Integrating security questionnaires into your existing systems seamlessly
Share This Article
Importance of Security Questionnaires
Security questionnaires are essential tools used to evaluate and ensure the safety and compliance of vendors and partners. Understanding their significance is crucial for organizations aiming to mitigate cybersecurity risks and maintain robust security standards. Within this section, we will explore the importance of these questionnaires for addressing cybersecurity challenges and assessing vendor risks.
Mitigating Cybersecurity Risks
Organizations today face a myriad of cybersecurity threats that can compromise sensitive data and disrupt operations. Implementing security questionnaires is a proactive step in reducing these risks. They provide a structured way of gathering and evaluating the security measures that vendors and partners have in place.
Common practices to mitigate cybersecurity risks include:
Encrypting sensitive data.
Implementing regular system and software updates.
Conducting employee training on cybersecurity awareness.
Using strong, unique passwords.
Creating and storing data backups.
Regularly assessing and monitoring third-party vendors (UpGuard).
By integrating security questionnaires into their processes, organizations can systematically verify that their vendors are adhering to these cybersecurity best practices, thereby reducing vulnerability to data breaches and other cyber threats.
Vendor Assessment Importance
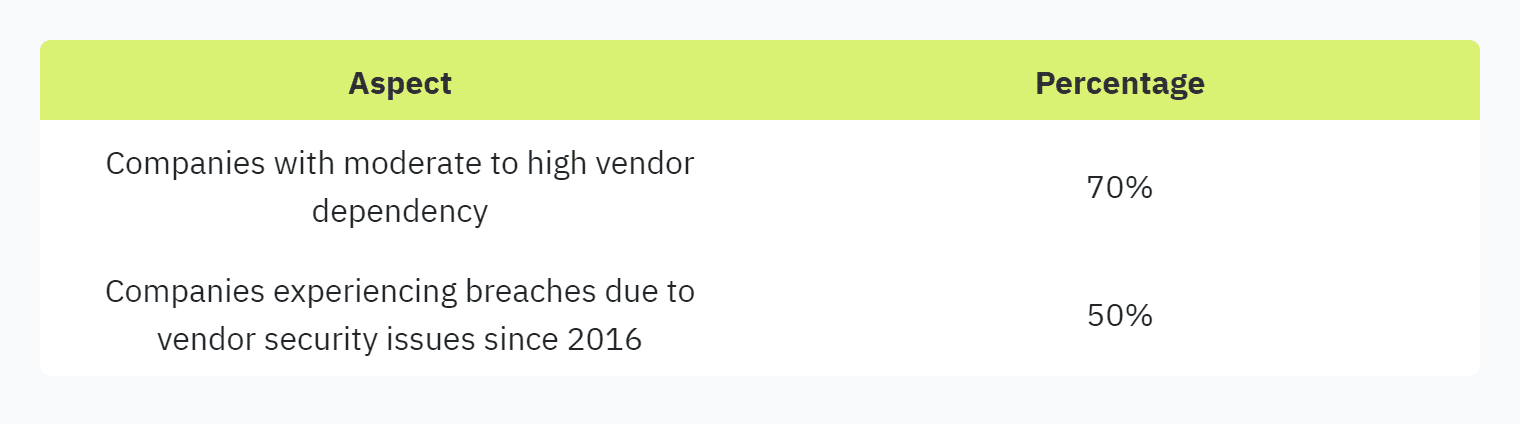
The role of vendors in business operations is significant, with a recent study by Deloitte revealing that 70% of companies rate their dependency on vendors as moderate to high (OneTrust). This dependency underscores the importance of thoroughly assessing vendor security measures.
Security questionnaires help in:
Streamlining data gathering.
Ensuring vendor compliance with regulatory frameworks.
Reducing instances of security breaches due to vendor vulnerabilities.
By utilizing security questionnaires effectively, organizations can identify potential security gaps in their vendor relationships early on, addressing risks before they escalate into significant threats. For more on this, check out our article on understanding security questionnaires.
Internal links to consider for further reading on this topic include why security questionnaires are a nightmare, streamlining security questionnaires, and best practices for security questionnaires.
Key Elements in Security Questionnaires
Understanding the fundamental components of security questionnaires is crucial for efficiently integrating security questionnaires into your systems. Two key elements are custom and framework-based questions, and evidence-based answers.
Custom and Framework-Based Questions
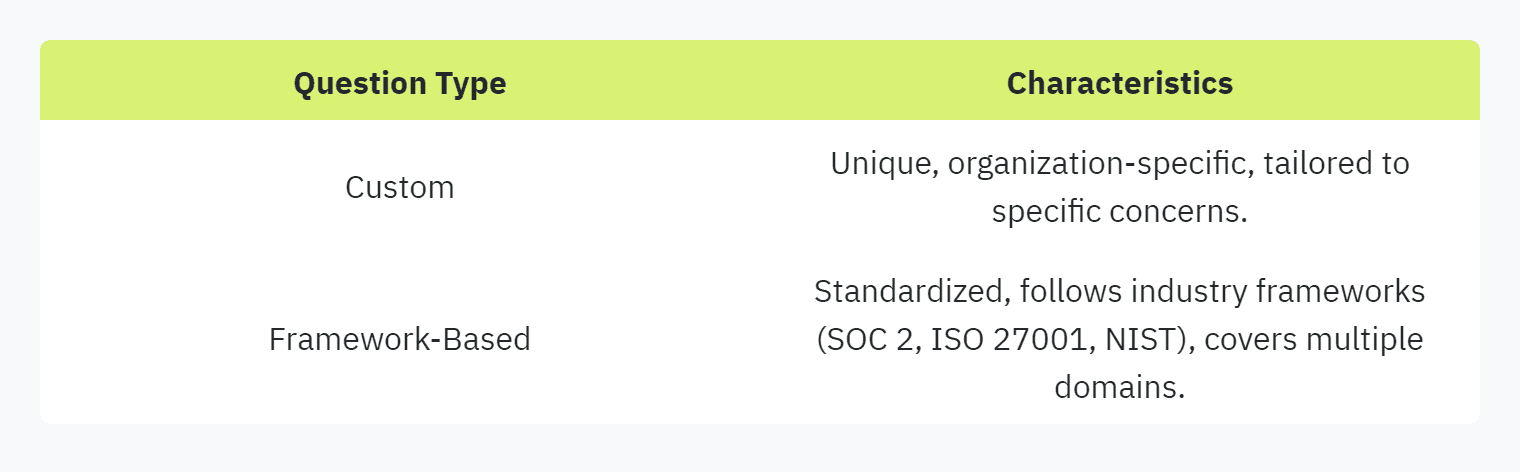
Security questionnaires typically feature both custom questions and framework-based questions. Custom questions are unique to each organization and are designed to address specific concerns or requirements. These questions can cover a wide range of topics, from data privacy practices to employee training protocols.
On the other hand, framework-based questions are standardized and often adhere to well-known frameworks such as SOC 2, ISO 27001, or NIST. These questions provide a structured approach to assessing security measures across multiple domains, ensuring a comprehensive evaluation of an organization's security posture.
Both types of questions are essential for a thorough assessment. For more in-depth information on security questionnaires, businesses should consider customizing their approach to fit their unique requirements while adhering to industry standards.
Evidence-Based Answers
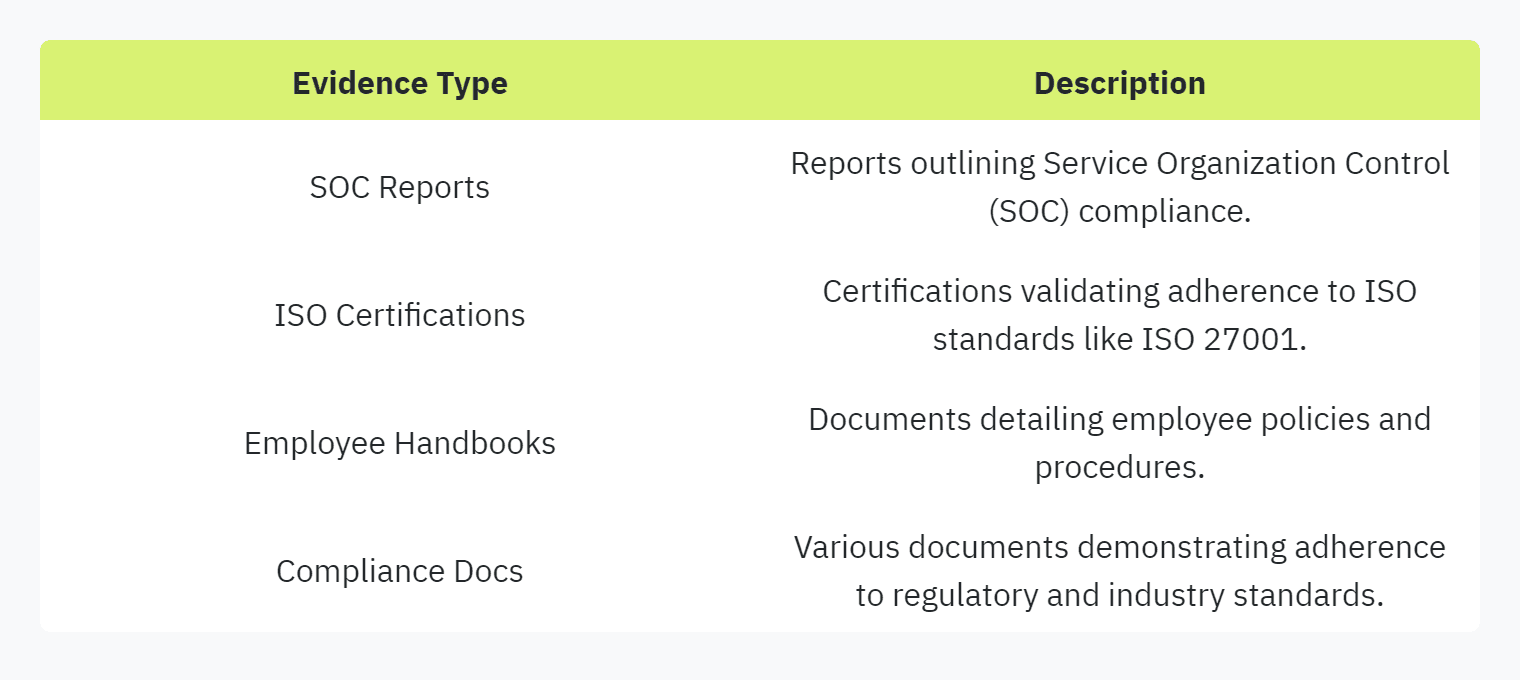
One of the primary expectations when tackling security questionnaires is the need for evidence-based answers (OneTrust). Evidence-based answers involve providing verifiable documentation to support the claims made in response to the questionnaire. This can include a variety of documents such as SOC reports, ISO certifications, employee handbooks, and other relevant compliance documents.
Building an evidence library is essential for managing these responses effectively. An evidence library comprises shareable and reference documents that organizations can use to substantiate their answers.
Maintaining a well-organized evidence library helps streamline the process of responding to security questionnaires, facilitating faster and more accurate answers. It's also beneficial to centralize these operations onto a singular platform accessible to all stakeholders (OneTrust). Doing so not only saves time but also ensures that accurate and up-to-date information is readily available.
For guidance on setting up your answer and evidence libraries, refer to our article on best practices for security questionnaires and tools to simplify security questionnaires. Integrating these elements effectively into your system will lead to improved efficiency and compliance.
Improving Questionnaire Responses
Enhancing the efficiency and accuracy of security questionnaire responses is vital for organizations seeking to seamlessly integrate security protocols. Two strategies to achieve this are establishing an answer library and centralizing operations.
Establishing an Answer Library
Creating an answer library is a fundamental step in improving responses to security questionnaires. An answer library is a repository of pre-approved responses to common questions encountered in security assessments. This library can significantly reduce the time and effort required to complete each questionnaire.
Building the Library: It’s recommended to start by developing a primary answer library and expanding it as necessary. This includes adding responses to custom questions and framework-based inquiries. Keeping answers straightforward and consistent is essential. (OneTrust)
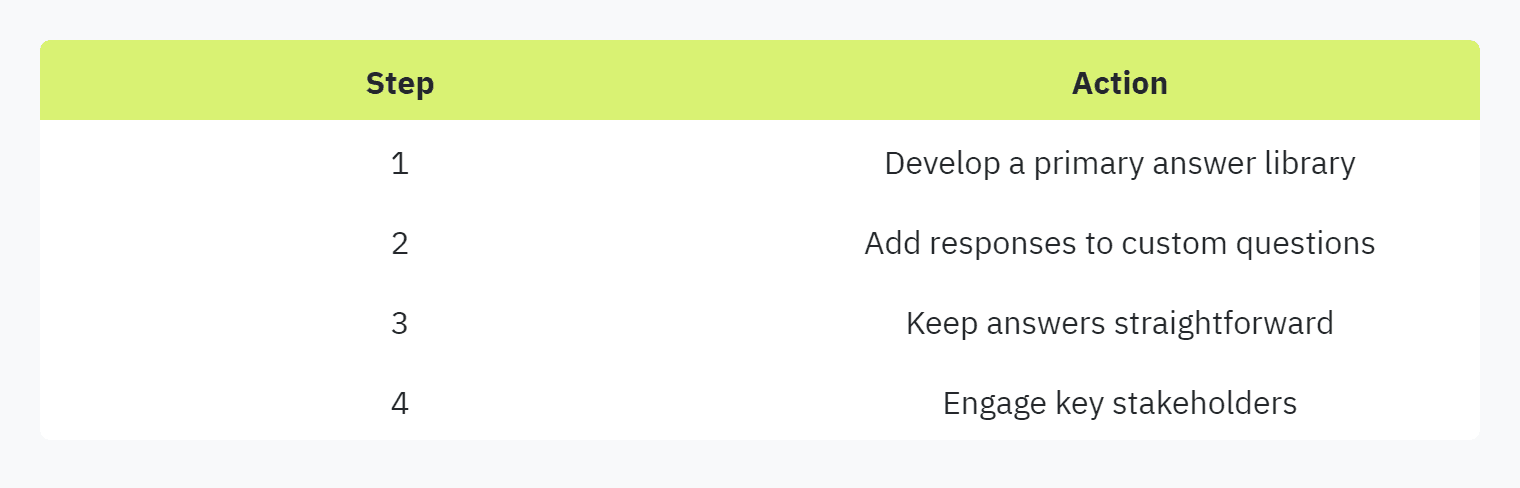
Adding Evidence: Apart from textual answers, it’s crucial to build an evidence library comprising shareable and reference documents. This can include SOC reports, ISO certifications, employee handbooks, and more. Such documentation enhances the credibility of your responses. (OneTrust)
Centralizing Operations
Centralizing operations is another key strategy for improving the response process. By consolidating all functions related to security questionnaires onto a singular platform, organizations can streamline their workflows and enhance collaboration.
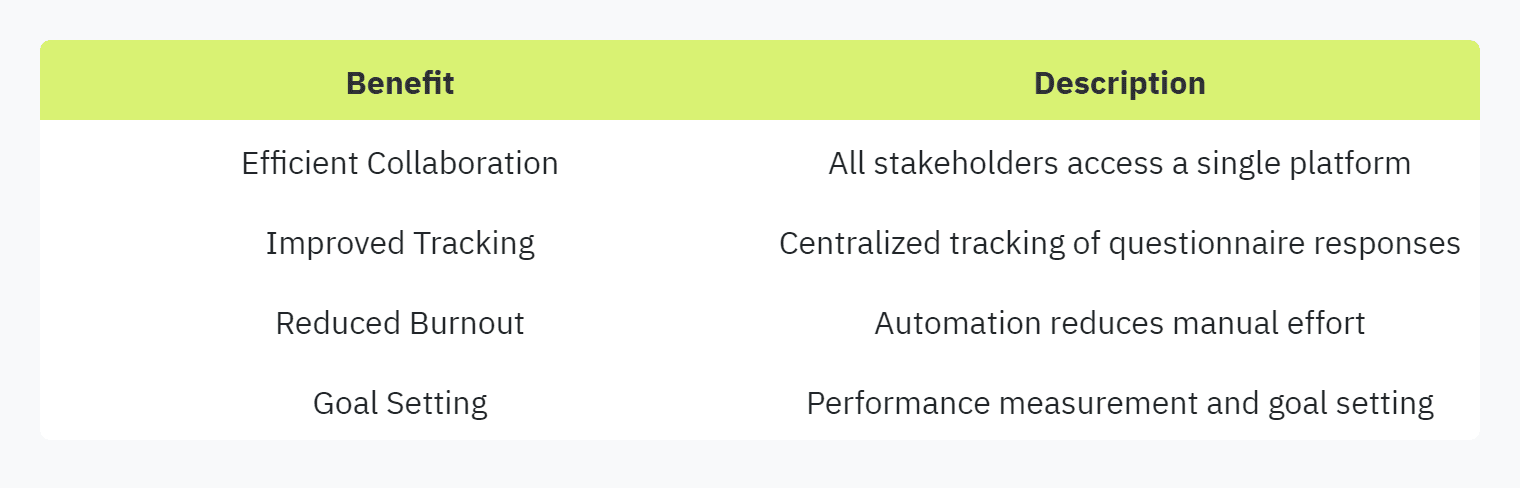
Platform Consolidation: Implementing a singular, accessible platform allows all stakeholders to access the answer and evidence libraries, track responses, and collaborate efficiently. This unified approach ensures that every team member is on the same page and can contribute effectively. (OneTrust)
Performance Measurement: Regularly measuring performance and setting specific goals can help in maintaining the effectiveness of the response process. Leveraging automation tools within the platform minimizes manual effort, reduces burnout, and improves overall response time. More information on automation can be found in our article on automating security questionnaire responses.
By establishing a comprehensive answer library and centralizing operations, organizations can improve their efficiency in handling security questionnaires. For more insights, explore our articles on streamlining security questionnaires and best practices for security questionnaires.
Automation for Efficient Responses
Leveraging Technology
Automation of security questionnaire responses is crucial for creating an efficient workflow, ultimately saving time and money for organizations. Leveraging advanced technologies such as Natural Language Processing (NLP), Machine Learning (ML), and AI can significantly streamline the completion of security questionnaires. These technologies can help in automatically answering custom questionnaires and evaluating an organization's security, privacy, and compliance programs.
For example, OneTrust's Questionnaire Response Automation tool helps organizations by pre-populating answers to common questions, reducing the time spent on repetitive tasks. Additionally, this technology ensures accuracy in responses by utilizing a vast database of previously vetted answers, ensuring that answers are both consistent and compliant.
Streamlining Workflow Operations
To further improve efficiency, building an answer library is essential. This library should contain a collection of "go-to" answers that can be reused, minimizing the time required to respond to new questionnaires. Such a library can be developed organically or through industry-standard questionnaires like the Shared Assessments SIG Lite or SIG Core (OneTrust).

Another aspect of streamlining operations involves centralizing the management of questionnaire responses. An evidence library comprising shareable and reference documents such as SOC reports, ISO certifications, and employee handbooks can significantly enhance the workflow. This central repository ensures that all necessary documents are easily accessible, reducing delays and simplifying the response process.
The surge in reliance on remote work technology due to the COVID-19 pandemic has exposed vulnerabilities and led to a 62% increase in large-scale cyberattacks. This makes it even more critical for organizations to adopt automation tools that can handle the increased volume of security questionnaires efficiently.
For more detailed insights on improving the efficiency of your security questionnaire responses, visit our article on tools to simplify security questionnaires.
By leveraging technology and streamlining workflow operations, organizations can efficiently manage and respond to security questionnaires. Implementing automation not only enhances accuracy and compliance but also frees up valuable time and resources. Explore our guide to automating security questionnaires for additional strategies and best practices.
Enter your email to start accelerating your sales today.
















