Automating responses to common security questionnaire questions
Share This Article
Importance of Security Questionnaires
Security questionnaires serve as a vital tool for businesses to share and evaluate crucial security information, ensuring the integrity of their digital operations. They play a significant role in cyber risk management, especially as companies expand their digital footprints globally.
Cyber Risk Management Significance
Security questionnaires are fundamental in cyber risk management. As businesses grow their digital presence and interact with third-party vendors, the need to ensure these vendors comply with security standards becomes paramount. By conducting thorough reviews through these questionnaires, companies can safeguard their reputation, assets, and customer trust.
Third-party Vendor Compliance: Ensures that external partners adhere to the company's security protocols and standards.
Reputation Protection: Helps maintain the company's standing by verifying the integrity of all involved parties.
Asset Security: Prevents unauthorized access and potential breaches by vetting the security measures of third parties.
Customer Trust: Builds confidence among customers that their data is protected across all business operations.
These aspects underscore the necessity of integrating security questionnaires into the broader strategy of cybersecurity.
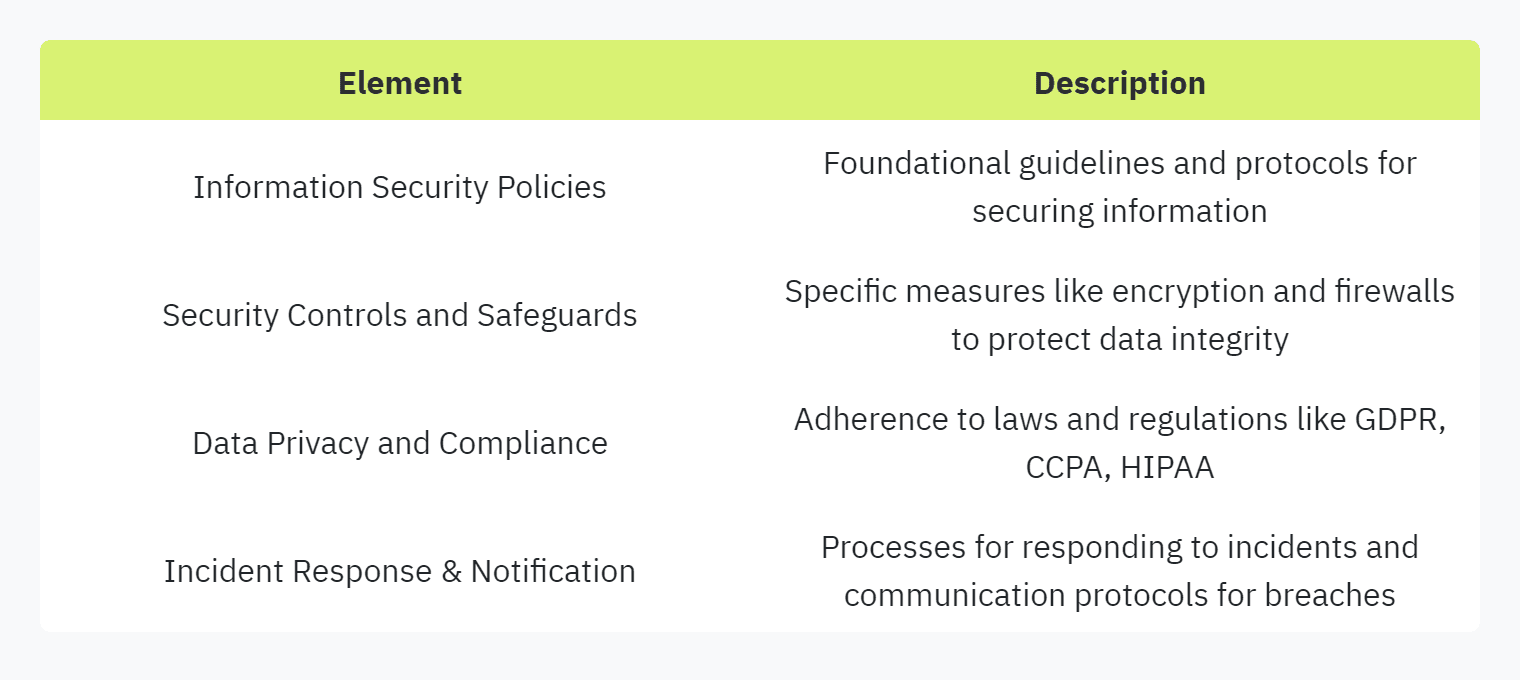
Essential Elements of Questionnaires
For a security questionnaire to be effective, it must cover several key areas that offer a comprehensive view of a vendor's security landscape. The most crucial elements include:
Information Security Policies and Procedures
Establishes the foundational guidelines and protocols for securing information.
Ensures all parties adhere to standardized procedures for data protection.
Security Controls and Safeguards
Details the specific measures in place to protect data integrity and confidentiality.
Includes technical controls such as encryption, firewalls, and access controls.
Data Privacy and Compliance
Ensures adherence to relevant laws and regulations concerning data privacy.
Verifies compliance with standards such as GDPR, CCPA, and HIPAA.
Incident Response and Breach Notification
Outlines the processes for responding to security incidents and data breaches.
Specifies notification protocols to quickly inform affected parties of any breaches.
Here's a quick overview in table format:
By covering these elements, security questionnaires provide a thorough assessment of a vendor's capability to protect sensitive information. For those looking to innovate in this space, automating security questionnaire responses emerges as a beneficial solution.
To delve deeper into managing the complexities and inefficiencies of manual processes, read our related articles on improving and streamlining security questionnaires.
Drawbacks of Manual Questionnaire Handling
In the landscape of security and risk management, manually handling security questionnaires presents significant drawbacks. This section highlights the inefficiencies and risks associated with such traditional approaches.
Inefficiencies of Manual Processes
Manual completion of security questionnaires is notably time-consuming and labor-intensive. This traditional method requires meticulous effort in sifting through extensive documentation and often proves inefficient and inconsistent (Vendict). Professionals are required to manually track responses and update them, leading to delays and potential errors.
The following table illustrates the estimated time and resources required for manual security questionnaire handling:
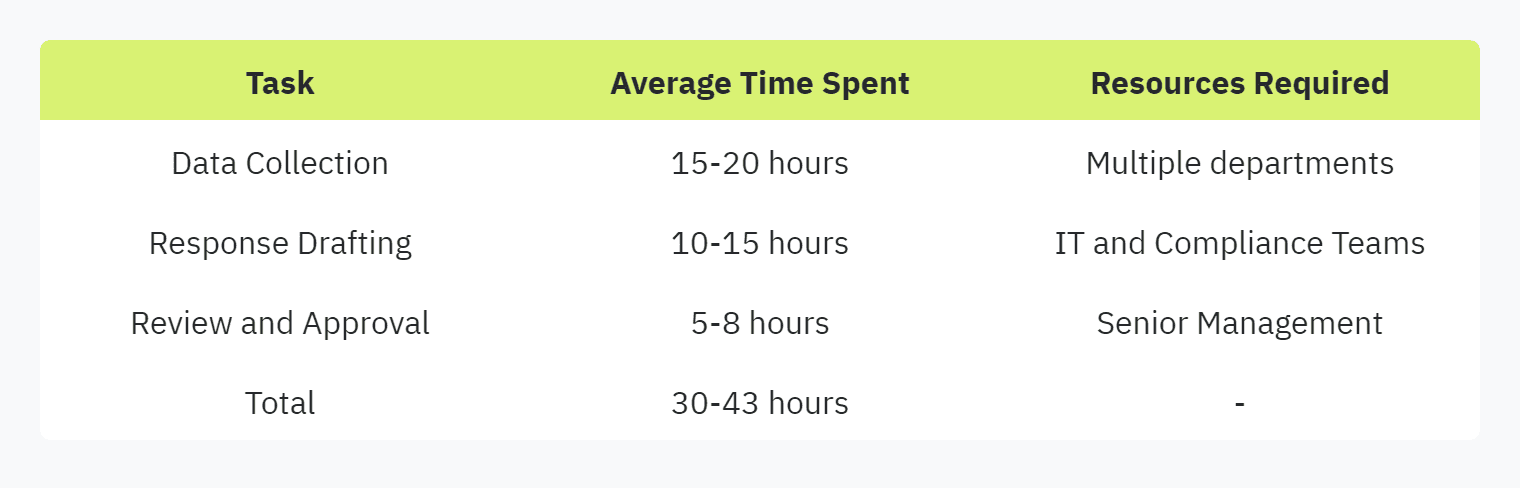
Manual processes are not just time-consuming but also hinder productivity. Such inefficiencies often divert crucial resources away from more strategic activities within the organization.
Risks Associated with Human Error
Human error is another significant risk in the manual handling of security questionnaires. These errors can occur at various stages, including data collection, response drafting, and final approval. As the traditional approach to handling security questionnaires involves multiple steps and personnel, the likelihood of mistakes increases (Vendict).
Errors in security questionnaires can lead to:
Inaccurate Assessments: Incorrect data or omissions can cause errors in the overall risk assessment.
Inconsistent Responses: Different team members may interpret questions differently, leading to inconsistencies.
Delayed Responses: Mistakes may necessitate repeated reviews and revisions, delaying the entire process.
Non-Compliance: Inaccurate or incomplete responses may result in regulatory non-compliance.
Integrating automated solutions can significantly reduce these risks. By leveraging automation tools, organizations can ensure more accurate and consistent information capture, thereby delivering faster and more reliable results (Centraleyes). For more strategies on automation, explore our guide to automating security questionnaires.
In conclusion, the inefficiencies and risks associated with manual handling of security questionnaires underscore the need for automation. Automation not only streamlines the process but also mitigates the risks of human error, enabling security teams to focus on proactive risk management. For further insights, visit our articles on improving security questionnaire experience and tools to simplify security questionnaires.
Benefits of Security Questionnaire Automation
Automating security questionnaire responses offers numerous advantages for organizations, particularly for security and compliance officers, IT managers, and SaaS startups.
Streamlining the Process
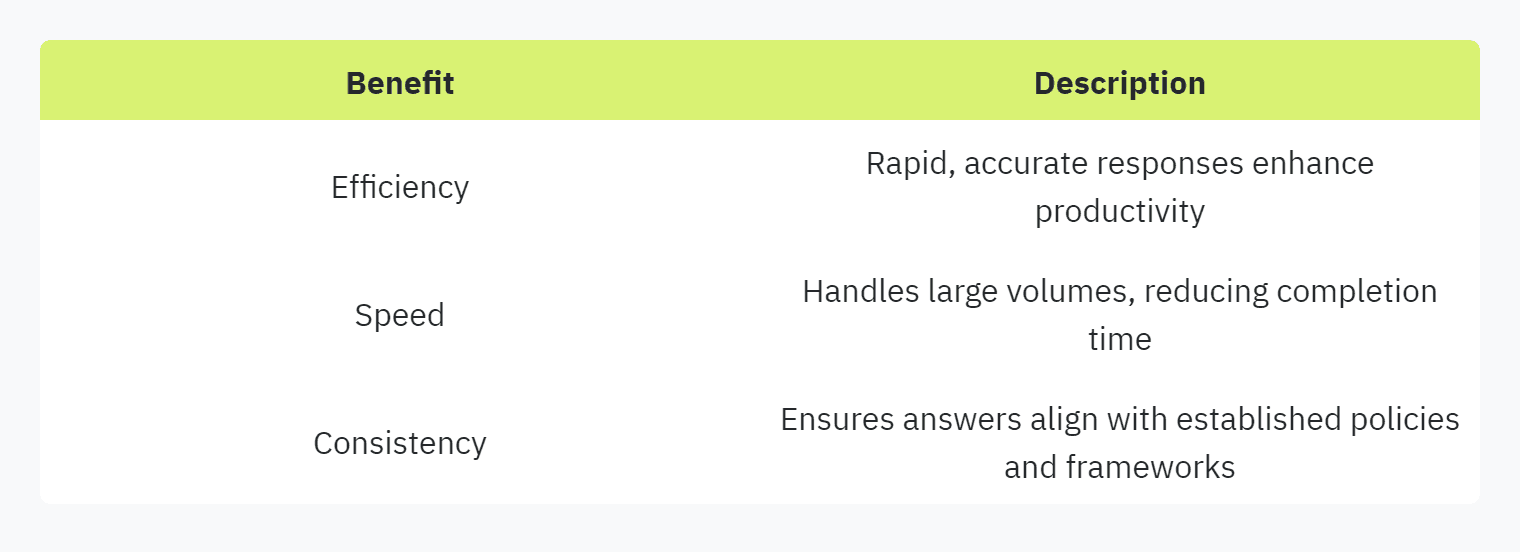
By automating security questionnaire responses, organizations can significantly reduce the time and effort required to complete these essential tasks. Automation tools can quickly analyze, categorize, and respond to common security questions, eliminating the need for manual intervention.
Efficiency: Automation ensures rapid, accurate responses, increasing overall productivity. According to Vendict, automation in security questionnaires helps streamline the process, making it more efficient.
Speed: Automated systems can handle large volumes of questions simultaneously, reducing the time required for response completion. This is crucial for businesses facing multiple security audits or assessments.
Consistency: Automation reduces the risk of inconsistent answers, ensuring that responses align with the organization’s established security policies and frameworks.
For additional details on how to streamline the process, check out our article on streamlining security questionnaires.
Proactive Risk Management
Automation in security questionnaires is not only about efficiency but also serves as a proactive measure in risk management. By implementing an automated system, organizations can better anticipate, identify, and mitigate potential security threats.
Immediate Identification: Automated tools can quickly detect discrepancies or potential red flags in security responses, allowing for immediate action (Vendict).
Enhanced Monitoring: Continuous monitoring capabilities enable organizations to track vendor compliance over time, ensuring ongoing adherence to security standards.
Data-Driven Insights: Automation provides valuable data insights, helping organizations refine their security protocols and improve overall risk management strategies.

For more insights on handling risk management, explore our article on proactive risk management.
Leveraging these benefits can result in a more efficient and proactive approach to security management. For best practices on implementing automation in security questionnaires, visit best practices for security questionnaires and guide to automating security questionnaires.
Automation Solutions and Best Practices
Vendor Solutions like Natural Language Processing (NLP)
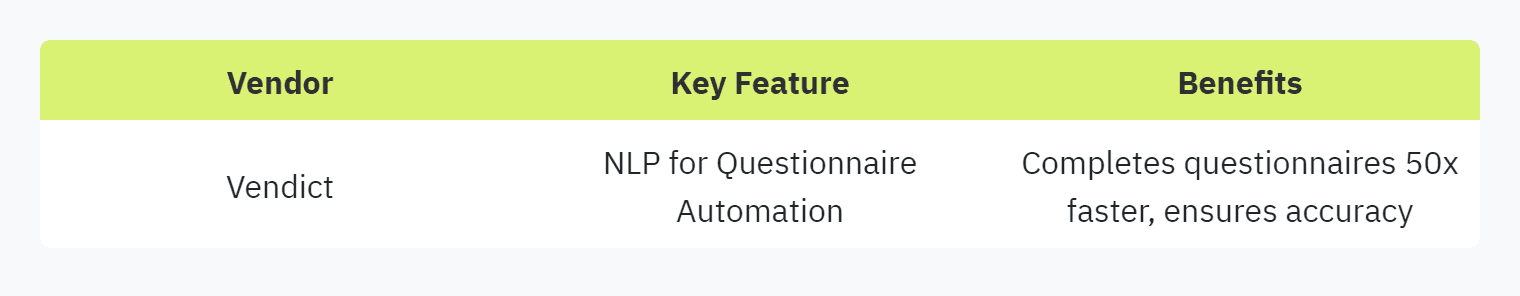
For security and compliance officers, IT managers, and SaaS startups, leveraging vendor solutions like Natural Language Processing (NLP) is a game-changer in automating security questionnaire responses. NLP employs advanced algorithms to understand, interpret, and generate human language, making it possible to streamline the completion of security questionnaires.
Vendict is a notable example of a solution that utilizes NLP for this purpose. Vendict's system can automate the completion of security questionnaires up to 50 times faster than manual methods. This efficiency not only speeds up the process but also ensures that answers are precise and accurate, reducing the risk of human error (Vendict). By automating these tasks, organizations can redirect their focus to core business activities, enhancing overall productivity.
Internal links for further reference:
Future Outlook and Adaptation to Cyber Threats
As cyber threats continue to evolve, the future of security questionnaires is inherently tied to advanced automation technologies. Embracing automation and adhering to best practices will enable organizations to stay ahead in safeguarding their assets, reputation, and customers.
According to Vendict, integrating automated solutions within the cybersecurity framework ensures proactive risk management and continuous adaptation to new threats (Vendict). Automation helps in dynamically updating security protocols and maintaining compliance with minimal manual intervention. This foresight is crucial for mitigating risks in a fast-changing digital landscape.

For more insights into the future outlook and adaptation strategies:
By implementing these automation solutions and adhering to best practices, organizations can significantly enhance their cybersecurity posture and keep pace with the ever-evolving landscape of cyber threats.
Enter your email to start accelerating your sales today.
















