Why security questionnaires are a nightmare and how to fix them
Share This Article

Importance of Security Questionnaires
Security questionnaires are essential tools in the modern digital landscape where data breaches and cyber threats are increasingly common. They help companies assess how well they or their partners protect their digital information and ensure compliance with security standards.
Ensuring Data Protection
Ensuring the protection of data is paramount as businesses increasingly rely on outside vendors and cloud services. Security questionnaires play a crucial role in confirming that these partners handle the company’s sensitive information safely. By assessing various aspects such as data encryption, access control, and incident response plans, security questionnaires provide a robust measure of a vendor's security posture.
In the digital age, where data breaches can lead to severe legal and financial repercussions, these questionnaires serve as a preventive measure. They identify vulnerabilities and ensure that all parties adhere to specific security standards, which helps in mitigating risks and maintaining customer trust. For more on data protection practices, check out our article on data privacy in security questionnaires.
Partner Compliance Evaluation
Security questionnaires are integral in evaluating the compliance of partners handling sensitive data. In a world where companies collaborate with numerous vendors and third-party service providers, ensuring that these partners adhere to security standards is vital. According to Vendict, such evaluations help in protecting a company's data and safeguarding it from potential legal and financial risks due to security breaches.
Organizations use security questionnaires to verify that vendors maintain suitable measures to identify, prevent, and respond to cyber threats. A strong third-party risk management program is crucial for preparing for potential attacks and ensuring that all security protocols are followed. For more insights into partner compliance, read our article on compliance in security questionnaires.
To visualize the significance, consider the following table illustrating the common threats mitigated by ensuring partner compliance:
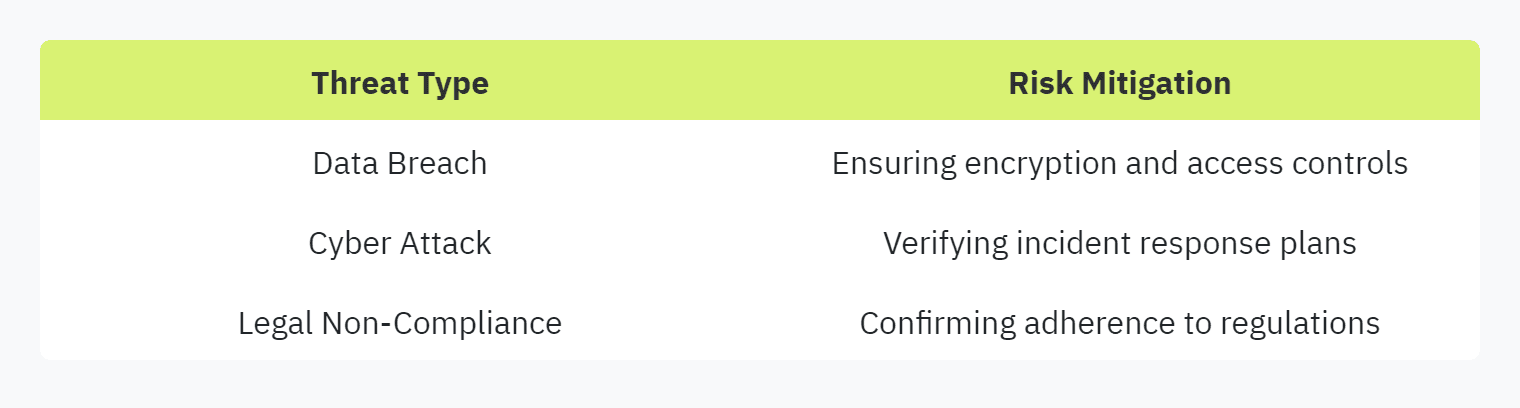
Effective third-party risk management, involving well-framed and clear security questionnaires, minimizes disruptions and fosters positive relationships with vendors. Discover more about improving your questionnaire process in our article on streamlining security questionnaires.
Understanding the importance of security questionnaires helps in realizing why companies consider them indispensable. Explore our detailed guide on understanding security questionnaires for further information.
Types of Security Questionnaires
Security questionnaires are essential tools for ensuring compliance and data protection. They come in various types, each suited for different purposes, such as standardized, customized, third-party vendor, and regulatory compliance questionnaires.
Standard vs. Customized
Security questionnaires can be broadly categorized into standard and customized types. Both serve the purpose of assessing the security posture of vendors but differ in their approach and application.
Standard Questionnaires:
Standard questionnaires are pre-defined sets of questions used to gather detailed information from vendors. They are designed to cover a wide range of security and compliance aspects, making them suitable for most industries. Examples include the Standard Information Gathering (SIG) questionnaire and frameworks from the National Institute of Standards and Technology (NIST).

Standard questionnaires are valuable for situations where a consistent and repeatable assessment process is required. They ensure that all vendors are evaluated against the same criteria, making it easier to compare responses and identify any potential risks.
Customized Questionnaires:
Customized questionnaires are tailored to specific organizational needs, taking into account unique security requirements and risks. These are particularly useful for organizations with specialized needs or industries with specific regulatory requirements.
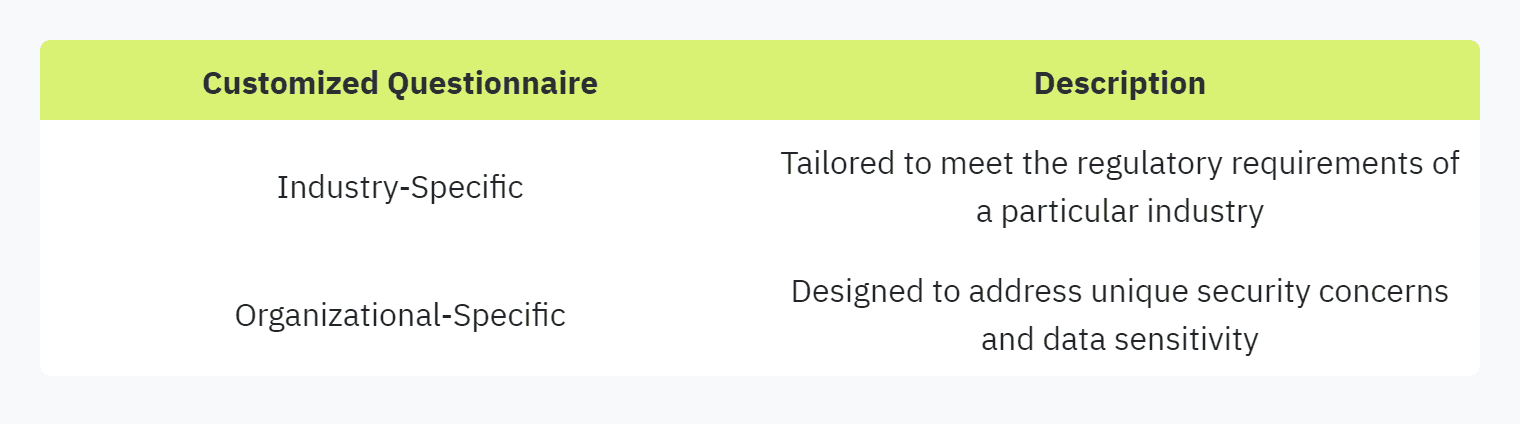
Customized questionnaires allow organizations to focus on areas of particular concern, ensuring that they receive relevant and precise information. However, they can be more time-consuming to create and manage, particularly without specialized tools or automation.
Third-Party Vendor vs. Regulatory
Security questionnaires can also be categorized based on their target, such as third-party vendor assessments or regulatory compliance questionnaires.
Third-Party Vendor Questionnaires:
Third-party vendor questionnaires are used to evaluate the security posture of external partners and service providers. These questionnaires help organizations understand the risks associated with their vendors and ensure that they have appropriate security measures in place.
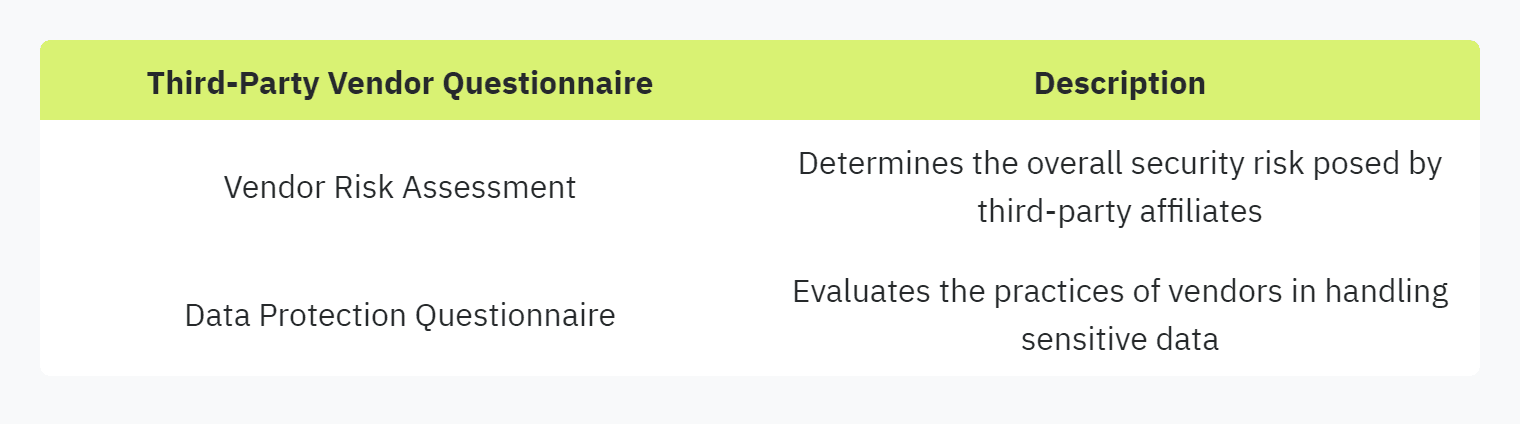
Using third-party vendor questionnaires is considered a cybersecurity best practice, aiding in the selection of secure and compliant partners. These questionnaires help in identifying any vulnerabilities that could threaten the integrity and security of organizational data.
Regulatory Compliance Questionnaires:
Regulatory compliance questionnaires are designed to ensure that an organization and its partners comply with applicable laws and industry regulations. These questionnaires focus on specific regulatory requirements, making sure that all involved parties adhere to mandated security standards.

Regulatory compliance questionnaires are essential for organizations operating in highly regulated industries, such as finance and healthcare. These assessments protect against legal liabilities and ensure operational integrity by mandating adherence to established guidelines.
By understanding the different types of security questionnaires, organizations can better navigate the complexities of why security questionnaires are a nightmare and implement effective measures to enhance their security posture. For more information on automating these processes, visit our guide on automating security questionnaires.
Automation Benefits in Questionnaires
Automation in the realm of security questionnaires provides multiple benefits, streamlining the process of risk management and enhancing efficiency, accuracy, and speed.
Efficiency in Assessments
Automating security questionnaires can vastly improve the efficiency of assessments. In the modern digital landscape, data breaches and cyber threats are increasingly common, requiring organizations to frequently assess how well they and their partners protect digital information. This process can be streamlined through automation, allowing for quicker and more thorough evaluations (Vendict).
A key area where automation enhances efficiency is in managing large volumes of questionnaires. Automation tools can handle the complex and numerous assessments that businesses undergo, ensuring that essential security checks are not overlooked.
Consider the following comparison:
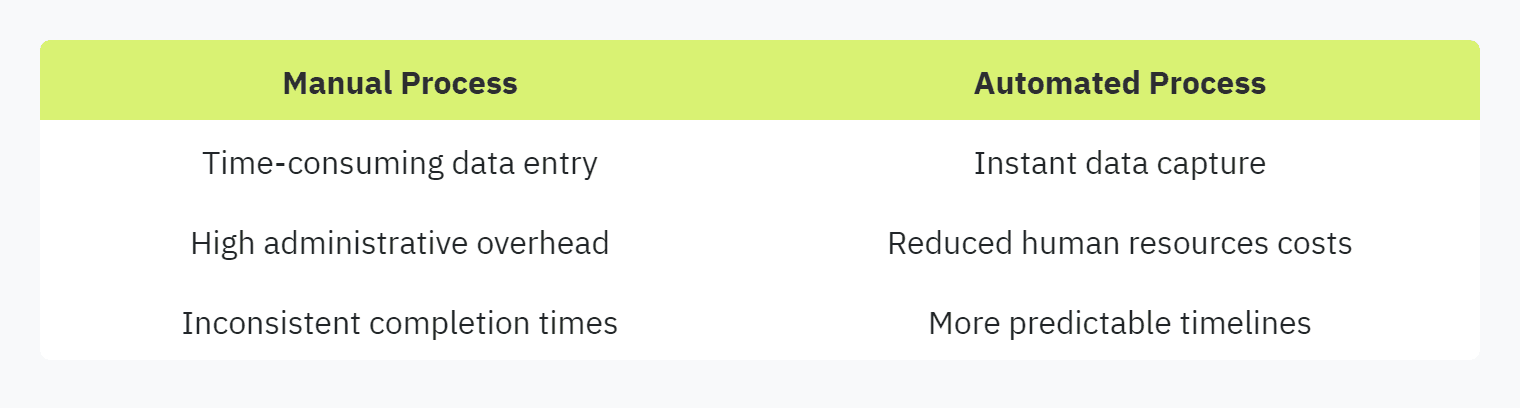
For additional information on enhancing efficiency in security questionnaires, explore our section on efficient security questionnaires.
Accuracy and Speed Enhancement
Beyond efficiency, automation significantly enhances the accuracy and speed of security questionnaire processes. Manual questionnaire handling poses a high risk of human errors, which can compromise the accuracy of the assessments. By automating these processes, errors are minimized, ensuring more reliable results.
Regarding speed, automating security questionnaires eliminates the time-consuming nature of manual processes. Automation tools can quickly analyze and process responses, providing faster turnaround times without compromising on thoroughness.
The benefits of accuracy and speed can be seen in the table below:
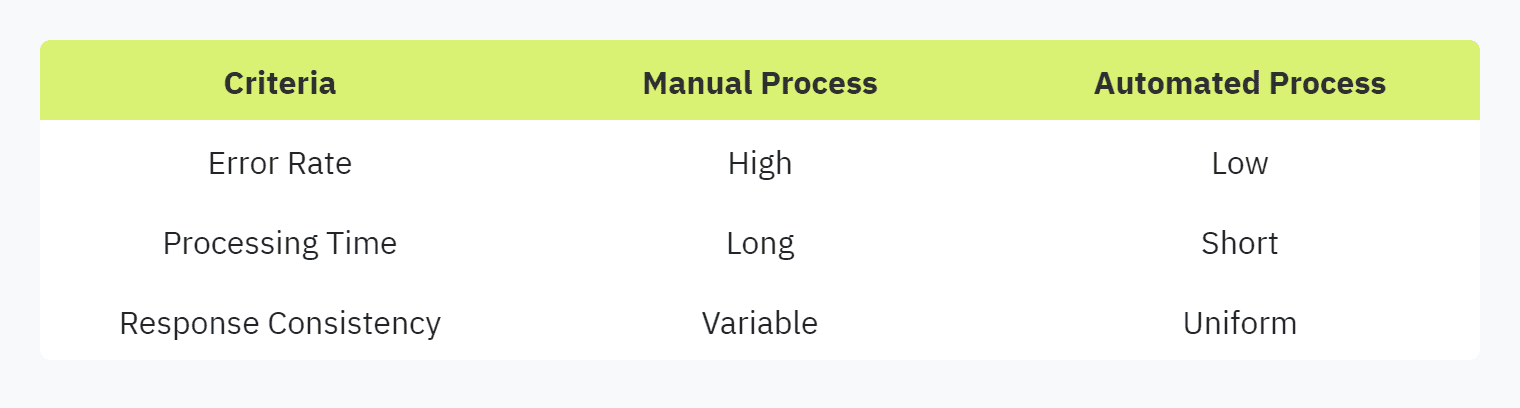
For more insights on how automation improves security questionnaires, read our article on automating security questionnaires.
Automation acts as a proactive measure against potential risks. By streamlining the security questionnaire process, it provides a layer of protection that keeps organizations ahead in their risk management endeavors (Vendict). This proactive approach is crucial given the increasing frequency of large-scale cyberattacks, which saw a 62% increase in industries such as oil and gas, food, and IT over the past year (OneTrust).
For further reading on this proactive approach, visit our section on ai in security questionnaires.
By automating the security questionnaire process, organizations can improve efficiency, accuracy, and speed, ultimately enhancing their overall security posture. For a comprehensive guide on how to implement these practices, explore our guide to automating security questionnaires.
Challenges in Manual Questionnaire Processes
Manual processes for completing security questionnaires present several challenges that render them inefficient and error-prone. These issues contribute significantly to the common frustrations experienced by security and compliance officers.
Time-Consuming Nature
One of the primary drawbacks of manual security questionnaire processes is their time-consuming nature. Companies frequently receive extensive spreadsheets, often containing hundreds of questions that need meticulous attention and detailed responses (Vendict). This process involves numerous stakeholders, each contributing to different sections of the questionnaire, adding to the complexity and length of time required.
The continuous need to respond to multiple clients or vendors further exacerbates the issue. Each response must be tailored to specific requirements, which can vary widely. As cybersecurity protocols evolve, updating the responses to reflect the latest security measures and compliance standards becomes an additional time burden.
Here's a table to illustrate the time typically spent on manual questionnaires compared to automated processes:

Source: Vendict
For strategies to reduce this time commitment, see our guide on reducing time to complete security questionnaires.
Risk of Human Errors
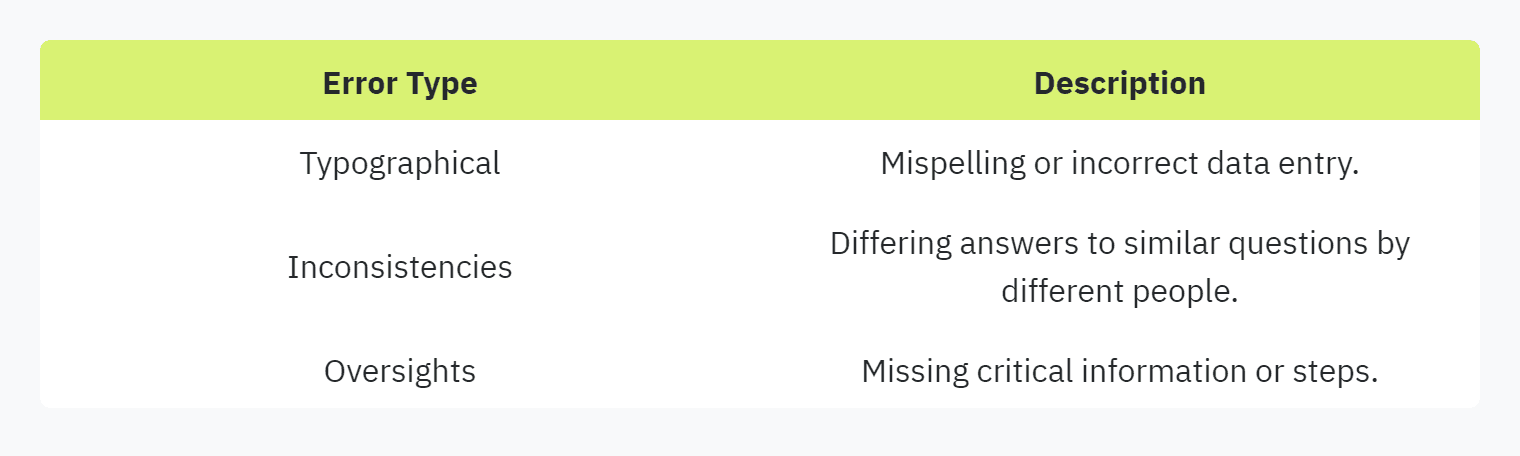
Manual completion of security questionnaires is also highly susceptible to human errors. These errors can arise from several factors:
Data Entry Mistakes: Transferring information manually between documents often leads to typographical errors and inaccuracies.
Inconsistent Responses: Different individuals may interpret and answer questions inconsistently, leading to contradictory responses that can damage credibility.
Oversights: Important details may be inadvertently omitted, especially when the questionnaire is lengthy and complex (OneTrust).
These errors can have serious repercussions, including failed compliance checks or security audits, and may even impact vendor relationships (Underestimating the Importance of Compliance in Security Questionnaires).
Example of Common Human Errors in Manual Processes:
To address these issues, many organizations are turning to automated solutions, which can significantly reduce the risk of human errors. Explore how automation can improve accuracy in our section on automating security questionnaires.
These challenges highlight why security questionnaires are often seen as a nightmare. By embracing modern technologies and practices, companies can alleviate many of these issues, streamlining the process and enhancing overall efficiency. For more insights on improving the experience, visit our page on improving security questionnaire experience.
Future of Security Questionnaires
Embracing Automation Technologies
As organizations extend their digital operations, automating security questionnaires becomes more essential to ensure third-party vendors comply with security standards (Vendict). Automation enhances efficiency, accuracy, and scalability, making it possible to manage numerous vendor assessments with minimal human intervention (automating security questionnaires).
Key benefits of automation include:
Efficiency: Automated systems can handle large volumes of questionnaires quickly.
Accuracy: Reduces human errors and ensures consistent assessment criteria.
Scalability: Can easily manage an increasing number of assessments.
Implementing automation technologies also streamlines the overall process, allowing security and compliance officers to focus on more strategic tasks. For insights on how to achieve this, read our guide to automating security questionnaires.
Adoption of Modern Practices
Modern practices are essential for staying ahead in security questionnaire management. Implementing international standards like ISO 27001 for information security management systems ensures robust data protection (Vanta). Key components of ISO 27001 implementation include:
Risk Assessments: Identifying potential security threats.
Security Controls: Applying measures to mitigate identified risks.
Employee Training: Regularly educating staff on security protocols.
External Audits: Undergoing certification processes to verify compliance.
Organizations are also incorporating advanced technologies like AI to enhance the automation process. AI can predict potential risks and streamline questionnaire responses, making it a valuable tool in modern security practices.
For more details on integrating these modern practices, visit our section on integrating security questionnaires.
By embracing automation technologies and adopting modern security practices, organizations can effectively manage security questionnaires, ensure compliance, and foster trust with partners and customers. For further reading on improving the security questionnaire experience, check out our article on improving security questionnaire experience.
Risk Management and Vendor Relationships
Security questionnaires are critical for evaluating potential risks and forming trustworthy vendor relationships. Here, we will discuss cybersecurity best practices and methods for assessing third-party risks.
Cybersecurity Best Practices
Ensuring strong cybersecurity requires organizations to adhere to several best practices. These practices help in safeguarding sensitive information and maintaining compliance with industry standards. Understanding why security questionnaires are indispensable aids in identifying the right practices for enhancing security measures:
Regular Security Training: Keeping employees informed about the latest threats and security protocols helps prevent potential breaches.
Robust Access Controls: Limiting access based on roles ensures that only authorized personnel can handle sensitive data.
Regular Audits and Assessments: Conducting periodic security assessments helps identify vulnerabilities and maintain compliance.
Implementing Strong Encryption: Utilizing encryption for data at rest and in transit protects against unauthorized access.
Multi-Factor Authentication (MFA): Requiring multiple forms of verification enhances security beyond basic password protection.
For more guidance, refer to our best practices for security questionnaires.
Evaluating Third-Party Risks
Assessing the security posture of third-party vendors is crucial for mitigating potential threats. As businesses increasingly collaborate with external entities, ensuring these partners uphold stringent security standards becomes imperative (Vendict). Highlighted below are key steps in evaluating third-party risks:
Comprehensive Questionnaires: Utilizing detailed security questionnaires helps in gauging the vendor’s adherence to security protocols (Vendict).
Review Security Certifications: Verification of ISO 27001, SOC 2, or other relevant certifications provides insight into the vendor’s compliance with security standards.
Monitor Vendor Performance: Continuously tracking and evaluating the vendor’s security measures ensures ongoing compliance and risk mitigation.
Cyber Insurance: Check if the vendor holds cyber insurance to cover potential losses from data breaches.
For actionable insights and strategies, consider our guide to automating security questionnaires and automating vendor security assessments.
Using security questionnaires effectively helps in creating a robust risk management framework and maintaining strong vendor relationships. For additional tips and tools, explore our articles on streamlining security questionnaires and automation technologies in security questionnaires.
Enter your email to start accelerating your sales today.
















