Top tools to simplify security questionnaires for small teams
Share This Article

Simplifying Security Questionnaires
Importance of Security Questionnaires
Security questionnaires are essential tools for assessing the security postures of third-party vendors. They help organizations identify potential vulnerabilities and mitigate risks associated with external partnerships. Completing these questionnaires is crucial for ensuring that vendors meet necessary security standards.
Risk Mitigation: They enable companies to identify and address potential security risks before entering into business agreements.
Building Trust: These questionnaires foster trust and secure relationships by verifying that vendors adhere to stringent security protocols.
Resource Optimization: Many organizations outsource the task to specialized firms like Compass IT Compliance to ensure accuracy and free up internal resources.
For more insights on why security questionnaires are a nightmare but necessary, explore our detailed articles.
Standard Security Questionnaire Types
Organizations use various standard security questionnaires to evaluate third-party vendors' controls related to data privacy, information security, business continuity, and regulatory compliance (SafeBase). Here are some common types:
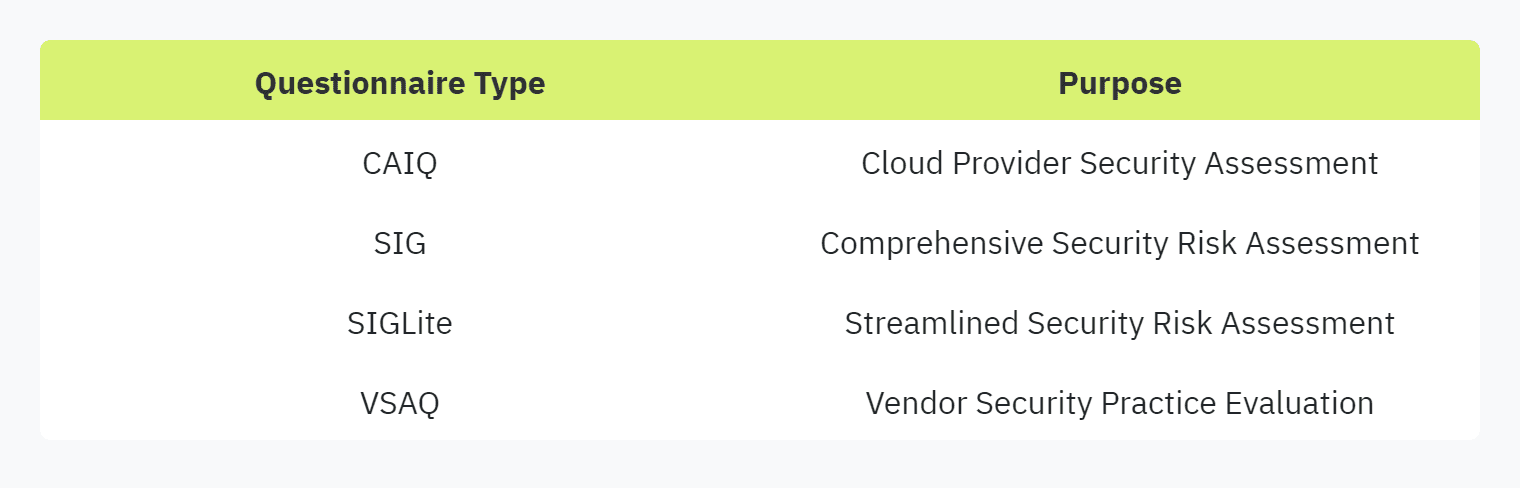
CAIQ (Consensus Assessments Initiative Questionnaire): Used for cloud providers to assess security controls.
SIG (Standardized Information Gathering) and SIGLite: Detailed and streamlined questionnaires for comprehensive security and risk assessment.
VSAQ (Vendor Security Assessment Questionnaire): Evaluates vendors' security practices specifically.
Organizations often create customized questionnaires to address specific security needs and compliance requirements. Common templates include:
VSAQ
CIS Critical Security Controls Questionnaire
NIST 800-171
SIGQ
CAIQ
For further guidance on understanding security questionnaires and adapting them to your needs, explore our resources.
Understanding these standard types and their purposes can help organizations better streamline the security questionnaire process. For more information on streamlining security questionnaires and enhancing efficiency, refer to our guides.
Streamlining the Process
Efficiently streamlining the process of completing security questionnaires can be a game-changer for many organizations, especially small teams. Let's explore the steps involved and how automation can be utilized.
Steps in Completing a Security Questionnaire
Completing a security questionnaire involves several critical steps. Here's a standardized process to follow:
Outlining the Requirements: Understand the scope and requirements of the questionnaire.
Collecting Necessary Documentation: Gather all required documents and data supporting your responses.
Assigning Responsibilities: Designate key stakeholders responsible for various sections.
Providing Supporting Documentation: Include evidence and documentation to support your answers.
Answering Truthfully: Provide honest and accurate responses to each question.
Reviewing Responses: Thoroughly review the questionnaire for accuracy and completeness.
Continuous Improvement: Regularly iterate to enhance your security posture (SafeBase).
Utilizing Automation for Security Questionnaires
Automation can significantly streamline the process of completing security questionnaires. Several tools are specifically designed to automate these tasks, reducing the time and effort required.
Benefits of Automation
Efficiency: Automation speeds up the process, reducing time to respond.
Accuracy: Reduces the risk of human error.
Consistency: Ensures uniform responses.
Compliance: Helps maintain ongoing compliance with industry standards (Hyperproof).
Key Tools and Features
Automation tools offer various features to streamline security questionnaires:
By leveraging such tools, organizations can optimize the process of security questionnaires and focus more on improving their overall security stance.
For further details on how to utilize these tools effectively, check out our guide on automating security questionnaires and best practices for security questionnaires. Automating responses not only saves time but also ensures consistency across multiple assessments, aligning them with your security frameworks like SOC 2 or NIST. This helps organizations address vendor security assessments efficiently.
Tools for Automation
Identifying the right tools to automate security questionnaires can significantly ease the burden on small teams. Here are three platforms that offer comprehensive solutions for simplifying this process.
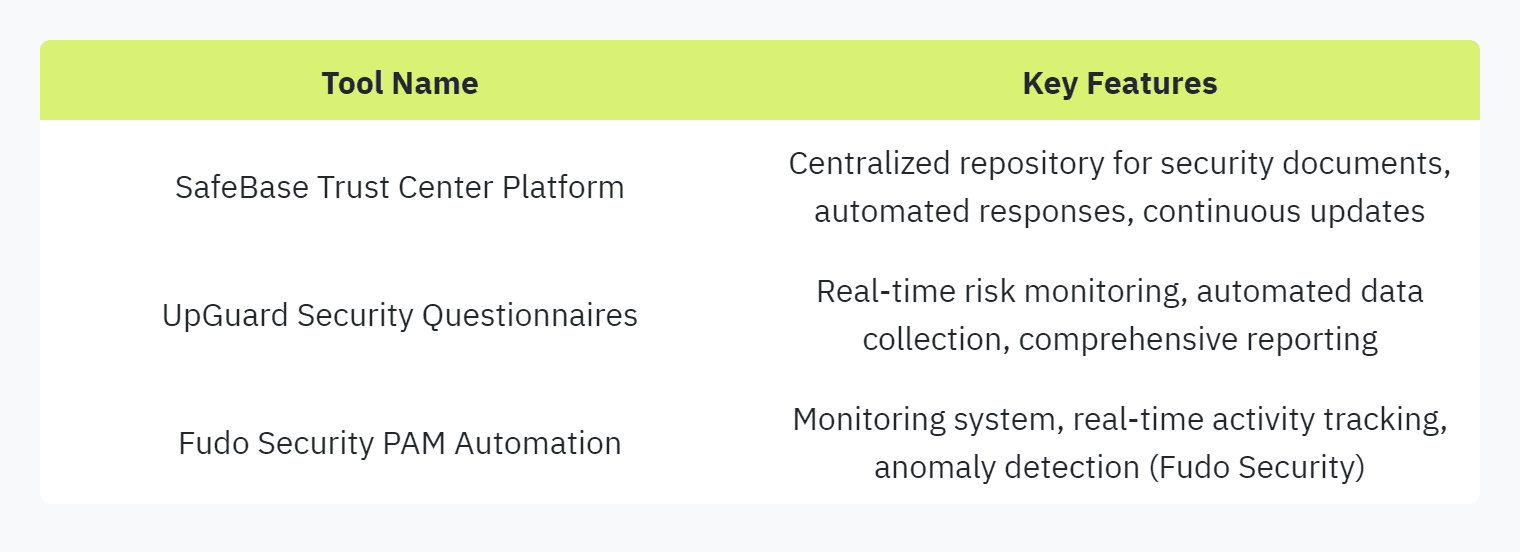
SafeBase Trust Center Platform
SafeBase's Trust Center Platform is designed to automate the security review process, enabling companies to effectively communicate their security and trust posture. This platform supports a more streamlined buying experience by positioning security as a revenue driver.
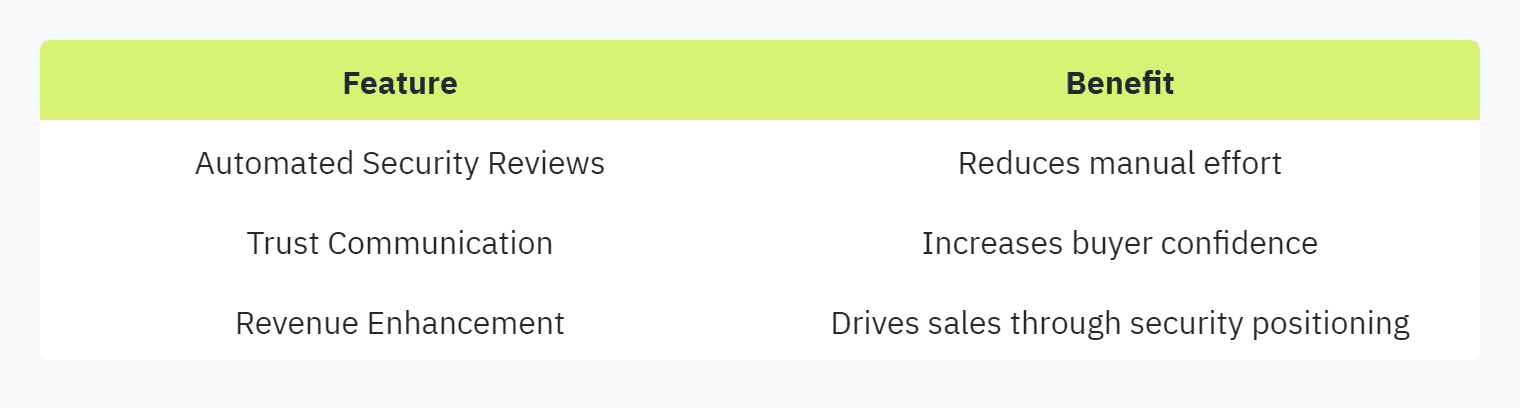
Key Features
Automated Security Reviews: Simplifies the process of responding to security questionnaires.
Trust Communication: Enhances transparency, aiding in customer trust.
Revenue Enhancement: Positions security as a key factor in the sales process.
Leverage the SafeBase Trust Center to efficiently manage and communicate your organization's security posture. For more on automating security questionnaires, visit our guide to automating security questionnaires.
UpGuard Security Questionnaires
UpGuard offers a robust solution for security questionnaires with its AI Autofill feature. This tool helps users automatically populate security questionnaires, reducing manual entry errors and saving time. UpGuard's Trust Exchange includes additional features such as security ratings and data leaks detection, further enhancing the security assessment process.
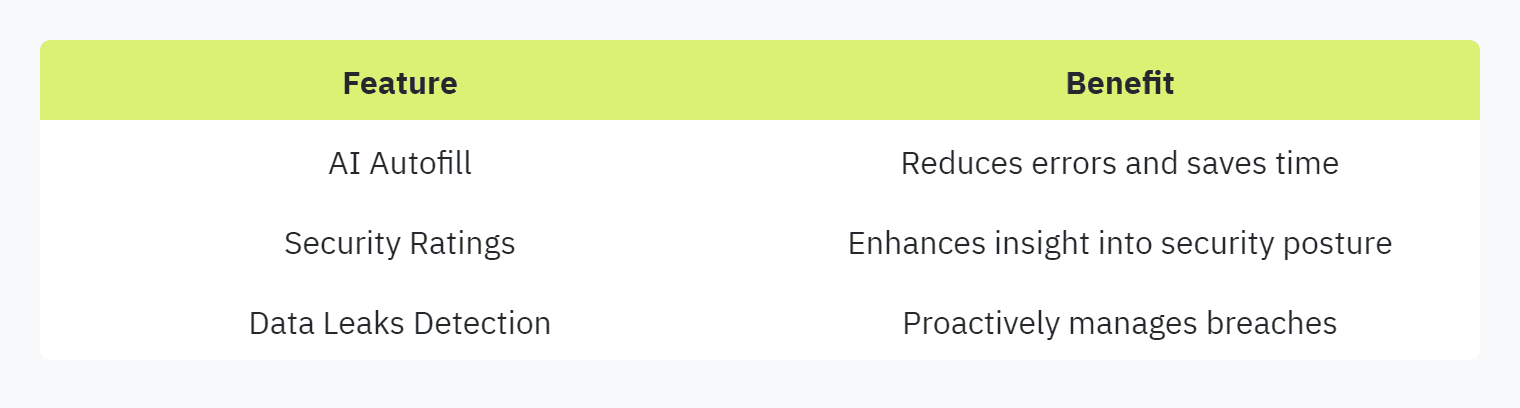
Key Features
AI Autofill: Automatically populates security questionnaires.
Security Ratings: Provides insights into security posture.
Data Leaks Detection: Identifies and addresses potential security breaches.
Using UpGuard can streamline your security assessments and provide valuable insights. For related content, see our page on automating security questionnaires.
Fudo Security PAM Automation
Fudo Security PAM Automation is an advanced tool for simplifying the management of privileged access. It integrates cloud computing to automate processes such as access provisioning, credential rotation, and session monitoring.
Key Features
Access Provisioning Automation: Streamlines access control.
Credential Rotation: Ensures security of access credentials.
Session Monitoring: Tracks and audits privileged sessions.
Utilizing Fudo Security PAM Automation can significantly improve the efficiency of managing privileged access, reducing manual intervention and minimizing errors. Learn more about enhancing security assessments on our platform.
Explore these tools for simplifying security questionnaires and enhancing your organization's security practices. For additional insights, consider reading about leveraging AI in security assessments.
Enhancing Security Posture
Benefits of Security Questionnaire Automation
Security questionnaire automation offers numerous benefits, especially for small teams managing multiple security assessments. By utilizing automation tools, teams can streamline the entire process, ensuring efficiency and accuracy without compromising the security posture.
Efficiency and Speed Automation significantly reduces the time spent on completing security questionnaires, allowing teams to focus on more critical tasks. This reduces time to complete security questionnaires, enabling faster responses to potential vendors and partners.
Consistency and Accuracy Automated systems utilize pre-sourced security information, reducing the chances of inaccuracies and inconsistencies. According to SafeBase, this approach ensures that responses are consistent across different questionnaires, improving the quality and reliability of the responses.
Collaboration and Integration By facilitating collaboration on AI-generated responses, teams can work together seamlessly. Automation tools also integrate with other security systems, such as Identity and Access Management (IAM) platforms, enhancing the overall security and compliance framework (Fudo Security). Find out more about collaboration in security questionnaires.
Reduction in Human Error Manual completion of security questionnaires is prone to human error. Automation minimizes manual intervention, significantly reducing the risk of mistakes and ensuring accurate responses.
Real-Time Monitoring and Alerts Implementing automation in security questionnaires allows for real-time activity monitoring and anomaly detection. This enhances the ability to identify and respond to suspicious behavior promptly, reducing the risk of data breaches (Fudo Security). Explore more about automating security questionnaire responses.
Leveraging AI and Technology for Security Assessments
The integration of Artificial Intelligence (AI) and advanced technology in security assessments has revolutionized how organizations handle security questionnaires. Here are some ways AI and technology are leveraged:
AI-Powered Response Generation AI enables the auto-generation of responses based on pre-sourced information, ensuring relevant and accurate answers. This capability eliminates the need for extensive manual effort in drafting responses, as outlined by SafeBase.
Standardized Playbooks and Runbooks Using standardized playbooks and runbooks, security teams can ensure consistent incident response handling, improving detection capabilities and response accuracy (Fudo Security). For more details, check out our guide on automating security questionnaires.
Enhanced Detection Capabilities Tools like Security Information and Event Management (SIEM) systems and Privileged Access Management (PAM) solutions utilize AI to improve real-time monitoring and anomaly detection. Learn more about ai in security questionnaires.
Improved Customer Trust By leveraging AI and automation tools, organizations can enhance their security posture, ensuring the protection of sensitive customer information. This builds customer trust and satisfaction, as effective security measures are in place (Hyperproof).
Utilizing technology not only simplifies the process of completing security questionnaires but also enhances the overall security framework of the organization. Check out our resources on ai and automation in security questionnaires.

If you’re looking for an affordable and straightforward security questionnaire automation platform, check out our service at lessquestionnaires.com.
Enter your email to start accelerating your sales today.
















