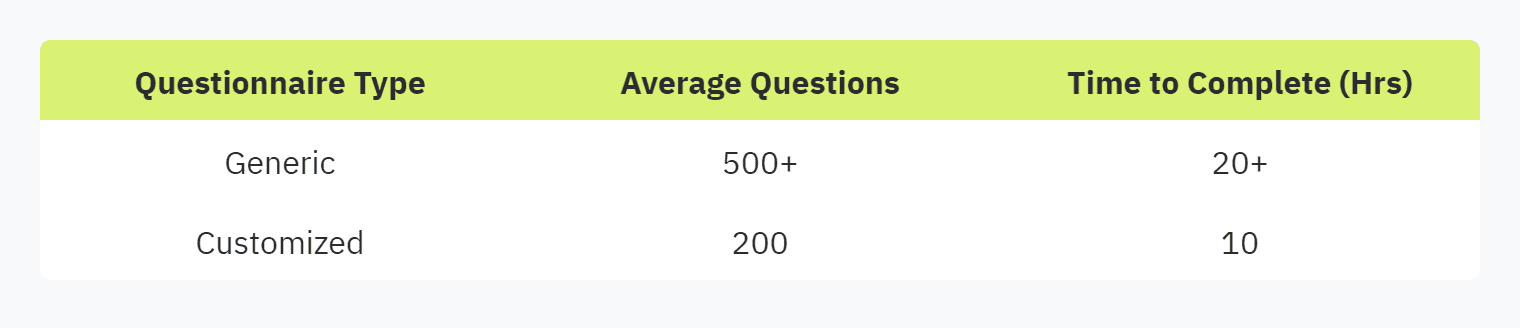
Customizing questionnaires helps address relevant security concerns without overwhelming the vendor. This targeted approach encourages thorough and accurate responses, enhancing the quality of the assessment. For more insights, refer to our article on improving security questionnaire experience.
Clear and Direct Language Usage
Using clear and direct language in security questionnaires is crucial for obtaining accurate and swift responses. Questions that can be answered with simple responses such as "yes," "no," or "n/a" are preferable (Panorays). This straightforward approach not only reduces the chances of misinterpretation but also speeds up the assessment process.

Clear communication fosters transparency and trust between parties, facilitating discussions on risk management, compliance, and incident response protocols. This proactive engagement can help identify and resolve potential issues early. For best practices on questionnaire language, visit simplifying security questionnaire language.
By implementing these best practices, companies can reduce the common frustrations with security questionnaires and enhance the overall efficiency and effectiveness of their security assessments. Additional resources on this topic can be found in our articles on automating security questionnaires and tools to simplify security questionnaires.
Enter your email to start accelerating your sales today.
















