How efficient security questionnaires build trust with clients
Share This Article

Streamlining Security Questionnaires
Efficient security questionnaires play a crucial role in building trust with clients by providing consistent and accurate information. Streamlining the process involves balancing customization with standardization and ensuring the quality and accuracy of responses.
Balancing Customization and Standardization
One of the key challenges in automating security questionnaires is finding the right balance between customization and standardization. Customization is essential to capture the unique risks associated with different vendors or industries. However, too much customization can lead to inconsistencies and make the process cumbersome.
To strike this balance, organizations can:
Implement templates: Use standardized templates that cover the most common security questions while allowing for customization where needed.
Create a flexible framework: Develop a framework that incorporates core security principles but can be easily adjusted to address specific vendor or industry requirements.
Leverage automation tools: Utilize AI-powered platforms like Arphie to automate responses by reusing historical data and mapping answers across similar questions.
By achieving a balance between customization and standardization, organizations can streamline the questionnaire process and reduce the administrative burden on both vendors and compliance officers.
Ensuring Response Quality and Accuracy
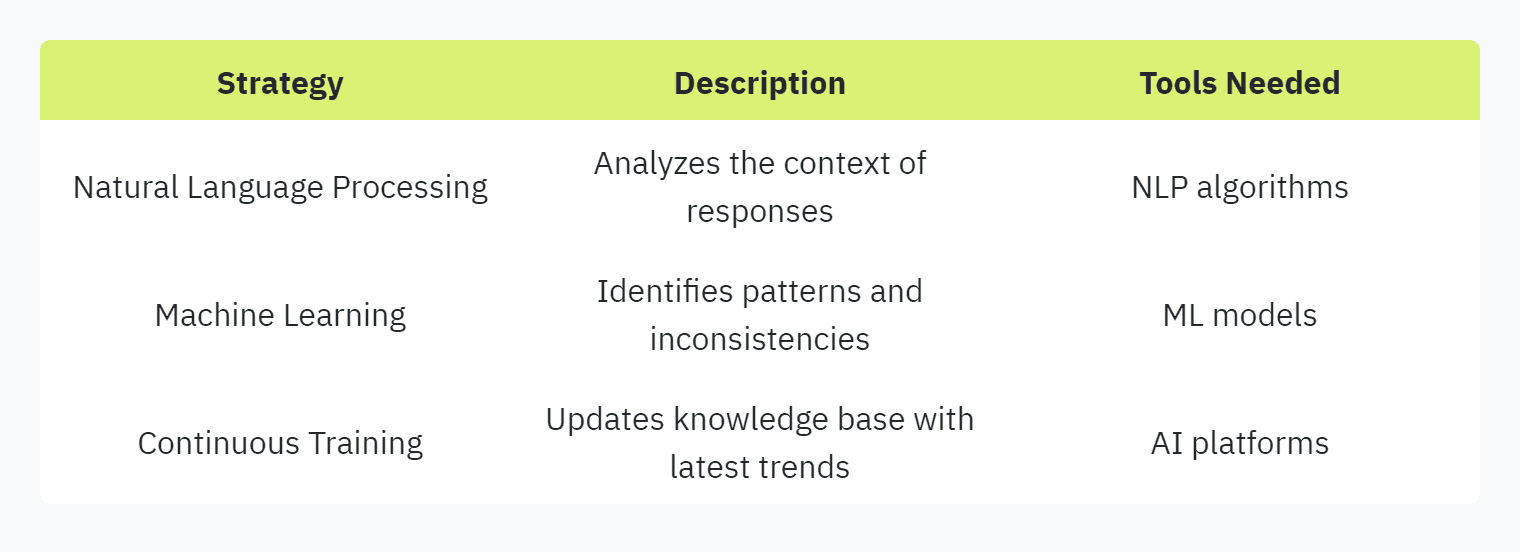
Ensuring the quality and accuracy of responses in automated security questionnaires is paramount. Advanced solutions using natural language processing and machine learning algorithms are essential to flag inconsistencies and maintain the integrity of the data.
Strategies for ensuring quality and accuracy include:
Natural Language Processing (NLP): Utilize NLP to analyze and understand the context of responses, ensuring they match the intent of the questions.
Machine Learning Algorithms: Deploy machine learning to identify patterns and inconsistencies in responses, providing real-time feedback for corrections.
Continuous Training and Updates: Regularly update the knowledge base with the latest security trends and regulations to maintain the relevance of the questionnaire content (Arphie).
Ensuring response quality and accuracy not only builds trust with clients but also aids in compliance and risk management. For more insights on improving the security questionnaire process, visit our article on best practices for security questionnaires and automating security questionnaires.
Employing these strategies helps in minimizing errors, reducing inconsistencies, and maintaining the reliability of security questionnaires, thus fostering a streamlined and efficient process. For additional tips, refer to our guide on streamlining security questionnaires and tools to simplify security questionnaires.
Automating Security Questionnaires
With the increase in cyber threats and regulations, automating security questionnaires has become essential. This process utilizes AI and machine learning to streamline and enhance accuracy, making it crucial for security officers, compliance managers, and IT heads.
Continuous Adaptation to Threats and Regulations
Automated security questionnaires must stay current with evolving threats and regulations. AI and machine learning play a pivotal role in this continuous adaptation. Solutions like Arphie use these technologies to update knowledge bases and adapt to the latest security trends and regulatory requirements.
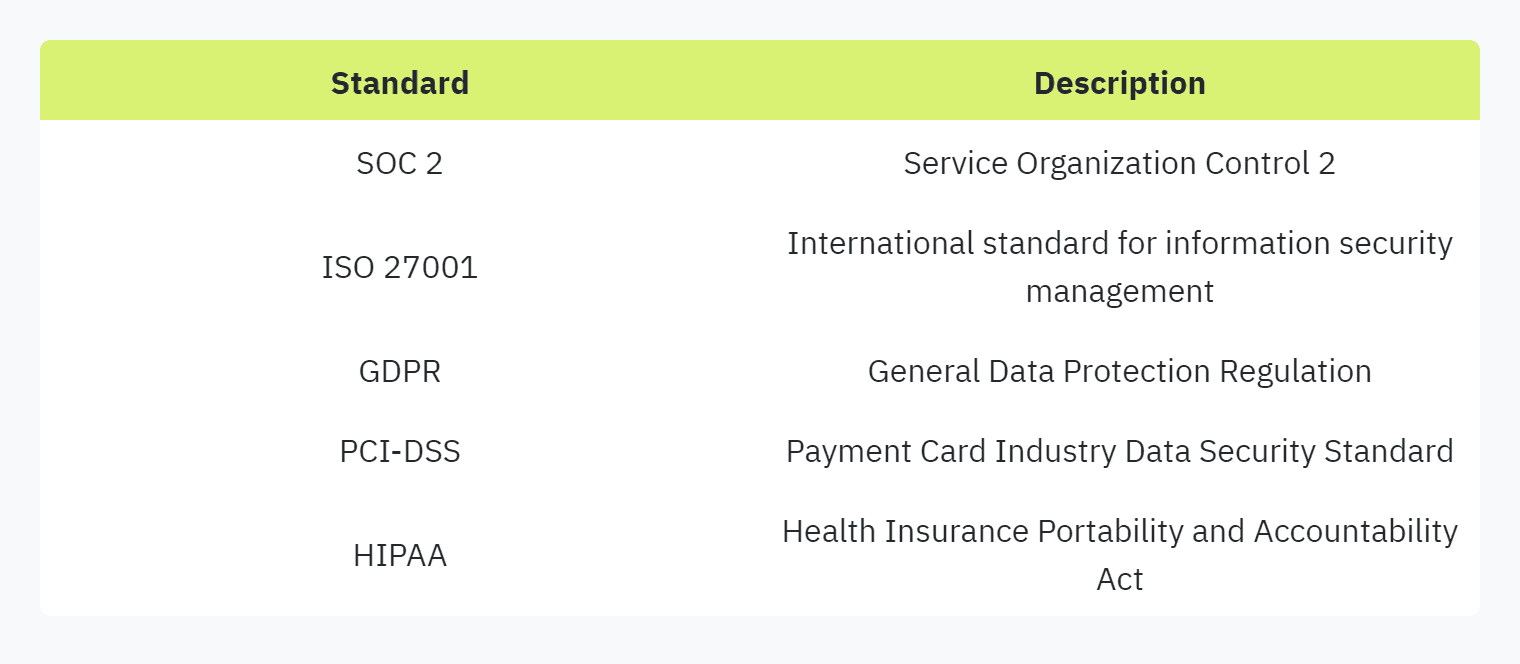
Effective automation ensures compliance with industry standards such as SOC 2, ISO 27001, GDPR, PCI-DSS, and HIPAA (Scytale). This involves evaluating third-party vendors for vulnerability scans, penetration tests, and external audits, thereby enhancing the overall cyber security assessment process.
By ensuring that their questionnaires are up-to-date, organizations can transform managing vendor risk assessments into a streamlined process, saving time and resources (Arphie). This not only protects organizations from potential regulatory penalties but also from financial losses and reputational damage resulting from third-party breaches.
User Adoption and Training
User adoption and training are critical components of successfully implementing automated security questionnaires. To ensure seamless adoption, organizations must provide comprehensive training programs that cover the functionality and benefits of the automation tools.
Training should include:
Basic understanding of the automation tools.
Detailed steps on how to leverage AI for pre-sourced security information.
Techniques for reducing inconsistencies and inaccuracies in responses.
Guidelines on compliance with various security standards.
Addressing FAQs and potential user concerns.
Users must feel confident in deploying automated questionnaires. This includes understanding the customization options available to cater to specific organizational needs. Training sessions should also emphasize the importance of protecting sensitive data through automation tools, thus reinforcing the organization's commitment to data privacy.
For further insights on automation practices, explore our comprehensive guide to automating security questionnaires, and for strategies to promote user adoption, visit our page on training for security questionnaire automation.
By focusing on continuous adaptation and robust user training, organizations can effectively leverage automated security questionnaires to build trust with clients, streamline compliance, and enhance their overall security posture.
Best Practices for Vendors
Centralizing Security Documentation
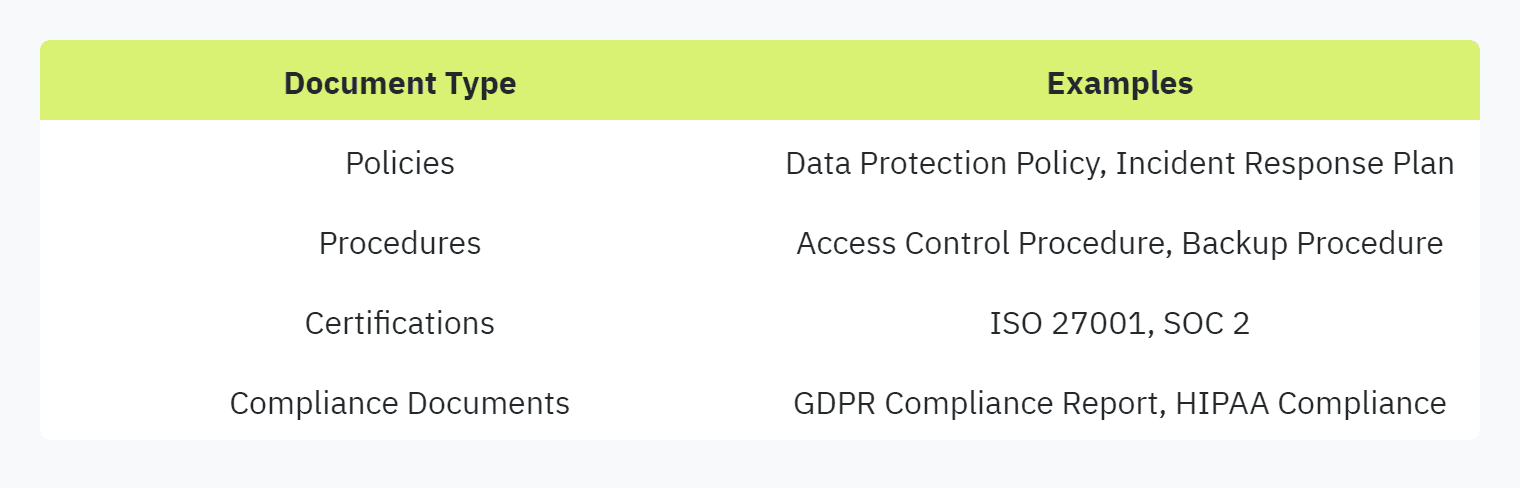
To streamline the process of responding to efficient security questionnaires, vendors should centralize their security documentation. By creating a central repository containing relevant policies, procedures, certifications, and compliance documents, vendors can significantly speed up the process and maintain consistency across their responses.
Implementing a centralized system offers several benefits:
Consistency: Ensures uniformity in responses to various questionnaires.
Time-saving: Reduces the time required to gather documents and information.
Efficiency: Streamlines the response process for future questionnaires.
Accuracy: Minimizes errors and discrepancies in the provided information.
A centralized repository can include the following types of documents:
For a deeper understanding, visit our guide on streamlining security questionnaires.
Leveraging Automation Tools and AI
Automation tools and AI have revolutionized the way vendors handle security questionnaires. Utilizing AI-powered platforms, such as Arphie, can automate the completion of security questionnaires. These platforms reuse historical data, generate responses, and map answers across similar questions, thereby reducing the burden on vendors and ensuring accuracy and consistency.
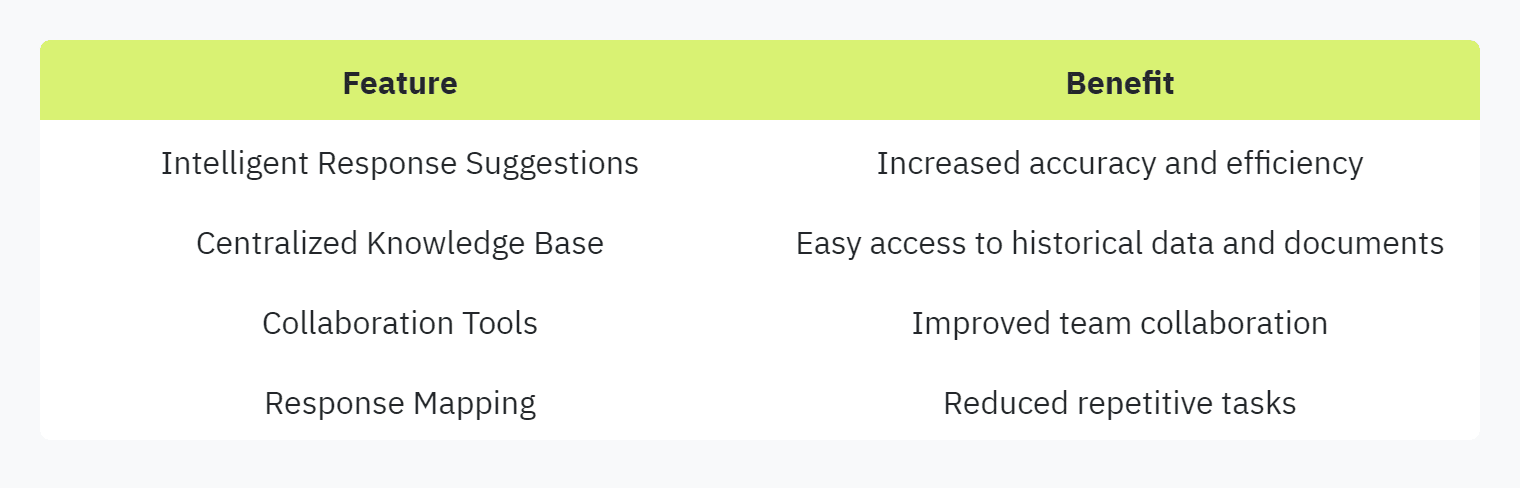
Key features of AI-powered automation tools include:
Intelligent Response Suggestions: Automatically suggests relevant responses based on historical data.
Centralized Knowledge Base: Maintains a repository of previous responses and documentation.
Collaboration Tools: Facilitates communication and collaboration among team members.
Response Mapping: Maps answers to similar questions, reducing repetitive work.
The following table highlights the impact of automation tools:
Organizations leveraging these tools, such as automating vendor security assessments, transform the task of managing vendor risk assessments into a streamlined process, saving time and resources while enhancing the overall quality of their vendor risk management program (Arphie).
For more insights into automation and AI, read our articles on ai in security questionnaires and automating security questionnaire responses.
Crafting Effective Questionnaires
Creating an efficient security questionnaire is crucial for assessing and verifying the security posture of vendors and partners. This section outlines best practices for using security frameworks as guides and paying attention to detail when forming questions.
Using Security Frameworks as Guides
To develop effective and efficient security questionnaires, leveraging well-known security frameworks is essential. Frameworks such as ISO 27001, NIST, and others provide comprehensive guidelines that help in structuring the scope and format of the questionnaire.
Common Industry Standard Frameworks:
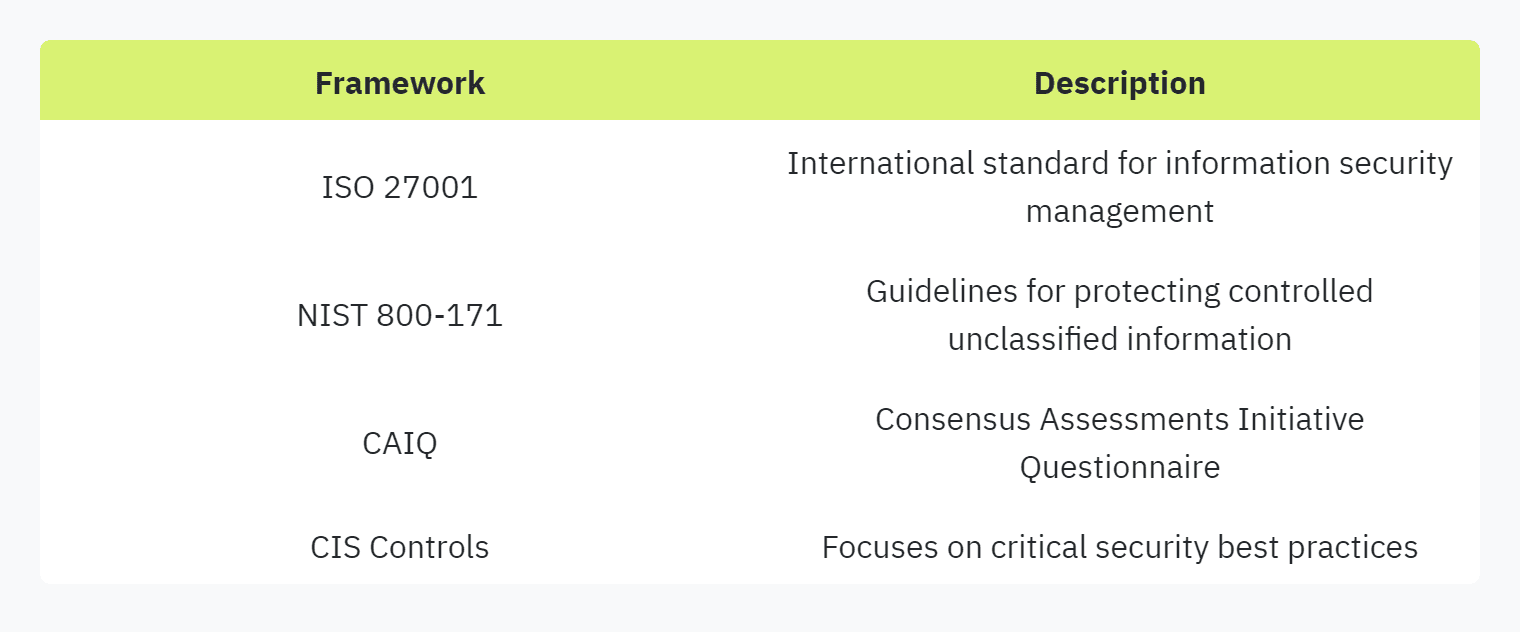
Using these frameworks as a baseline ensures that all critical security domains are covered. Additionally, templates such as the Consensus Assessments Initiative Questionnaire (CAIQ), CIS Critical Security Controls (CIS First 5 / CIS Top 20), and the Standardized Information Gathering Questionnaire (SIG/SIG-Lite) can serve as starting points for assessing a vendor's security posture.
For more details on compliance in security questionnaires, visit our article on compliance in security questionnaires.
Attention to Detail in Question Formation
Precise and well-crafted questions in a security questionnaire can make the difference between superficial and comprehensive security assessments. Key elements to consider when crafting questions include clarity, relevance, and alignment with security standards.
Important Aspects of Question Formation:
Clarity: Questions should be straightforward and unambiguous. Avoid technical jargon and ensure that the language is easily understood by respondents from different backgrounds. Simplified language can improve the response quality (LinkedIn).
Relevance: Each question should directly relate to the security controls or practices being assessed. Irrelevant or overly generic questions can lead to incomplete or inaccurate responses. Focus on specific vulnerabilities and compliance requirements relevant to your organization (Scytale).
Alignment with Security Standards: Ensure that the questions align with industry-standard security frameworks and regulations to maintain consistency and comprehensiveness. For example, questions related to software supply chain security should reflect standards like the NIST SSDF.
Detailed and Specific: Craft questions that require detailed responses, not just yes or no answers. This can provide better insights into a vendor’s security practices and vulnerabilities.
For more strategies on improving security questionnaire experience, refer to our guide on improving security questionnaire experience.
By applying these principles and leveraging established frameworks, organizations can create security questionnaires that are not only effective but also help build trust with clients and partners. For additional resources and tools, check out our article on tools to simplify security questionnaires.
Enter your email to start accelerating your sales today.
















