Ensuring data privacy while automating security questionnaires
Share This Article

Importance of Security Questionnaires
Security questionnaires play a pivotal role in ensuring data privacy and safeguarding sensitive information within businesses. They help to assess and manage risks, ensuring the robustness of an organization's security measures.
Role in Data Breach Prevention
Security questionnaires are a fundamental tool in the prevention of data breaches. They enable organizations to thoroughly vet their vendors and partners, ensuring that they adhere to stringent security standards. This due diligence is crucial, especially given that 55% of healthcare organizations experienced third-party data breaches in 2021, as reported by the HIPAA Journal. By systematically assessing security policies through these questionnaires, organizations can identify and mitigate vulnerabilities, reducing the likelihood of unauthorized access to sensitive data.
Effective use of security questionnaires aids in monitoring and controlling access to personal data. This is essential to prevent unauthorized access and potential breaches. Without visibility over personal data collection, usage, and sharing, businesses can face significant operational and technical challenges, making security questionnaires even more critical.

For more on this topic, explore our articles on why security questionnaires are a nightmare and common frustrations with security questions.
Financial Implications
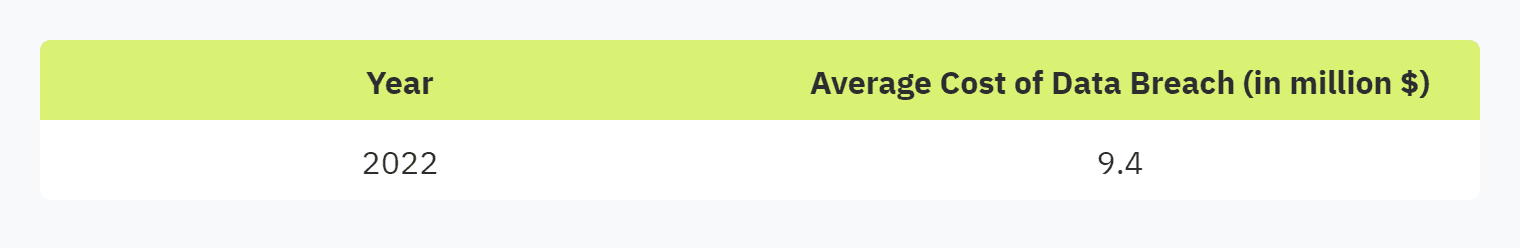
The financial repercussions of data breaches are substantial. In 2022, the average cost of a data breach reached $9.4 million per incident, excluding hidden costs. These figures underscore the importance of maintaining strong security measures, including the use of comprehensive security questionnaires.
Businesses not only face direct costs related to breach remediation but also hidden costs such as loss of customer trust, legal fees, and regulatory fines. Additionally, organizations often need to allocate significant budgets to address technological, security, and employee training needs to prevent future breaches.
Properly implementing security questionnaires can help mitigate these expenses by preventing breaches before they occur. By ensuring that vendors and partners comply with necessary security standards, organizations can lower their risk profile and avoid costly incidents.
For those seeking to streamline the process, consider reading our guide on automating security questionnaires and explore tools to simplify security questionnaires.
Ensuring data privacy through security questionnaires is crucial in today's digital environment. By utilizing these tools effectively, organizations can not only prevent data breaches but also manage the associated financial risks, fostering a more secure operational framework. For more insights, check out our articles on compliance in security questionnaires and ai in security questionnaires.
Compliance Requirements and Regulations
Understanding and adhering to compliance requirements and regulations is crucial in the realm of [data privacy in security questionnaires]. Compliance not only ensures legal adherence but also boosts consumer trust and confidence. Key regulations such as the CCPA and the GDPR specifically address data protection and privacy needs.
CCPA and GDPR
The California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR) are two major regulations that significantly impact how organizations handle data privacy and security.
California Consumer Privacy Act (CCPA)
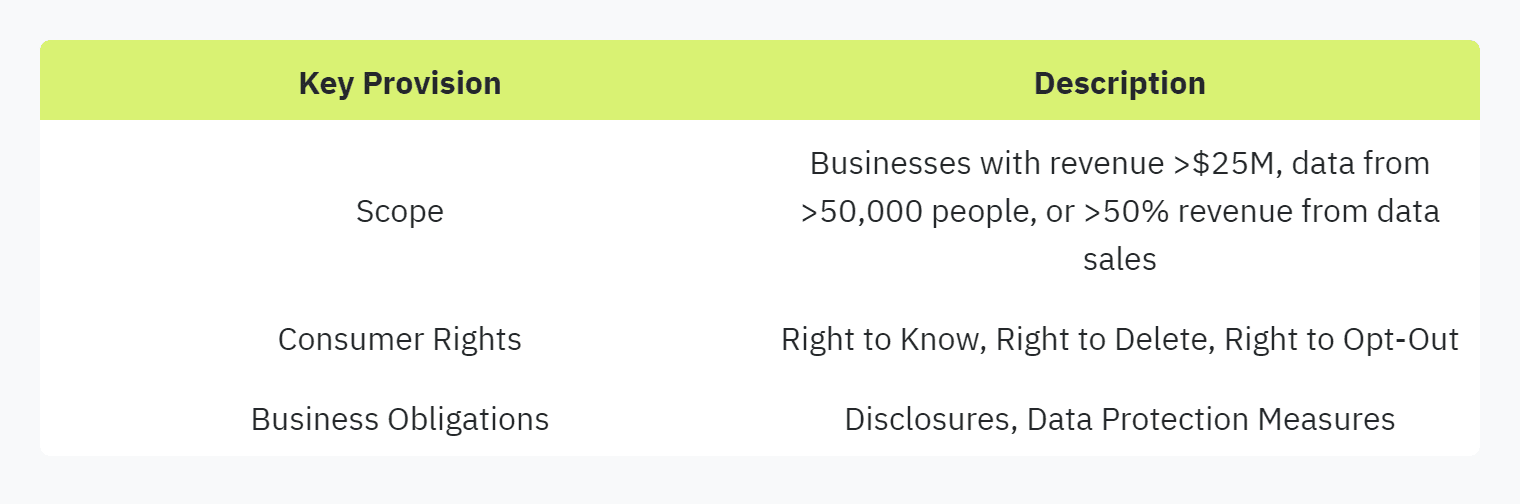
The CCPA applies to businesses with annual revenues that exceed $25 million, possess personal information from more than 50,000 individuals, or earn more than half of their revenue from selling personal data (Responsive.io). The act regulates consumer data privacy and enforces the following key points:
Consumer Rights: Empower consumers with the right to know what personal data is collected, the purpose of data collection, and the ability to access, delete, or opt-out of the sale of their data.
Business Obligations: Requires businesses to disclose data collection and sharing practices and implement data protection measures.
General Data Protection Regulation (GDPR)
The GDPR by the European Union enforces stringent data protection laws for EU citizens, affecting all organizations that collect and process data from EU residents (OneTrust).
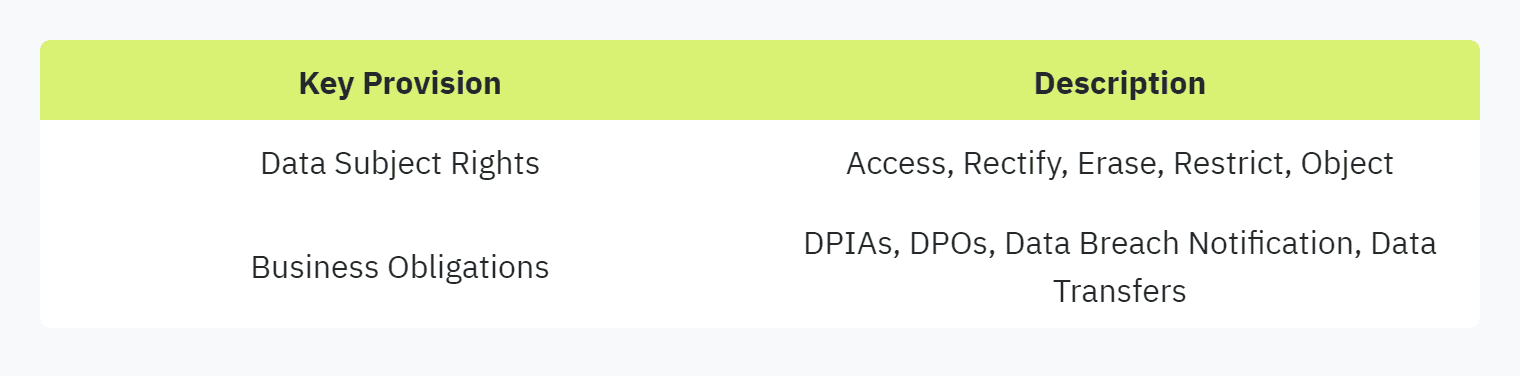
Data Subject Rights: Includes the right to access personal data, rectify inaccuracies, erase data (right to be forgotten), and restrict or object to data processing.
Accountability and Governance: Mandates Data Protection Impact Assessments (DPIAs) and the appointment of Data Protection Officers (DPOs).
For more about compliance intricacies, refer to our articles on compliance in security questionnaires and how to implement automation in compliance measures.
Industry-Specific Mandates
Different industries face unique compliance requirements tailored to their specific needs and risks. These mandates aim to ensure stringent data protection standards across various sectors.
Healthcare: HIPAA
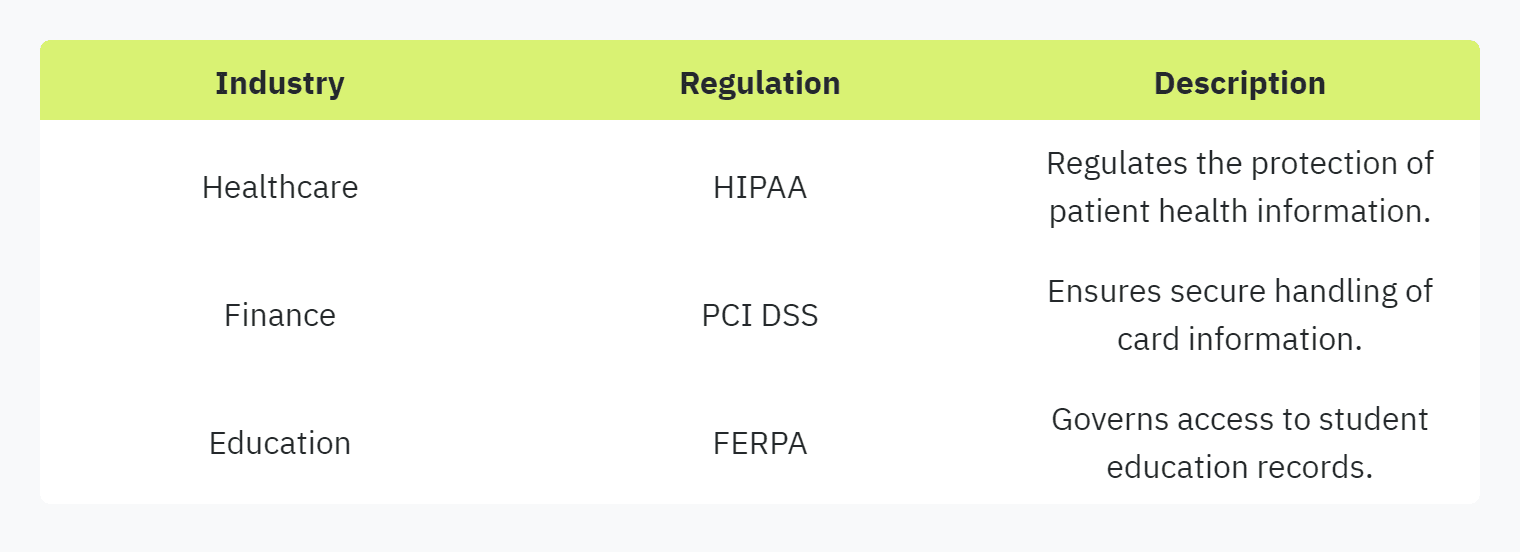
The Health Insurance Portability and Accountability Act (HIPAA) mandates strict protection of patient health information (PHI). Organizations must ensure confidentiality, integrity, and security of PHI while permitting health information exchanges that support high-quality healthcare.
Finance: PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) ensures the secure handling of card information to mitigate risks of data breaches. Businesses must adhere to the standard's 12 requirements, covering safe storage, transmission, and processing of card data.
Education: FERPA
The Family Educational Rights and Privacy Act (FERPA) provides students control over their education records, restricting unauthorized access without consent. Educational institutions must implement measures to protect the privacy of student information.
Aligning with these compliance requirements is essential for organizations to not only avert legal repercussions but also to enhance data security and public trust. For a complete list of industry-specific regulations, check our detailed guide to automating security questionnaires to streamline compliance efforts efficiently.
Understanding these regulations and their implications is vital for organizations looking to automate security questionnaires. By incorporating compliance requirements into automation tools, businesses can ensure lawful and secure handling of personal data while improving efficiency.
Challenges in Security Questionnaires
Security questionnaires are indispensable in ensuring data privacy and compliance. However, they come with several challenges that can impede efficiency and effectiveness. Addressing these challenges requires a clear understanding of vendor compliance demands and the time constraints that often lead to the loss of deals.
Vendor Compliance Demands
Organizations are increasingly required to undergo intricate Vendor Security Assessments (VSAs) to ensure that vendors and suppliers meet stringent security criteria. This rising demand for detailed security assessments is driven by the need to mitigate potential cyber risks (EY CEO Imperative Study). Companies must comply with various security frameworks that safeguard their data against threats, as seen in incidents like the Marriott Hotel data breach and the Twitter data leak (OneTrust).
Security questionnaires serve as a vital component of a company's due diligence process. They enable organizations to evaluate the security and data privacy practices of potential partners before entering into collaborations. This process is essential in third-party risk management and helps build trust with partners (Secureframe).
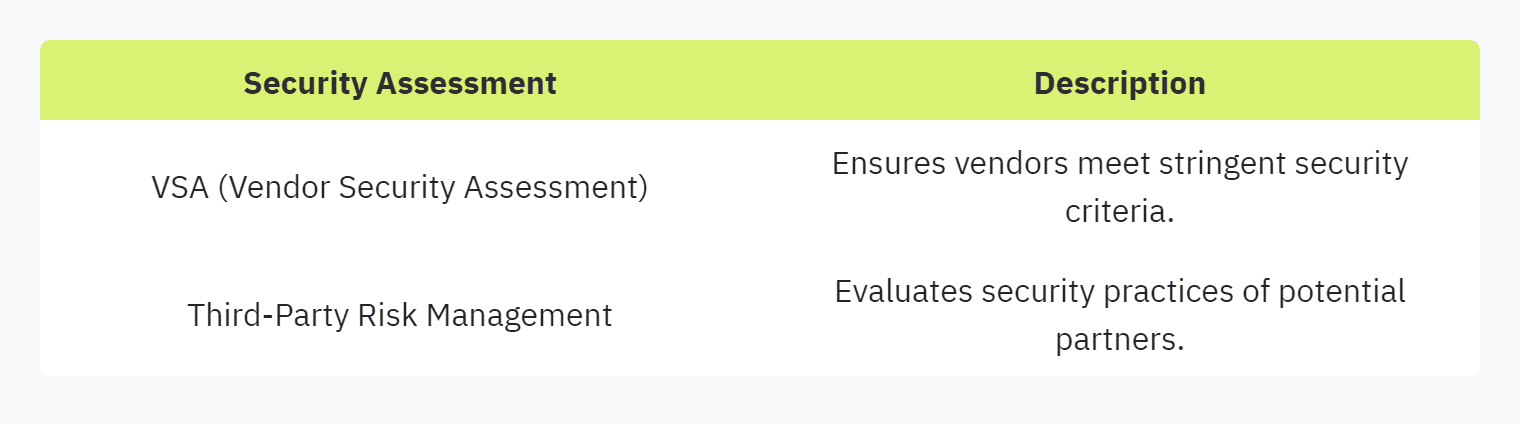
The continuous rise in security requests reflects the growing importance of assessing the security practices of third-party collaborators. This comprehensive review process is crucial for maintaining data privacy and compliance standards.
Time Constraints and Loss of Deals
One of the most significant challenges associated with security questionnaires is the time constraint. The increasing volume and complexity of these assessments often result in prolonged review periods, which can delay business operations and hinder potential deals. This time-consuming process can lead to the loss of business opportunities as companies struggle to keep up with the demands of completing multiple security questionnaires.
Security questionnaire automation is a promising solution to address these scalability issues. By automating tasks, organizations can enhance the consistency, precision, and control of their responses. This approach not only alleviates the workload on information security and GRC professionals but also improves the efficiency of the overall process (Skypher). Implementing automation tools can streamline the process, reducing the time required to complete security questionnaires and thus minimizing the risk of losing deals.

To learn more about the benefits of automation and how to implement these tools, visit our article on automating security questionnaires.
Security and compliance officers, IT managers, and SaaS startups can greatly benefit from understanding these challenges and exploring solutions. For additional tips and resources, consider reading our articles on reducing time to complete security questionnaires and tools to simplify security questionnaires.
Automation Solutions for Security Questionnaires
Delving into the realm of automation solutions for security questionnaires reveals several pathways to efficiency and accuracy. Here, we will explore the benefits of automating these crucial elements and the steps to implement the right tools for the job.
Benefits of Automation
The use of automated tools in managing security questionnaires can provide numerous advantages. These benefits address the pressing need for precision and speed, especially when dealing with the high volume of security evaluations many organizations face today.
Enhanced Efficiency and Consistency
Automation significantly boosts efficiency by reducing the manual labor involved in responding to questionnaires. This is particularly useful for scaling up operations without proportionally increasing human resources. Automation systems ensure consistency in responses, maintaining uniformity across various security assessments.
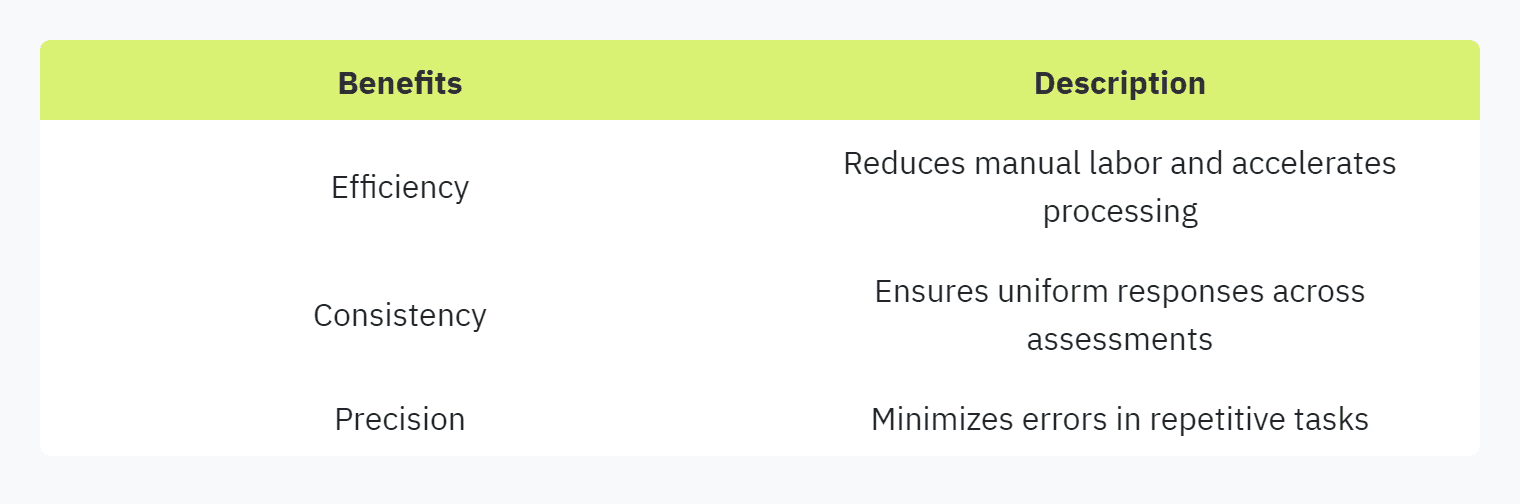
Automated systems also enhance precision, reducing the likelihood of errors—a common issue in manual handling of security questionnaires. By utilizing innovative software solutions, teams can manage heavy workloads more effectively (Skypher).
Implementing Automation Tools
The implementation of automation tools for security questionnaires encompasses several key steps. Selecting the right tools, training personnel, and integrating these tools into existing workflows can transform the process.
Selecting Suitable Tools
Choosing the appropriate automation software is critical. Organizations should seek tools that provide comprehensive features tailored to their specific needs. Considerations include:
Heat maps for identifying risk areas
Real-time analytics for monitoring questionnaire responses
Integration capabilities with existing systems
Explore our guide on tools to simplify security questionnaires for recommendations.
Training and Deployment
Once the tools are selected, thorough training is essential for successful implementation. Training helps to ensure that the team can leverage all functionalities of the software to its full potential. Organizations should also establish clear guidelines on how to use the tools effectively.
Integration with Existing Systems
For seamless operation, integration with current systems is necessary. The process should include:
Syncing with existing databases to fetch necessary data
Linking with compliance management systems for streamlined workflows
Setting up automated notifications to alert teams of important updates
For a detailed discussion, check our article on integrating security questionnaires.
By harnessing the power of automation, organizations can improve the accuracy and efficiency of their security questionnaires, leading to better data privacy management and compliance with regulations. For further information, read about the best practices for security questionnaires and measuring ROI of security questionnaire automation.
Enter your email to start accelerating your sales today.















