Using data insights to streamline security questionnaires
Share This Article

Understanding Security Questionnaires
Security questionnaires play a crucial role in managing cybersecurity risks within an organization, especially when dealing with third-party and fourth-party vendors. Understanding the purpose and components of these questionnaires can help security and compliance officers, IT managers, and SaaS startups streamline their processes and ensure robust risk management.
Purpose of Security Questionnaires
A security questionnaire is designed to help organizations identify potential cybersecurity weaknesses among third-party and fourth-party vendors, business partners, and service providers. By gathering detailed information about a vendor's security posture, these questionnaires deliver informed vendor risk assessments UpGuard.
Some key purposes of security questionnaires include:
Vendor assessment: Vetting vendors before onboarding helps organizations understand the vendors' susceptibility to breaches, enabling immediate action to mitigate risks. More on this can be found in our article on why security questionnaires are a nightmare.
Compliance: Ensuring vendors comply with various regulatory frameworks and regulations like GDPR, CCPA, HIPAA, etc.
Risk Identification: Identifying areas of potential cybersecurity weaknesses within the vendor’s systems and processes, which may impact the organization's security.
Components of a Security Questionnaire
Security questionnaires typically cover a wide range of topics related to a third party's security practices. Here are some common components:
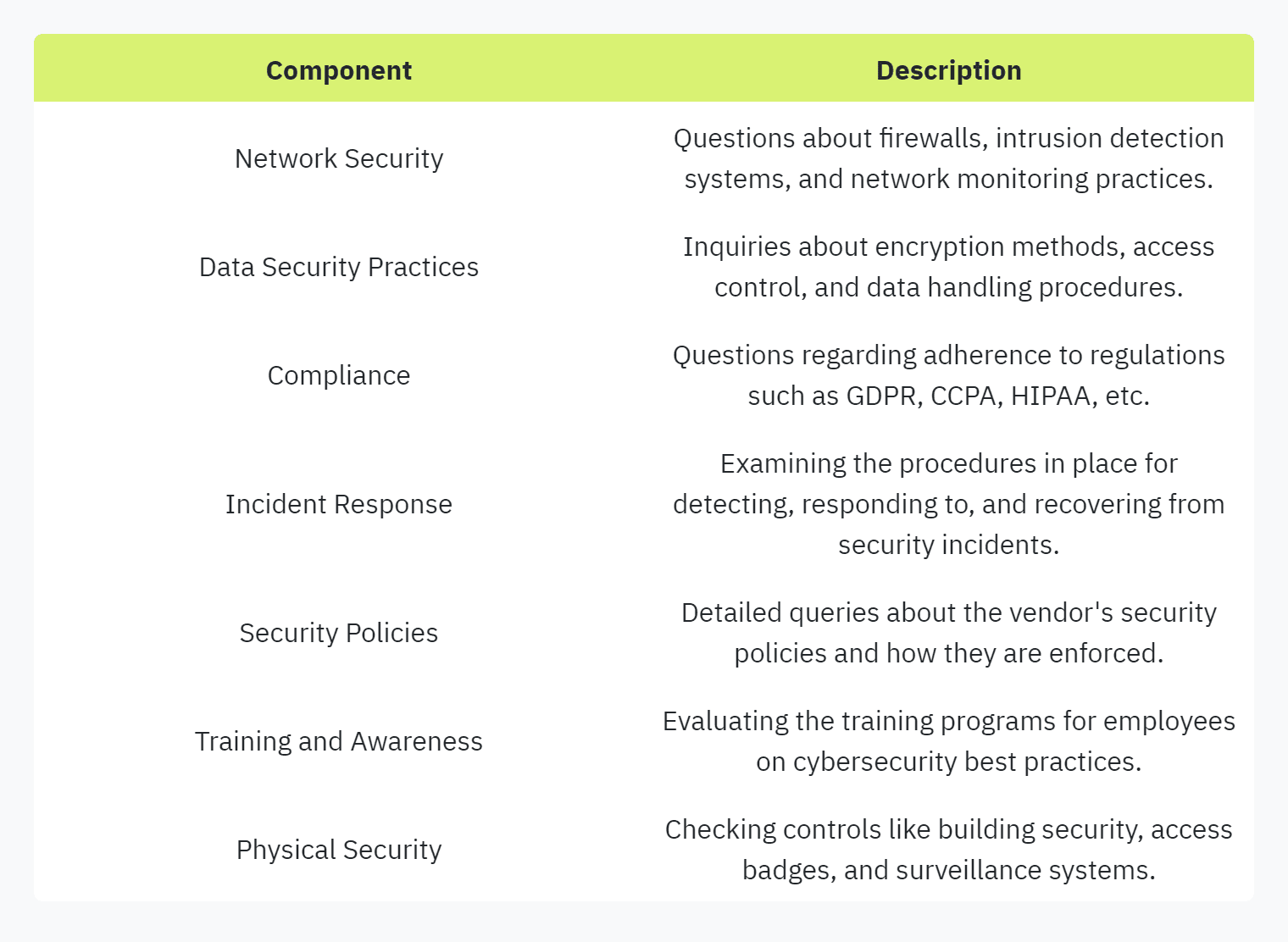
Understanding these components can help improve the process of automating security questionnaires, making it easier for organizations to manage their vendor risk programs effectively.
For those interested in diving deeper into these components, visit our article on components of a security questionnaire and best practices for security questionnaires.
By breaking down the essential aspects of a security questionnaire, organizations can better prepare and streamline their processes, ultimately leading to a more robust cybersecurity posture. Leveraging data insights in security questionnaires can further enhance their effectiveness, bringing clarity and efficiency to the vendor risk assessment process. Guided by correct data-driven practices, security and compliance officers can focus on implementation and continuous improvement, ensuring that their vendor risk management program stays ahead of potential threats.
Importance of Security Questionnaires
Security questionnaires play a vital role in maintaining organizational security and compliance. They are critical for evaluating vendor risk and mitigating cybersecurity threats.
Vendor Risk Assessment
A security questionnaire helps organizations identify potential cybersecurity weaknesses among third-party and fourth-party vendors, business partners, and service providers (UpGuard). By delivering informed vendor risk assessments, organizations can make more educated decisions about which vendors to onboard.
According to UpGuard, security questionnaires are essential for organizations to vet vendors before onboarding. This process helps in understanding which vendors are most likely to be breached, enabling immediate action to mitigate risks. The following table outlines the typical components assessed in a security questionnaire:
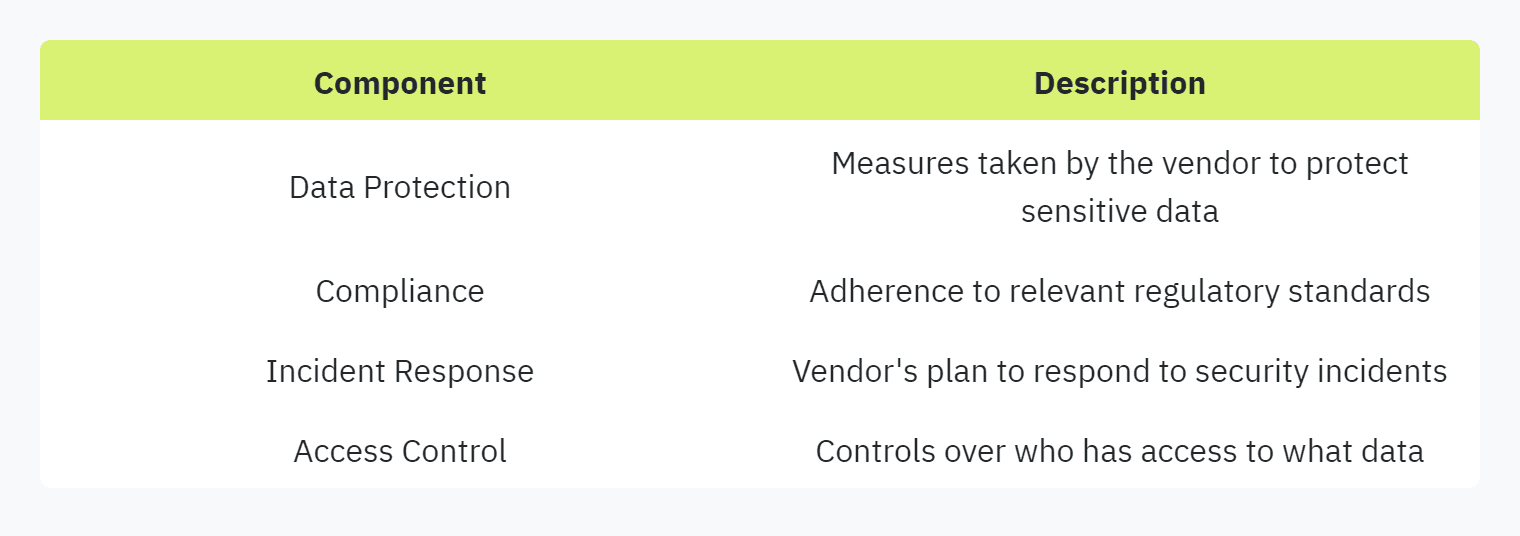
Incorporating other methods like security ratings, SOC 2 compliance, and continuous attack surface monitoring into the vendor risk management program can further enhance the assessment.
Mitigating Cybersecurity Risks
Security questionnaires are a proactive method for mitigating cybersecurity risks within an organization. They provide a standardized approach to evaluating the security practices and risks of vendors, partners, or service providers.
Automation of security questionnaires helps mitigate these risks more efficiently (Vendict). By streamlining the process, organizations can:
Save time and resources
Ensure more thorough assessments
Reduce human error
For example, automating the security questionnaire process can help identify vendors with inadequate security measures, enabling quicker remediation. For further reading on automation and its benefits, visit our article on automating security questionnaires.
In summary, incorporating [data insights in security questionnaires] is pivotal for both vendor risk assessment and mitigating cybersecurity risks. These questionnaires, particularly when automated, provide a comprehensive view of vendor security postures, allowing organizations to maintain robust security standards. For best practices and tools to simplify this process, refer to our articles on tools to simplify security questionnaires and best practices for security questionnaires.
Automation of Security Questionnaires
In the ever-evolving landscape of cybersecurity, automating security questionnaires is invaluable for organizations aiming to streamline their processes. Here we explore the benefits and challenges associated with automation.
Benefits of Automation
Automating the security questionnaire process can provide significant advantages, particularly for security and compliance officers, IT managers, and SaaS startups.
Efficiency and Speed: Automating the responses to security questionnaires can drastically reduce the time required to complete them. This speedy evaluation process facilitates faster vendor assessments and ensures timely responses (UpGuard).
Consistency and Accuracy: Automation ensures that responses are both comprehensive and consistent, reducing the likelihood of human error. Automation platforms that utilize AI and machine learning continuously update their knowledge bases to stay current with the latest security trends and regulations.
Resource Optimization: By automating repetitive tasks, valuable human resources can be freed up for more strategic activities. This is particularly significant given that security questionnaires are becoming increasingly complex and numerous.
Thorough Assessments: Automated systems can handle the intricate details of security questionnaires, ensuring thorough evaluations. This leads to a more robust vendor risk assessment process.
Challenges and Solutions
While the benefits of automating security questionnaires are clear, several challenges must be addressed to maximize the effectiveness of automation.
Customization vs. Standardization: One of the key challenges is finding the right balance between customized and standardized responses. Organizations need tools that offer flexibility while maintaining a high level of accuracy and relevance (Arphie).
Data Quality and Accuracy: Ensuring that the data used in automated responses is accurate and up-to-date is crucial. Regular audits and updates of the data repository can help maintain data integrity.
Integration with Existing Systems: Seamlessly integrating automation tools with current systems can be complex. Utilizing APIs and choosing compatible software can mitigate integration issues.
Evolving Threats and Regulations: The cybersecurity landscape is constantly changing, and regulations are continuously evolving. Leading automation platforms use AI and machine learning to update their knowledge base, ensuring that the automated security questionnaires remain current.
User Adoption and Training: Implementing new automation tools requires proper training and fostering user adoption. Comprehensive training programs and user-friendly interfaces can facilitate this transition.
To delve deeper into the practical steps of automating security questionnaires, check out our guide to automating security questionnaires. For more insights on how data insights can be leveraged for efficient questionnaire management, read our article on data-driven practices for security.
By addressing these challenges, organizations can successfully harness the power of automation to enhance their security posture and operational efficiency.
Data-Driven Practices for Security
Leveraging Data Insights
Organizations are increasingly recognizing the importance of data-driven decision making in their security processes. By harnessing data insights in security questionnaires, businesses can make objective decisions, supporting real-time data aggregation for pattern recognition and predictive analysis (Asana). To fully leverage data insights, companies should undertake specific steps:
Understanding the Company's Vision: Align security data analysis with the organizational goals.
Finding Data Sources: Identify relevant data from systems such as intrusion detection, prevention systems, firewalls, antivirus solutions, and log management systems.
Organizing Data: Centralize security data to allow comprehensive analysis.
Performing Data Analysis: Use data analytics tools to draw meaningful conclusions.
Drawing Conclusions: Translate data analysis into actionable insights.
Setting Measurable Goals: Establish metrics to monitor the effectiveness of implemented security measures.
Tools and technologies such as Business Intelligence (BI) software, data analytics tools like R and Python, and machine learning algorithms are instrumental in this process.
Enhancing Security Posture
Enhancing a company's security posture using data insights involves not only recognizing potential threats and risks but also proactively addressing them. By analyzing data, organizations can bolster their security measures, mitigate risks, and make informed decisions to safeguard their operations and assets (QR-Patrol).
Key actions include:
Identifying Threats and Vulnerabilities: Use data from varied security systems to detect any anomalies or potential vulnerabilities.
Centralizing Security Data: Aggregate data from different sources into one central location for a holistic view.
Proactive Risk Management: Translate data insights into proactive measures to preempt potential security breaches.
Continuous Improvement: Regularly analyze security data to continually enhance security protocols and measures.
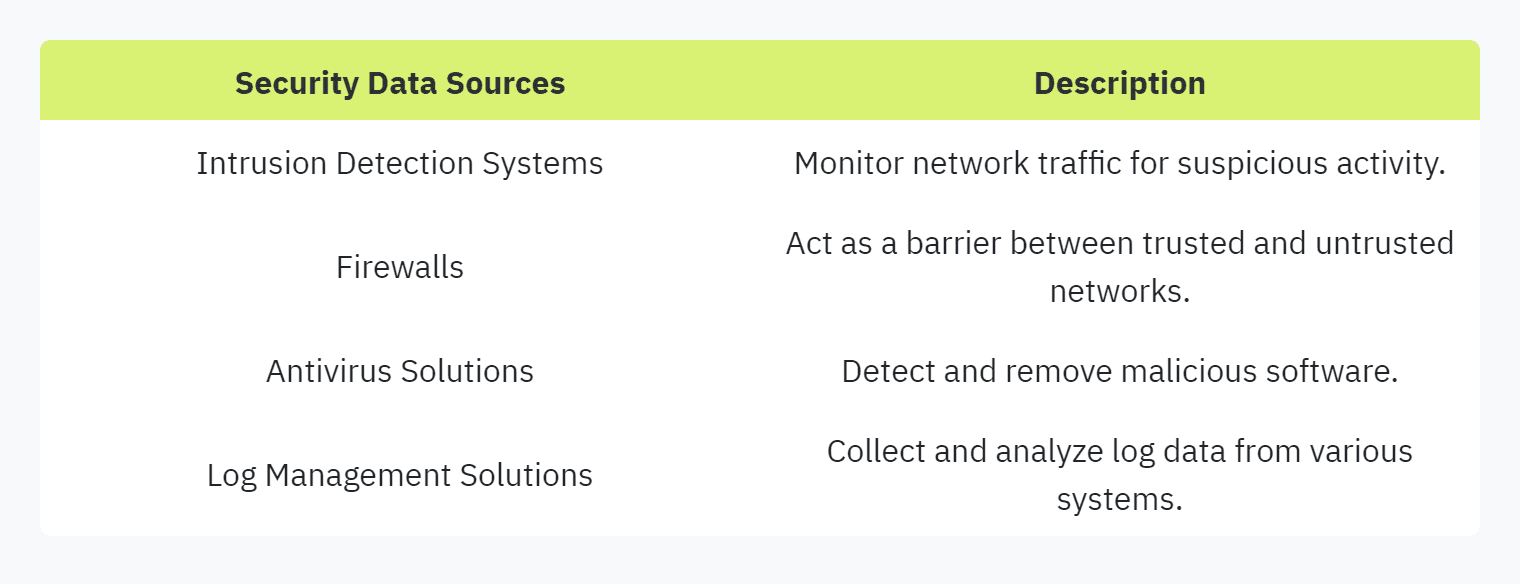
Incorporating data-driven practices not only strengthens security measures but also enhances the organization's overall security posture by staying ahead of potential threats.
For more insights and best practices on automating and leveraging data insights in security questionnaires, refer to our articles on automating security questionnaires, tools to simplify security questionnaires, and key metrics for security questionnaire automation.
Enter your email to start accelerating your sales today.
















