Understanding security questionnaires: making them easier to handle
Share This Article
Understanding Security Questionnaires
Purpose and Importance
Security questionnaires play a crucial role in the vendor review process by helping organizations identify potential risks and vulnerabilities. They aim to ensure that vendors meet an organization's security standards and align with its security goals (Vanta). These questionnaires help assess potential security threats and are a key tool in vendor risk management, enabling companies to make informed decisions about their third-party relationships.
The primary objectives of security questionnaires include:
Identifying Weaknesses: Uncovering potential cybersecurity weaknesses among vendors, partners, or service providers.
Ensuring Compliance: Ensuring vendors' information security practices align with internal and external requirements.
Risk Assessment: Delivering an informed vendor risk assessment to vet potential third-party risks.
For more details on best practices for security questionnaires, you can visit our comprehensive guide on best practices for security questionnaires.
Types of Security Questionnaires
Security questionnaires vary significantly in their focus and complexity, depending on the industry and specific security goals. Below are several common types:
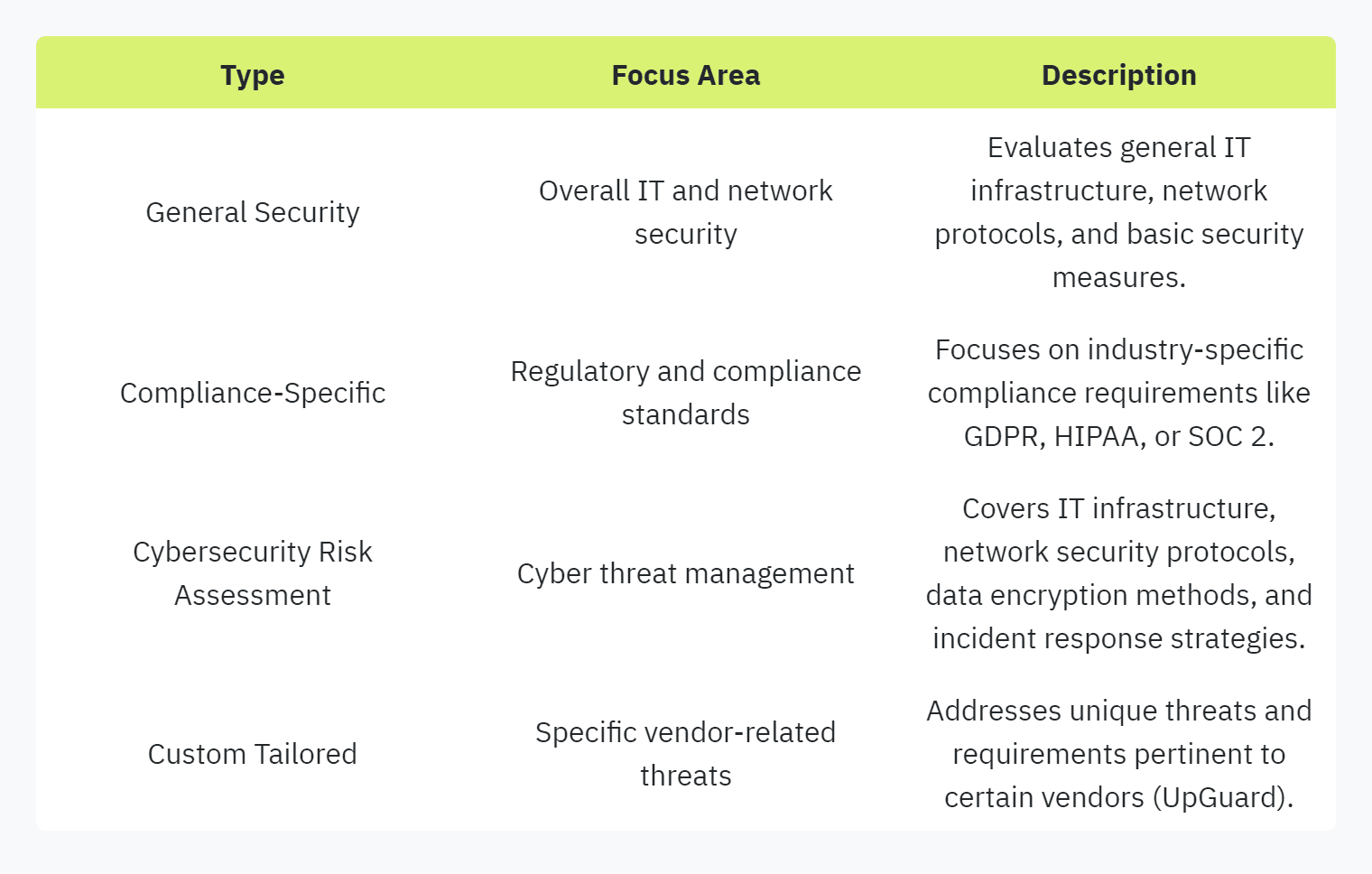
Security questionnaires often form part of a broader risk assessment strategy, which includes other evaluation methods such as security ratings, SOC 2 compliance, and continuous attack surface monitoring. Together, these tools provide a comprehensive overview of a vendor's security posture (UpGuard).
Understanding the different types of security questionnaires is essential for choosing the right approach for your organization's needs. By using industry-standard templates and customizing your questionnaires to address specific threats, you can create effective tools for vendor security assessments. To explore ways to streamline and automate this process, check out our article on automating security questionnaires.
For more information about the common challenges and frustrations with handling security questionnaires, you can visit our page on common frustrations with security questionnaires.
Key Components of Security Questionnaires
Security questionnaires are essential tools for assessing the security posture of third-party vendors and ensuring compliance with industry standards. They typically cover several crucial components, among which data encryption practices and vendor subcontractor management are key.
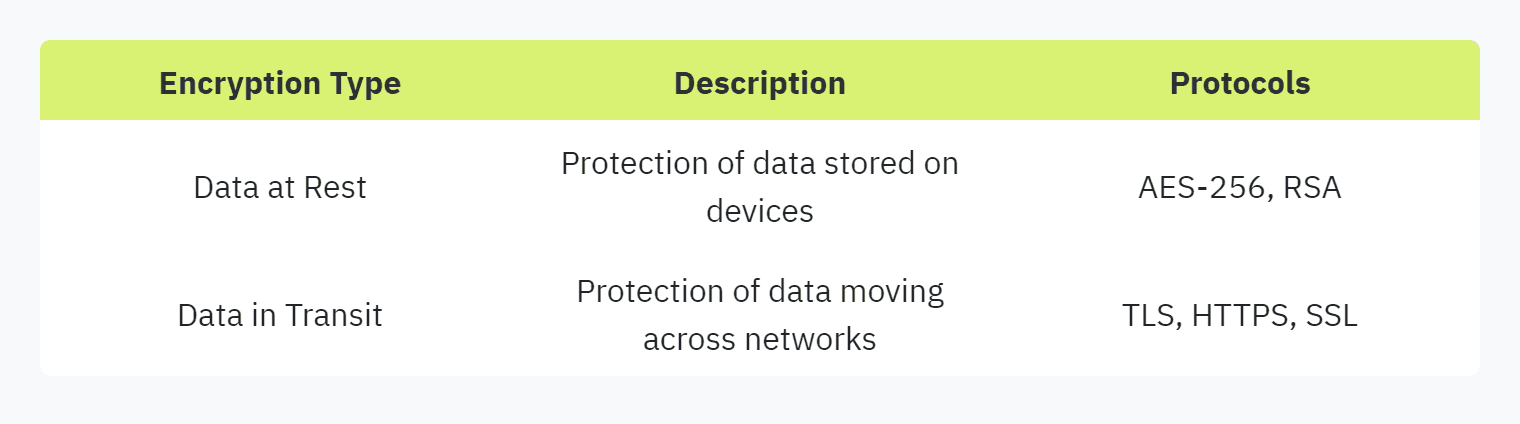
Data Encryption Practices
Data encryption is a critical factor in security questionnaires. Encryption practices aim to protect sensitive information by converting it into a secure format that cannot be easily breached. Organizations use various encryption methods to ensure data at rest and data in transit are safeguarded.
Common Data Encryption Criteria:
Encryption Algorithms: Vendors are often required to describe the algorithms they employ, such as AES-256, RSA, or SHA-256.
Data at Rest Encryption: Ensuring that data stored on servers, databases, and other storage devices is encrypted to prevent unauthorized access.
Data in Transit Encryption: Encrypting data as it moves across networks, including the use of protocols like TLS and HTTPS.
For more information on data privacy in security questionnaires, please refer to our detailed article.
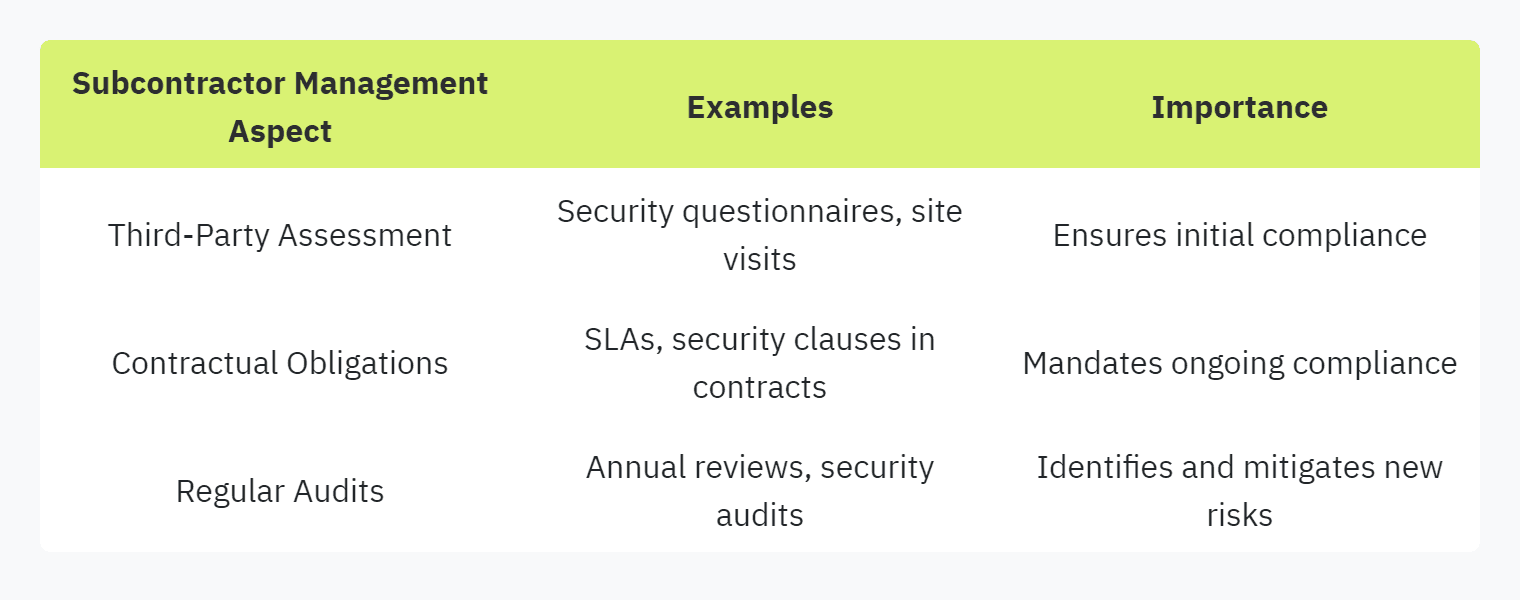
Vendor Subcontractor Management
Managing subcontractors is another critical element assessed through security questionnaires. When vendors use subcontractors, it’s imperative that these third parties adhere to the same security standards. This ensures a consistent security posture throughout the supply chain.
Typical Subcontractor Management Criteria:
Third-Party Assessment: Vendors must have a process to assess and vet subcontractors’ security practices.
Contractual Obligations: Ensuring that subcontractors are contractually bound to maintain security standards consistent with the primary vendor.
Regular Audits: Conducting periodic audits and assessments of subcontractors to ensure ongoing compliance and identify potential security gaps.
For additional insights on best practices for subcontractor management, visit our article on automating vendor security assessments.
To summarize, both data encryption practices and vendor subcontractor management are essential components of effective security questionnaires. They provide a comprehensive view of a vendor's security measures and help organizations mitigate potential risks. For more details on creating an effective questionnaire, check our guide on best practices for security questionnaires.
By focusing on these critical areas, organizations can ensure that their vendor assessments are thorough and effective, thereby protecting sensitive information and maintaining robust security standards. For further reading, explore how to streamline your processes with our resources on automation and streamlining process and tools to simplify security questionnaires.
Best Practices for Security Questionnaires
Effectively managing security questionnaires is crucial for organizations to ensure robust vendor vetting and risk mitigation. This section explores best practices to create efficient questionnaires and streamline the entire process.
Creating Effective Questionnaires
Security questionnaires serve as a critical tool for assessing the security posture of vendors, helping organizations identify potential vulnerabilities and risks. To make these questionnaires effective, several best practices should be considered:
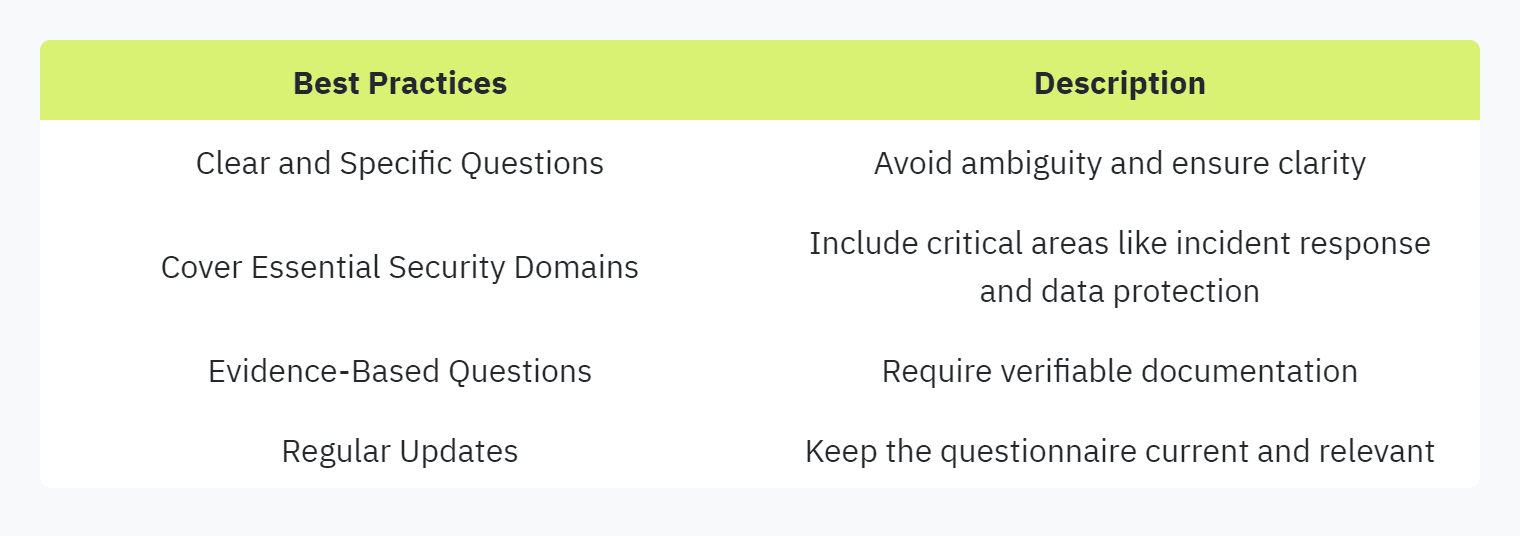
Clear and Specific Questions: Ensure that each question is clear, concise, and directly addresses specific security concerns. Avoid ambiguous questions that may lead to misunderstanding or incorrect responses.
Include Essential Security Domains: Cover essential security aspects such as incident response procedures, data encryption practices, and vendor subcontractor management.
Use Evidence-Based Questions: Design questions that require evidence-based answers. Request supporting documentation such as SOC 2 compliance reports or security ratings to verify responses (UpGuard).
Update Regularly: Regularly review and update the questionnaire to reflect current security standards and emerging threats. This keeps the questionnaire relevant and comprehensive.
For more detailed guidelines, visit our article on best practices for security questionnaires.
Automation and Streamlining Process
Automation plays a pivotal role in managing security questionnaires more efficiently, reducing human error and saving time. Here's how organizations can automate and streamline the process:
Automated Questionnaire Distribution: Use software solutions to automate the distribution of security questionnaires to vendors. This ensures timely dissemination and tracking of responses.
Centralized Platform: Implement a centralized platform where all security questionnaire data is stored and managed. This facilitates easy access, tracking, and analysis.
Template Libraries: Utilize template libraries for common security frameworks and compliance standards. This reduces the time spent on creating questionnaires from scratch.
Pre-Filled Responses: Use machine learning and AI to pre-fill responses based on previous data, reducing vendor workload and speeding up the process (Akitra).
Continuous Monitoring and Updates: Automated systems can continuously monitor vendor responses and alert when updates or re-evaluations are due (UpGuard).

For more on leveraging technology, check out our guide on automating security questionnaires and tools to simplify security questionnaires.
Following these best practices can lead to more efficient and effective management of security questionnaires. By combining clear and focused questions with automation processes, organizations can significantly improve their security assessment and risk mitigation efforts. More information on streamlining security questionnaires can be found on our website.
Security Questionnaires in Risk Management
Security questionnaires play a pivotal role in risk management, particularly in the domains of vendor due diligence and complementary risk assessment methods.
Vendor Due Diligence
Performing due diligence on vendors is a crucial step when entering new third-party partnerships. These questionnaires aid in managing risks such as data breaches, regulatory action, financial consequences, litigation, reputational damage, and loss of customers. To ensure comprehensive assessment, security questionnaires typically cover:
Data protection measures
IT infrastructure security
Compliance with industry standards (e.g., SOC 2, ISO 27001)
Policies to safeguard sensitive information
These assessments help in aligning vendors with a company's security goals, effectively managing potential risks. A detailed process of vendor due diligence can be explored further in our article on best practices for security questionnaires.
Complementary Risk Assessment Methods
Security questionnaires are indispensable tools for risk assessment in cybersecurity. They offer an organized way to evaluate key security aspects, from incident response procedures to data protection policies (Akitra). Additionally, they help ensure compliance with various security standards like NIST, ISO, PCI DSS, and FedRamp.
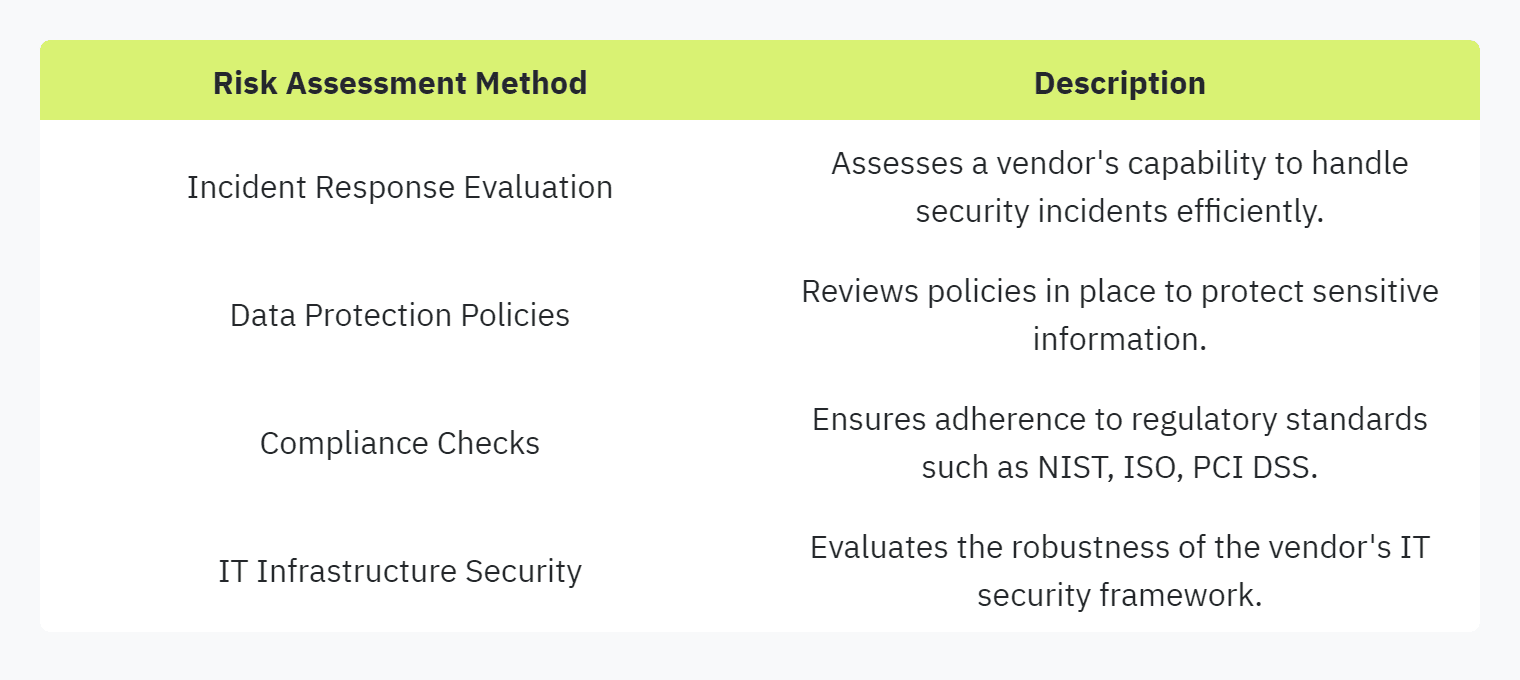
By integrating these complementary methods with traditional security questionnaires, companies can enhance their overall risk management strategy. For more insights into improving the efficiency and effectiveness of these methods, refer to our article on streamlining security questionnaires.
Learn more about how automation and AI can further enhance these practices by reading our detailed guides on automating security questionnaires and AI in security questionnaires.
Enter your email to start accelerating your sales today.
















