Effective communication to make security questionnaires less confusing
Share This Article
Importance of Security Questionnaires
Role in Cyber Risk Management
Security questionnaires play a vital role in cyber risk management. As businesses expand their digital presence and extend operations across borders, these questionnaires serve as essential tools to ensure third-party vendors meet necessary security standards. They provide a structured method for businesses to share and evaluate vital security information.
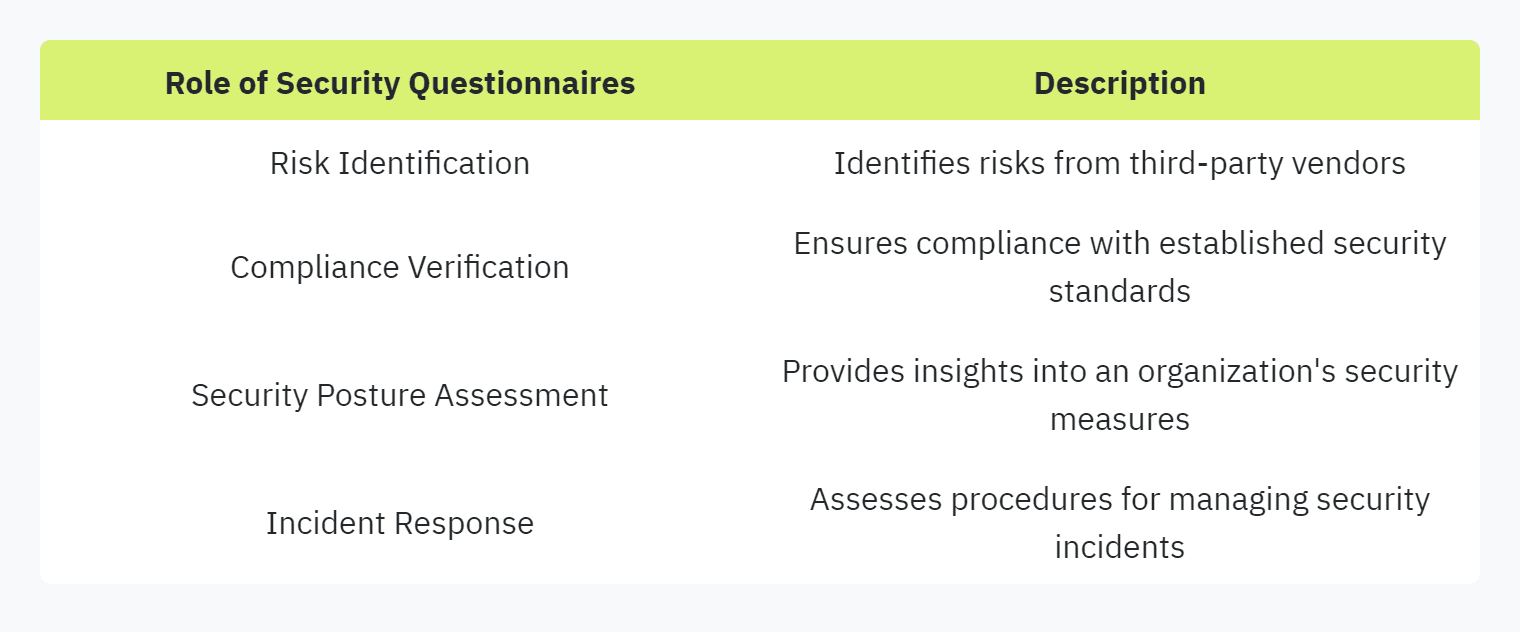
Security questionnaires have emerged as indispensable in vendor risk management. They help organizations identify potential security challenges arising from vendor relationships and ensure vendors comply with security requirements (SecureSlate).
Components Evaluated in Questionnaires
Several critical components are evaluated in security questionnaires to assess an organization's security posture comprehensively. These elements provide a detailed overview of an organization's security measures and compliance practices.
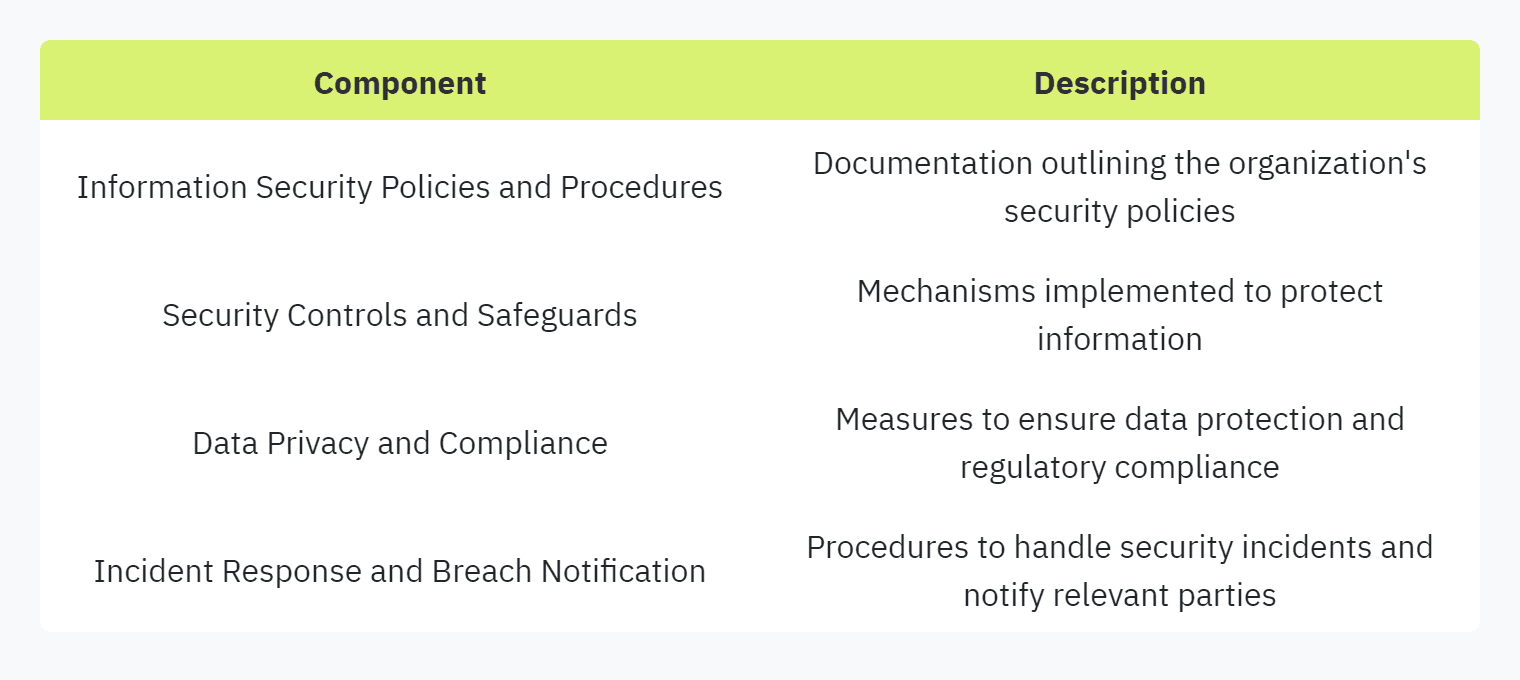
Key sections of security assessment questionnaires cover organizational security policies, technical security controls, incident response and management, and compliance with security frameworks such as NIST and ISO 27001 (SecureSlate).
Internal links like compliance in security questionnaires and integrating security questionnaires can provide additional insights into these components and their significance.
By comprehensively evaluating these components, security questionnaires help businesses understand their security landscape better and take necessary actions to mitigate cyber risks.
Automation in Security Questionnaires
Streamlining Questionnaire Completion
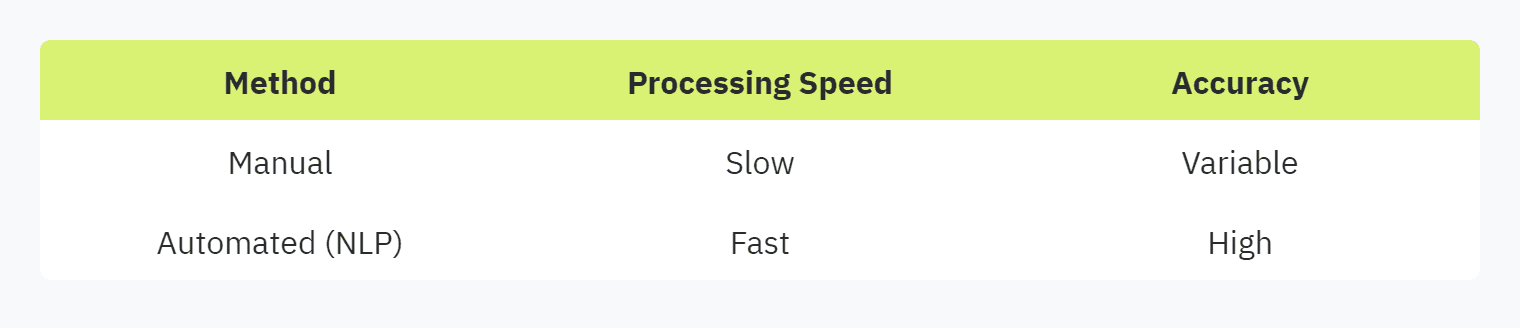
Security questionnaires typically contain hundreds of questions, making manual completion time-consuming and prone to errors. Automation can dramatically enhance this process, making it more efficient and accurate. Vendict's tool leverages Natural Language Processing (NLP) to streamline the completion of security questionnaires, processing them 50 times faster than manual methods.
To learn more about the benefits of automating security questionnaires, visit our automating security questionnaires page.
Benefits of Automated Processes
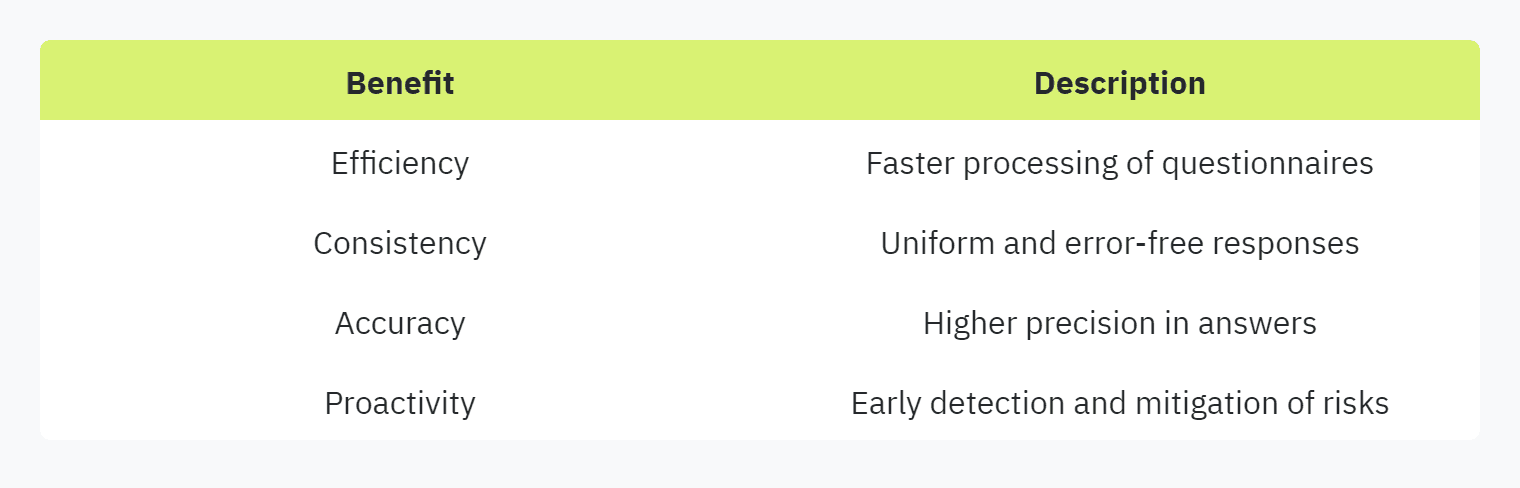
The automation of security questionnaires offers numerous benefits, acting as a protective barrier against potential risks and enhancing organizations' proactive risk management efforts. Some key advantages include:
Efficiency: Automated tools can handle large volumes of questions swiftly, freeing up time and resources for other critical tasks.
Consistency: Automation ensures consistent and precise answers, reducing the risk of human error.
Accuracy: By leveraging technologies like NLP, automated systems provide accurate and reliable responses, meeting compliance and industry standards.
Proactivity: Automated processes help organizations stay ahead of potential risks, addressing vulnerabilities before they become problematic.
For further insights, read our guide on the benefits of automated processes.
By adopting these automated solutions, security and compliance officers, IT managers, and SaaS startups can significantly enhance their approach to managing and completing security questionnaires. Visit our articles on common frustrations with security questionnaires and tools to simplify security questionnaires for more information.
Best Practices for Security Questionnaires
Comprehensive Answering Strategies
When dealing with security questionnaires, it’s crucial to adopt a comprehensive answering strategy. Providing thorough and accurate answers not only demonstrates your organization’s commitment to security but also builds trust with stakeholders. Below are some best practices:
Centralize Information: Gather information from various departments to ensure all aspects of the organization’s security posture are covered. This includes Information Security Policies, Security Controls, Data Privacy, and Incident Response protocols.
Clarify Technical Terms: Simplify complex technical jargon to make the responses more understandable. This can help avoid misunderstandings and ensure your answers are clear and concise.
Include Evidence: Support your responses with relevant documentation and evidence. This can include policy documents, compliance certificates, and incident response records (SecureSlate).
Conduct Regular Reviews: Regularly review and update the documentation to ensure your answers reflect the current state of your organization’s security measures. This is crucial for maintaining accuracy and relevance.
Allocate Resources: Ensure that there are dedicated resources to focus on completing security questionnaires. This helps in addressing competing priorities and resource constraints.
Alignment with Security Frameworks
Aligning your responses with established security frameworks is another essential practice. This not only standardizes your responses but also assures stakeholders of your compliance with industry standards. Here’s how to effectively align your security questionnaire responses:
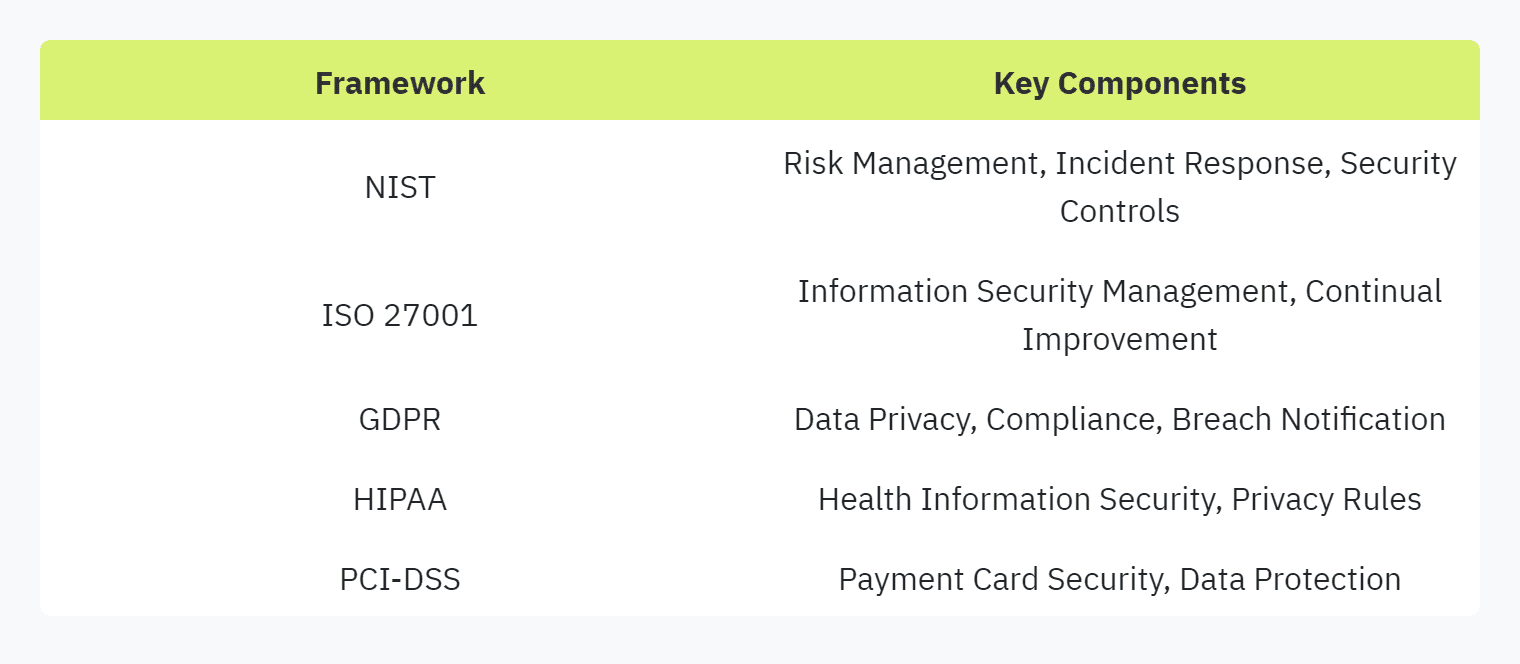
Identify Relevant Frameworks: Determine which security frameworks apply to your organization. Common frameworks include NIST, ISO 27001, GDPR, HIPAA, and PCI-DSS (SecureSlate).
Map Responses to Frameworks: Coordinate your responses with the requirements set forth by the relevant frameworks. This ensures consistency and demonstrates compliance.
Highlight Compliance: Clearly illustrate how your organization meets various security controls and safeguards outlined in the frameworks. Use specific examples and documentation to substantiate your claims.
Use Automated Tools: Consider automating security questionnaires to streamline the alignment process. Automated tools can help map your organization’s security measures to various frameworks efficiently.
Regular Audits: Conduct regular internal audits to ensure ongoing compliance with the selected frameworks. This practice helps in identifying gaps and making necessary improvements.
For more detailed guidance, explore our best practices for security questionnaires and learn how to streamline your responses through automation and alignment with industry standards.
By following these comprehensive answering strategies and aligning with security frameworks, organizations can effectively navigate the complexities of security questionnaires, thereby enhancing their cybersecurity posture and fostering trust with stakeholders. For further insights, refer to our articles on tracking security questionnaire responses and streamlining security questionnaires.
Future Trends in Security Questionnaires
AI and Machine Learning Integration
Emerging technologies such as artificial intelligence (AI) and machine learning (ML) are revolutionizing the way organizations manage security questionnaires. AI and ML can analyze vast amounts of data to detect patterns and anomalies, assisting in identifying potential security risks and vulnerabilities in questionnaire responses. This capability allows for more accurate assessments and proactive risk management.
By leveraging AI and ML, security questionnaires can become dynamic, updating in real-time based on the latest threat intelligence. This ensures that organizations stay ahead of emerging threats and continuously improve their security posture. Automation of security assessments through AI reduces manual efforts, leading to consistent and accurate evaluations.

For more insights on using AI in security questionnaires, refer to our article on ai in security questionnaires.
Impact of Cloud Computing and IoT
The proliferation of cloud computing and the Internet of Things (IoT) brings new challenges and opportunities for security questionnaires. As organizations migrate to cloud environments and adopt IoT devices, security questionnaires must adapt to evaluate the impact of these technologies on their security posture (Trust Cloud Community).
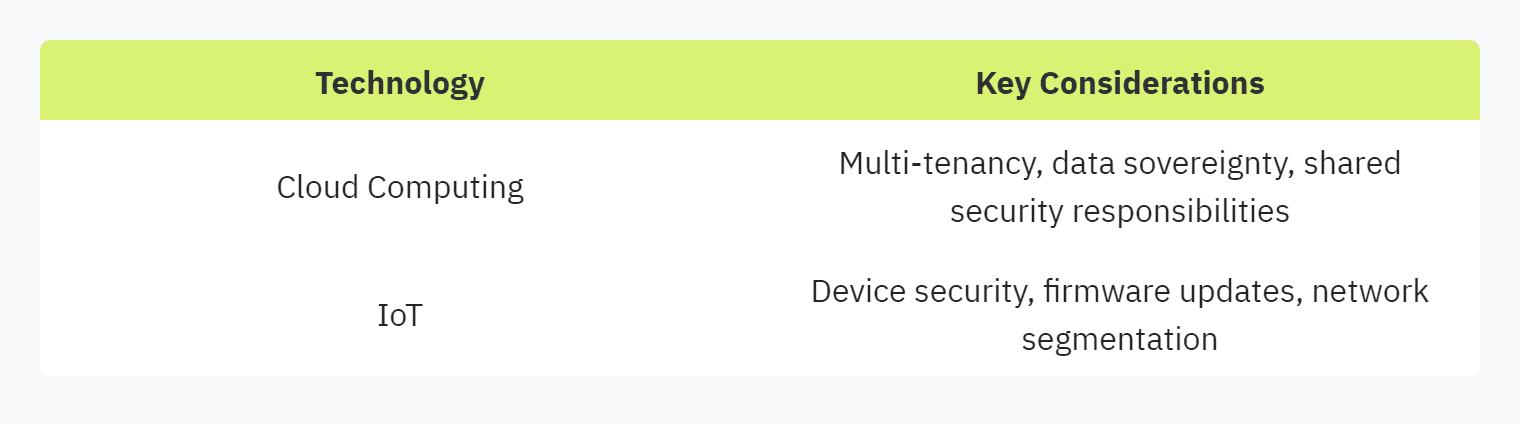
Cloud computing introduces complexities such as multi-tenancy, data sovereignty, and shared security responsibilities. Security questionnaires need to address these aspects to ensure comprehensive risk assessments. Evaluating cloud service providers' security measures, compliance with relevant standards, and data protection mechanisms becomes critical.
Similarly, the integration of IoT devices into corporate networks expands the attack surface, creating additional security risks. Questionnaires should include assessments of IoT device security, firmware updates, and network segmentation to mitigate potential threats.
To dive deeper into the impacts of cloud computing and IoT, read more about data insights in security questionnaires and compliance in security questionnaires.
By staying informed about these future trends, security and compliance officers, IT managers, and SaaS startups can better prepare for and mitigate risks in their security assessments. Embracing AI, ML, and understanding the implications of cloud and IoT will be essential components of their strategy for effective risk management. For more best practices, visit our guide on best practices for security questionnaires and improving security questionnaire experience.
Enter your email to start accelerating your sales today.
















