Training your team to make security questionnaire automation a success
Share This Article

Streamlining Security Questionnaires
Introduction to Questionnaire Automation
Completing security questionnaires can be a daunting task for organizations, often requiring significant time and resources. Introducing Questionnaire Automation is a solution designed to streamline this process by automating responses, ensuring both speed and accuracy. These questionnaires cover a broad range of topics, including physical security, network security, data protection, incident response, access control, and security policies and procedures.
Accurate and up-to-date responses are critical, as outdated or inaccurate information can lead to legal challenges for the vendors involved. Questionnaire Automation utilizes advanced technology to provide security questionnaire answers quickly and accurately, saving valuable time for security and compliance officers and IT managers (Vanta).
Benefits of Vanta's Automation Tool
Vanta's Questionnaire Automation tool addresses many challenges associated with completing security questionnaires, offering several benefits to organizations:
Time-Saving: By automating the response process, organizations can save significant time. Instead of manually answering each question, the automation tool provides quick and accurate answers in minutes.
Resource Efficiency: Automation helps reduce the manpower needed to complete security questionnaires, freeing up resources for other important tasks. This efficiency is particularly valuable for SaaS startups that may have limited staff.
Accuracy and Completeness: The tool ensures that responses are accurate and complete by syncing with the latest policies and documents. This feature helps maintain the reliability of responses and avoids the risk of providing outdated information (Vanta).
Enhanced Compliance: By using the most recent policies and documents, the tool helps ensure compliance with security standards. This is crucial for maintaining trust with customers and meeting regulatory requirements (Vanta).
To illustrate the time-saving aspect, consider the following comparison:
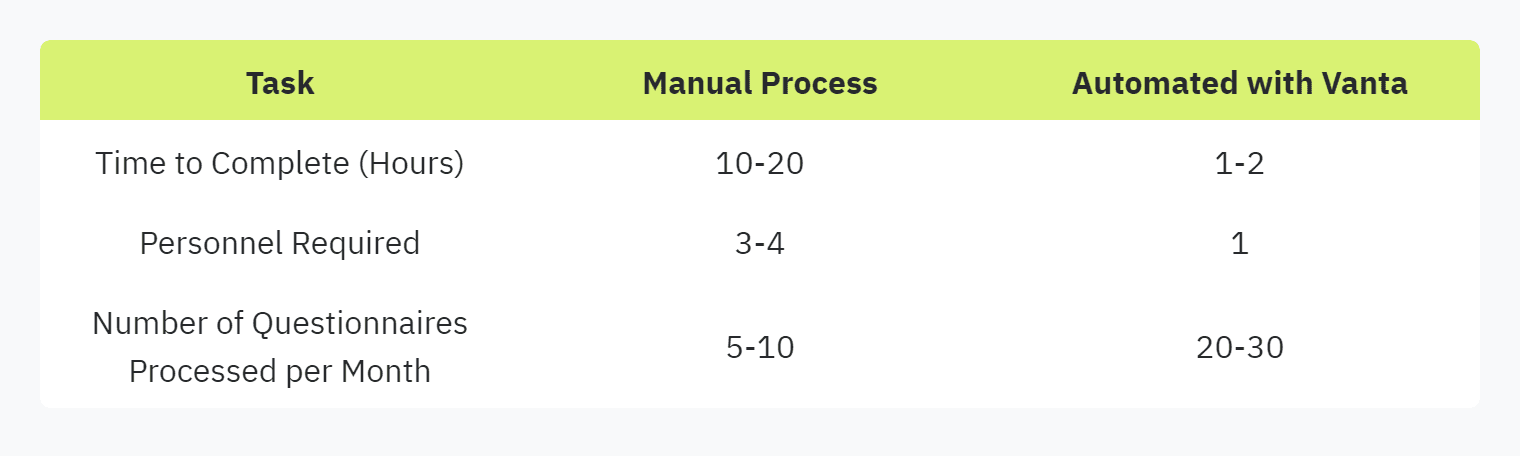
This table shows the significant reduction in time and resources achieved through automating security questionnaire responses.
For more information on how to streamline your security questionnaire process, explore our guide on efficient security questionnaires, and learn about the best tools to simplify security questionnaires.
Importance of Security Compliance
Security compliance is critical for organizations that wish to safeguard their data and maintain trust with their stakeholders. Understanding the various types of security questionnaires and the risks associated with outdated information is essential for ensuring robust security measures.
Types of Security Questionnaires
Security questionnaires are key tools in evaluating a vendor's security posture. They encompass a wide range of topics, including:
Physical security
Network security
Data protection
Incident response
Access control
Security policies and procedures
Each of these questionnaires is designed to assess specific aspects of a vendor's security framework. For instance, a questionnaire focused on network security will evaluate the controls and measures an organization has implemented to protect against network threats. For more information on the nuances of each type, visit our page on understanding security questionnaires.
Risks of Outdated Information
The accuracy of responses in security questionnaires is crucial. Outdated or inaccurate information can pose significant risks, both legally and operationally:
Legal Challenges: Inaccurate or outdated responses can lead to misrepresentation of an organization’s security posture, potentially resulting in legal disputes or regulatory fines.
Operational Risks: Inaccurate information can result in gaps in security defenses, leaving the organization vulnerable to breaches and other cyber threats.
A table summarizing the risks of outdated information:

Organizations must implement continuous monitoring and regular updates to ensure that their security information remains current and accurate. Automating the process through tools like Vanta can help mitigate these risks by ensuring real-time updates and reducing the chance of human error (Secureframe).
For detailed strategies on maintaining accurate security data, refer to our article on efficient security questionnaires. Emphasizing up-to-date information in questionnaires is vital for effective Third-party Risk Management (TPRM) and overall security compliance excellence. Deepen your understanding by exploring different TPRM frameworks.
Tools for Cybersecurity
Understanding the essential security tools for startups is critical in developing a robust cybersecurity framework. Automation plays a key role in incident response, enhancing the efficiency and effectiveness of threat mitigation.
Essential Security Tools for Startups
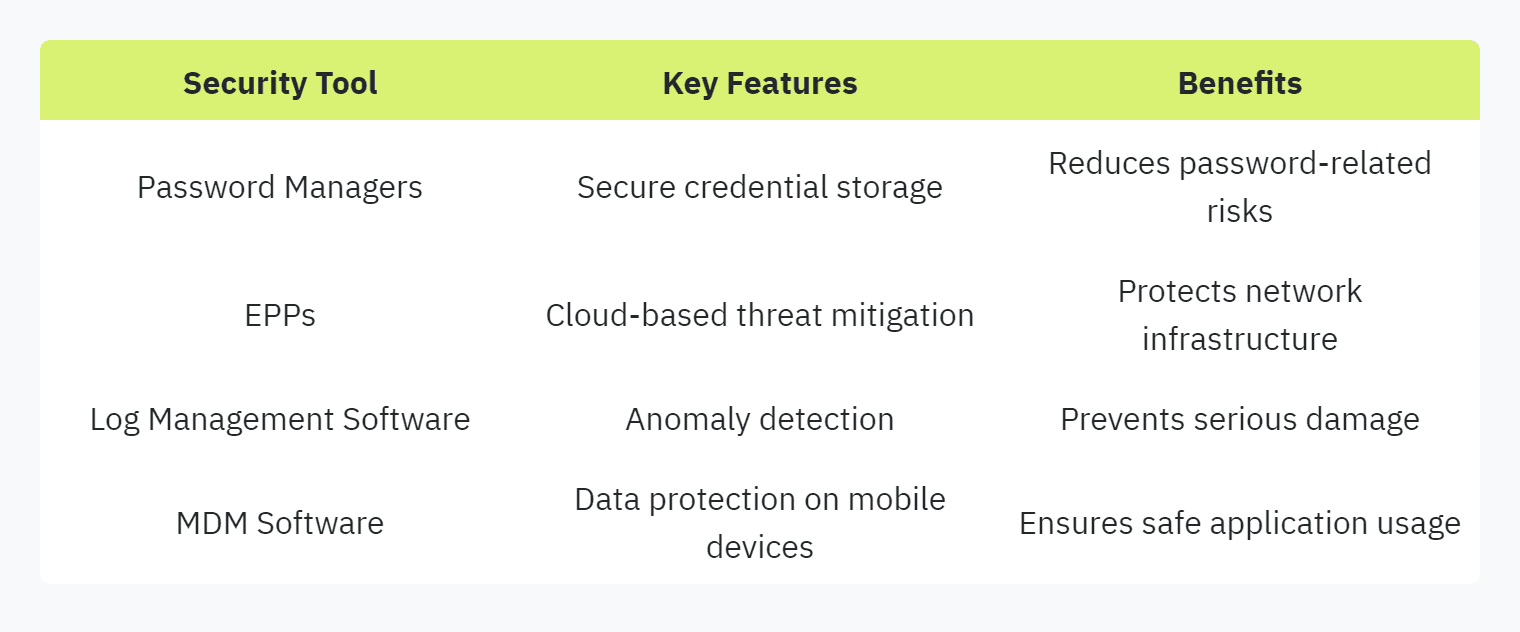
Startups often face numerous challenges in securing their digital environments. To address these, they can utilize a variety of essential security tools:
Password Managers: Password managers efficiently store and manage multiple credentials securely. They provide cost-effective and reliable solutions for credential storage, reducing the risks associated with weak or reused passwords.
Endpoint Protection Platforms (EPPs): These platforms offer comprehensive solutions to mitigate advanced threats. EPPs come with cloud-based management systems, providing a unified approach to protect the network infrastructure from various cyber threats (Vanta).
Log Management Software: This software is essential for detecting unusual activities within digital environments. It helps track and respond to anomalies promptly, thus preventing serious damage.
Mobile Device Management (MDM) Software: MDM software safeguards organizational data on mobile devices. It ensures data protection, secure application usage, and continuous device monitoring (Vanta).
For more tools to simplify security questionnaires, check out our guide on tools to simplify security questionnaires.
Automation in Incident Response
The role of automation in incident response cannot be overstated. It aids in real-time threat identification, rapid containment, and mitigation of security breaches promptly, thereby reducing dwell time and minimizing potential damage (Centraleyes). Automation tools streamline incident response by eliminating manual processes and enhancing efficiency.
Real-time Threat Identification: Automated systems continuously monitor network activities, instantly identifying and flagging threats as they occur. This allows for immediate awareness and action.
Rapid Containment: Quick containment is crucial in preventing the spread of a security incident. Automation enables rapid response protocols that isolate the threat, minimizing the impact on other systems.
Mitigation and Recovery: Automation tools help in the swift mitigation of threats and assist in recovery processes, ensuring that normal operations resume with minimal downtime.
To learn more about automating security responses, explore our article on automating security questionnaires.
Automation in incident response allows for a more resilient security posture, providing startups with essential capabilities to defend against an ever-evolving threat landscape. Whether it is through password managers, EPPs, or log management software, integrating these tools into your cybersecurity strategy is vital.
For startups looking to automate their incident response, understanding these tools and their benefits is the first step. Incorporate them into your security protocols to enhance your organization's ability to handle security incidents effectively. For additional insights, read our comprehensive guide on guide to automating security questionnaires.
Building a Comprehensive TPRM Framework
In today's interconnected world, managing third-party relationships is crucial for maintaining an organization's security stance. A comprehensive Third-Party Risk Management (TPRM) framework is essential for safeguarding sensitive information and ensuring compliance with security standards.
Third-Party Risk Management Strategies
Third-Party Risk Management involves strategies to identify, assess, and mitigate risks associated with outsourcing to third-party vendors, partners, suppliers, or service providers. Compliance leaders emphasize the importance of robust TPRM strategies (CyberSierra) due to the inherent risks involved.
Key Strategies Include:
Due Diligence: Conduct thorough research and background checks before onboarding any third-party vendor.
Risk Identification: Identify potential vulnerabilities that may arise from third-party associations.
Risk Assessment: Evaluate the severity and likelihood of identified risks.
Risk Monitoring: Implement continuous monitoring mechanisms to detect and address emerging risks.
Risk Mitigation: Develop and apply strategies to manage and reduce identified risks.
Continuous Assessment: Regularly review and update risk management practices to adapt to new threats.
Training: Train staff on best practices for managing third-party risks and using TPRM tools effectively.
By employing these strategies, organizations can mitigate risks such as data breaches, which 62% of the time originate from third-party vendor relationships (CyberSierra).
Components of a TPRM Framework
A strong TPRM framework is composed of several key components that work together to provide a systematic approach to managing third-party risks.
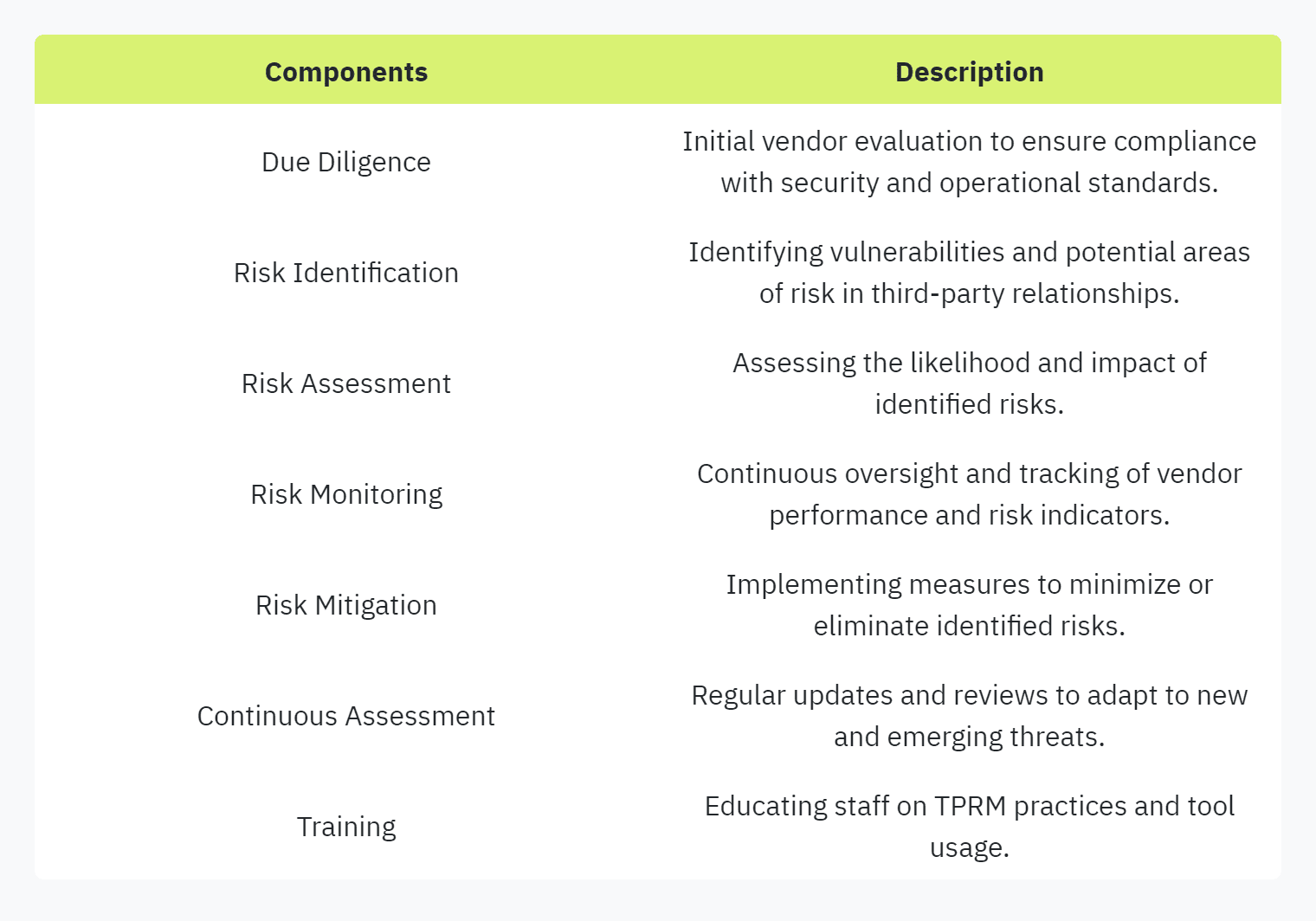
Utilizing these components effectively ensures the mitigation of risks, compliance with regulations, and protection of organizational reputation.
For more information on specific strategies and tools, refer to our articles on automating security questionnaires and best practices for security questionnaires.
Enter your email to start accelerating your sales today.
















