A simple guide to automating security questionnaires
Share This Article

Understanding Security Questionnaires
Security questionnaires are vital for organizations to assess the trustworthiness and compliance of vendors, partners, and internal processes. This section delves into their purpose, importance, and the common challenges associated with them.
Purpose and Importance
Security questionnaires serve several critical functions:
Risk Assessment: They help identify potential security threats posed by vendors and partners.
Compliance Verification: Ensure that business activities align with industry standards and regulations.
Transparency and Trust: Foster open communication and trust between involved parties.
By completing these questionnaires, organizations can proactively address risk management strategies, incident response protocols, and maintain regulatory compliance, thus avoiding costly disruptions and legal complications.
Common Challenges
Despite their importance, security questionnaires often present a range of challenges:
Customization vs. Standardization
Finding the right balance between customization and standardization can be challenging. Standardized questionnaires might miss unique risks associated with different vendors or industries. (Arphie)
Integration Complexity
For organizations with established vendor management and risk assessment processes, integrating automated security questionnaires can be complex. This requires robust API integrations and flexible deployment options. (Arphie)
Data Quality and Accuracy
Ensuring the accuracy and quality of data in automated questionnaires can be problematic. Advanced solutions using natural language processing and machine learning algorithms are necessary to address issues like inconsistencies and to prompt for clarification. (Arphie)
Continuous Updates
The cybersecurity landscape is constantly evolving, necessitating that automated questionnaires stay current with new threats and regulations. Leading automation platforms continuously update their knowledge base to adapt to the latest security trends. (Arphie)
For more insights into these challenges, explore common frustrations with security questionnaires.

To delve deeper into automating these processes, visit our article on automating security questionnaires.
Benefits of Automation
Automating security questionnaires can significantly assist security officers, IT managers, and SaaS startups in managing complex and time-consuming compliance tasks more efficiently. Here are the primary benefits:
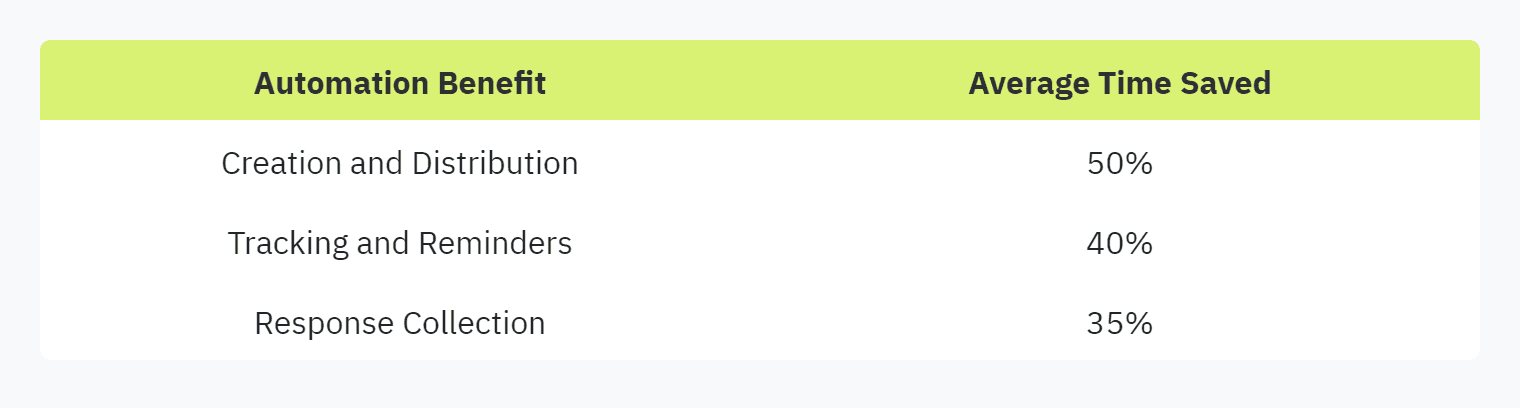
Efficiency and Time-Saving
Automating security questionnaires streamlines the entire process, from creation to distribution and management. This not only saves time but also reduces the chances of human error.
Automated Questionnaires Creation: Automation tools facilitate the creation of comprehensive questionnaires tailored to various compliance needs.
Automating Reminders and Follow-Ups: By automatically sending reminders, organizations can ensure timely responses without manual intervention.
Real-time Progress Tracking: Automation allows for real-time tracking of questionnaire completion, providing instant insights into the progress.
A study reports that AI automation for security questionnaires significantly boosts efficiency by reducing turnaround times.
For more on streamlining the process, visit efficient security questionnaires.
Reduction of Compliance Risks
Automation tools help in tracking regulatory and framework compliance, enhancing alignment, improving information security, and reducing regulatory violation risks.
Risk Prioritization: Automation can automatically identify compliance risks based on vendor questionnaire responses, helping security teams to prioritize risks effectively.
Intelligent Analysis: Utilizing AI and machine learning, automation tools can analyze responses for compliance risks, ensuring that high-risk areas are addressed promptly (Responsive.io).
Enhanced Security Posture: By reducing manual errors and ensuring comprehensive compliance checks, automation enhances the overall security posture of the organization.
Organizations using automation report a significant reduction in compliance-related risks and costs, which allows them to focus on high-value tasks and streamline risk management.
For more detailed information on enhancing compliance, visit compliance in security questionnaires.
Implementing these automation benefits can markedly improve both the efficiency and security of handling security questionnaires, making it a crucial strategy for any security-conscious organization. Don't miss our articles on automating vendor security assessments and ai in security questionnaires for further insights.
Strategies for Automation
Utilizing AI and Machine Learning
AI-driven automation offers transformative benefits in the realm of security questionnaires, especially for those managing multiple compliance and security checks. The integration of Artificial Intelligence (AI) and Machine Learning (ML) drastically improves the efficiency and accuracy of this otherwise tedious process.
AI automation can substantially reduce manual efforts, thus saving on labor costs and minimizing the need for external assistance (Arphie). Machine Learning algorithms and Natural Language Processing (NLP) enable the automatic generation of responses based on historical data, which allows businesses to meet tight deadlines and reduce turnaround times.
The advantages of deploying AI-driven security questionnaire automation include:
Cost Reduction: Lowering operational costs by reducing the need for manual labor and decreasing the probability of costly mistakes.
Compliance Tracking: Automatically identifying compliance risks based on responses, helping prioritize risk management (UpGuard).
Enhanced Efficiency: Streamlined process management with AI ensuring accurate and standardized responses.

Adoption of AI in security questionnaires assists in effortless integration and deployment within existing systems, improving overall information security, and minimizing regulatory violations. For more details on AI usage, browse our page on AI in security questionnaires.
Integration and Deployment Challenges
Though automation provides numerous benefits, integrating and deploying these systems can present challenges. Understanding and addressing these obstacles is crucial for successful implementation.
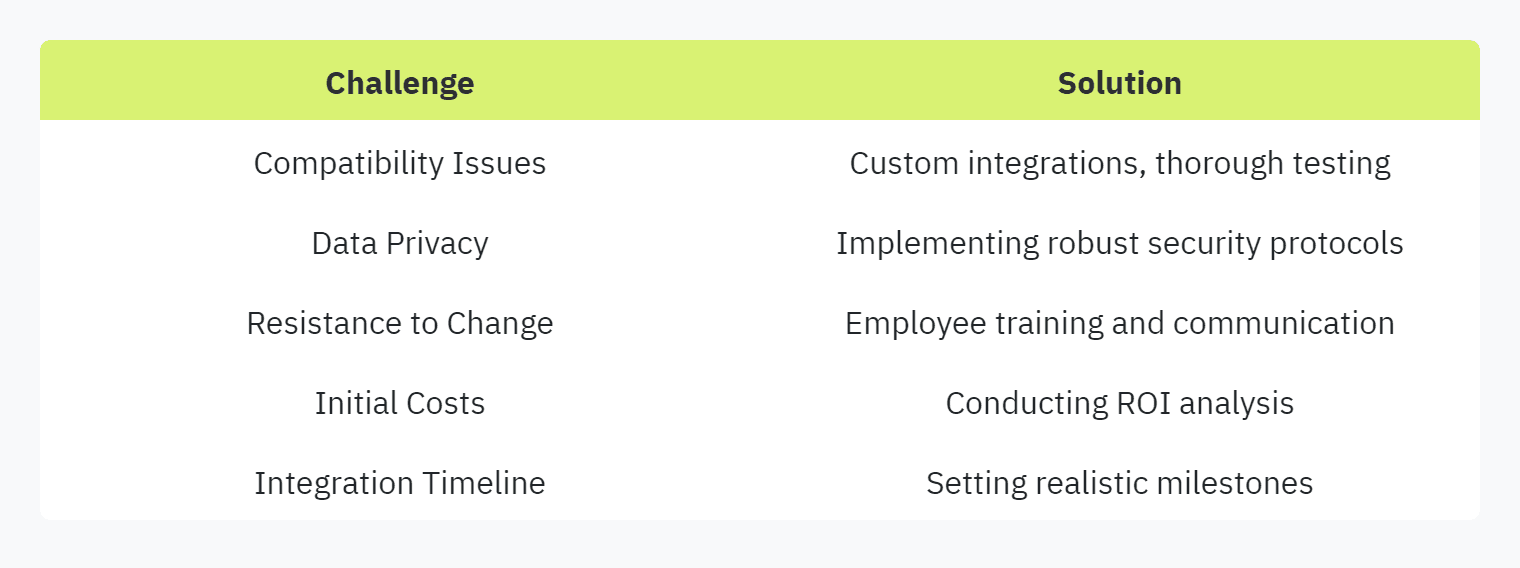
1. Compatibility with Existing Systems: One of the most significant challenges is ensuring that new automation tools are compatible with existing IT and security infrastructure. Custom integrations might be needed to ensure seamless operation, which can be both time-consuming and complex.
2. Data Privacy Concerns: Implementing AI-driven solutions necessitates handling a lot of sensitive data. Ensuring data privacy and securing the information from unauthorized access is paramount. For pointers on safeguarding data, explore our guidelines on data privacy in security questionnaires.
3. Resistance to Change: Organizations might face resistance from employees who are accustomed to manual processes. Effective training programs and clear communication about the benefits can ease this transition.
4. Cost of Implementation: While automation can save costs in the long run, the initial investment required for deploying AI and ML technologies can be high. It’s crucial to calculate the ROI of security questionnaire automation to make informed decisions.
5. Integration Timeline: Integrating automation tools can be time-consuming. Organizations should set realistic timelines and milestones to manage expectations and ensure a smooth transition.
By addressing these challenges head-on, organizations can leverage the full potential of AI-driven automation, ultimately enhancing their efficiency and compliance management. Visit our detailed page on reducing time to complete security questionnaires for more strategies.
For further insights, refer to our articles on automating security questionnaires and integrating security questionnaires.
Best Practices and Implementation
Collaboration and Task Assignment
In the realm of security questionnaire automation, effective collaboration and task assignment are fundamental to ensuring smooth operations. Task assignment involves the distribution and delegation of responsibilities among team members, managers, and stakeholders. Utilizing automation tools can greatly streamline this process.
Key Benefits:
Automated Workflows: Implementing software such as Centraleyes allows organizations to automate workflows. This includes distributing questionnaires, tracking responses in real-time, and sending automated notifications to stakeholders.
Transparency: Automated processes enhance transparency, allowing all team members to stay informed of their tasks, upcoming deadlines, and the progress of the entire project.
Efficiency: Automated notifications ensure that tasks are completed on time, reducing delays in risk management processes.
Best Practices:
Define Roles and Responsibilities: Clearly outline each team member’s role in the process.
Use Project Management Tools: Leverage tools like Centraleyes to automate task assignments and notifications.
Set Milestones: Establish clear milestones and deadlines to track progress efficiently.
Foster Communication: Encourage open communication among team members to address issues promptly.
For more detailed guidance on task assignment in security questionnaires, refer to our article on collaboration in security questionnaires.
Reporting and Analytics Integration
Advanced reporting and analytics capabilities are critical when automating security questionnaires. These capabilities provide actionable insights and ensure continuous improvement in the security posture.
Key Benefits:
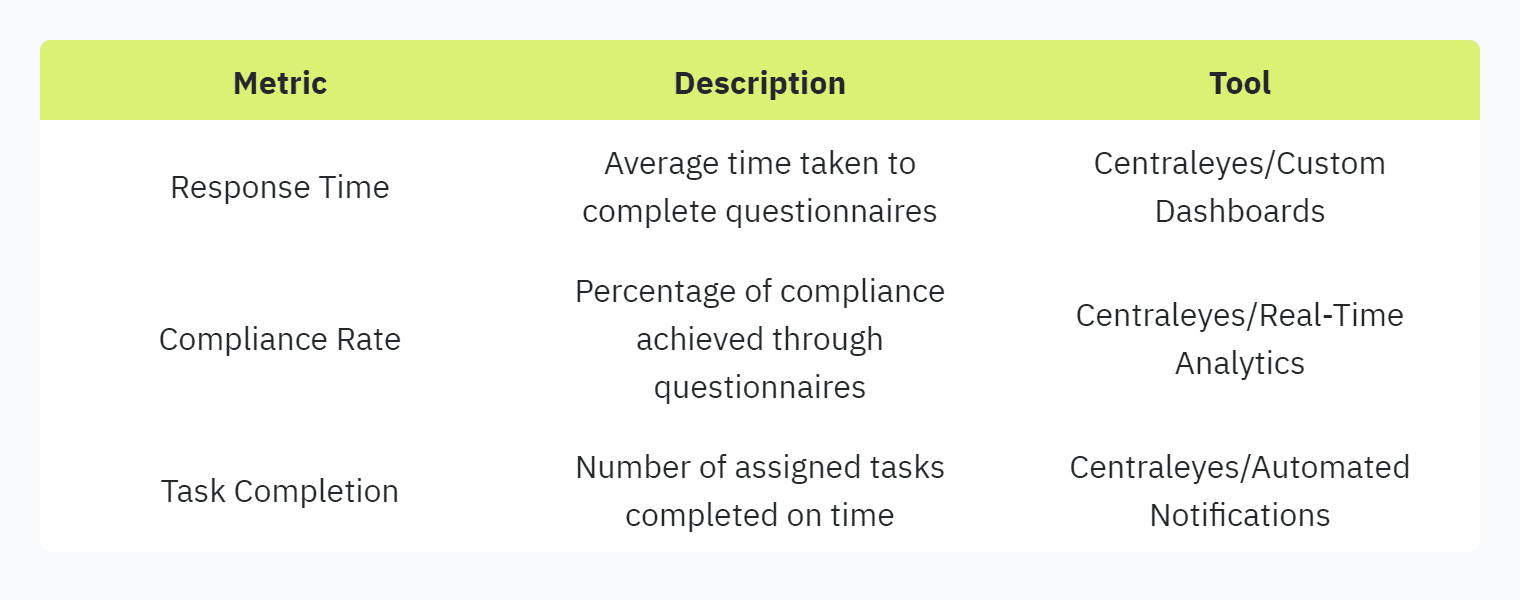
Customizable Dashboards: Tools like Centraleyes offer customizable dashboards that allow stakeholders to visualize data and track performance metrics.
Real-Time Analytics: Real-time analytics enable organizations to measure the effectiveness of their risk management strategies (Centraleyes).
Actionable Insights: With advanced reporting features, teams can identify areas for improvement and demonstrate compliance to both internal and external stakeholders.
Best Practices:
Utilize Real-Time Data: Continuously monitor real-time data to get an up-to-date overview of security assessments.
Generate Detailed Reports: Create detailed reports that highlight key metrics and areas of concern.
Leverage Visualizations: Use visual representations of data to make complex information more understandable.
Monitor Compliance: Regularly track compliance metrics to ensure adherence to regulatory standards.
Internal Links:
Learn more about tracking security questionnaire responses to keep your team informed.
Visit our page on data insights in security questionnaires for tips on leveraging analytics.
By adopting these best practices and integrating advanced reporting and analytics, organizations can optimize their efforts in automating security questionnaires, ensuring a more efficient and compliant security posture. For additional resources, explore our article on best practices for security questionnaires.
Enter your email to start accelerating your sales today.
















