Improving team collaboration when tackling security questionnaires
Share This Article

Understanding Security Questionnaires
Security questionnaires are a cornerstone in maintaining robust security practices, especially when onboarding new vendors or evaluating existing partnerships. They serve not only to assess the security posture of third-party vendors but also to demonstrate compliance with industry standards and regulations.
Importance of Security Questionnaires
Security questionnaires play a vital role in safeguarding organizational data against cyber threats and vulnerabilities. By serving as a bridge of trust between an organization and its vendors, these questionnaires ensure adherence to security standards, protect sensitive information, and mitigate legal and financial risks. They help organizations evaluate if potential vendors comply with cybersecurity frameworks, manage risk proactively, and implement appropriate data protection measures.
Advantages include:
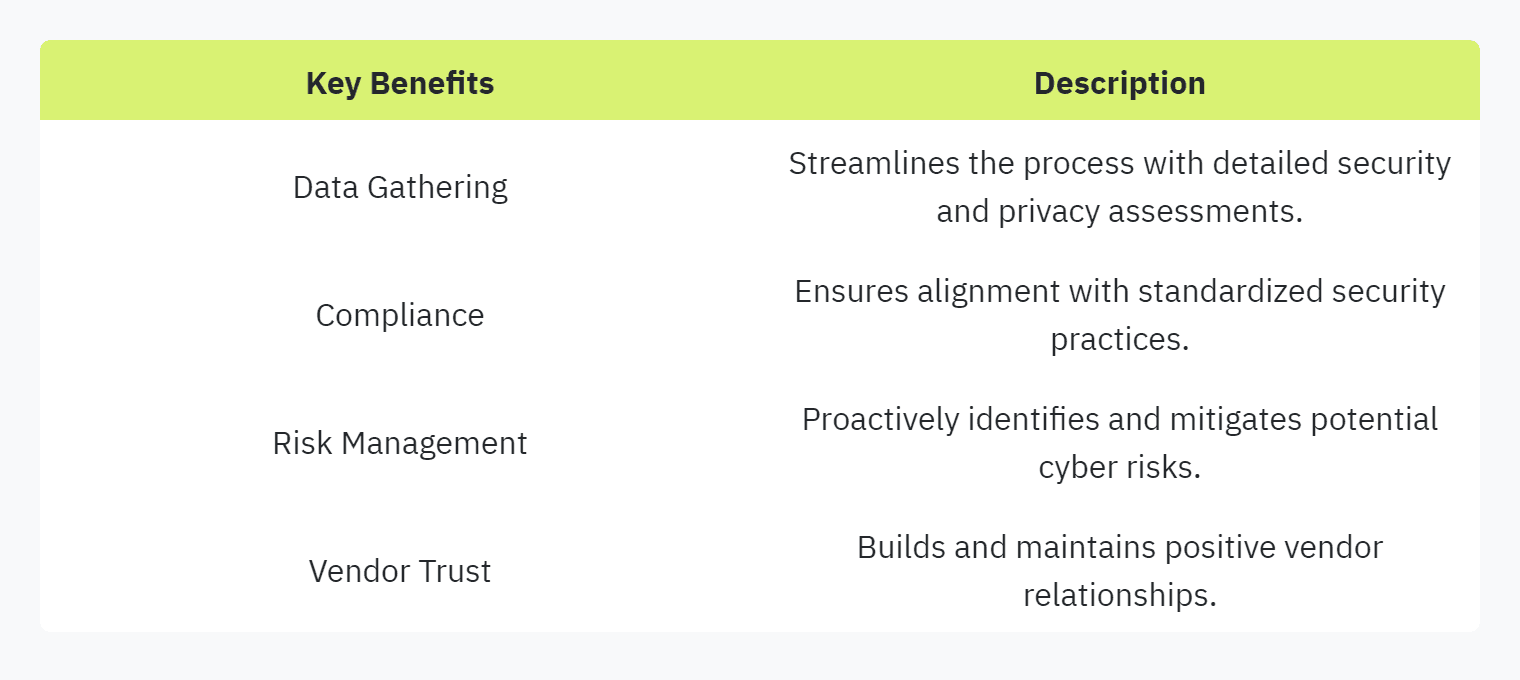
Risk Management: Proactively addresses potential security weaknesses, reducing the risk of data breaches and other cyber threats.
Compliance: Ensures vendors adhere to regulatory requirements, making it easier for organizations to maintain their own compliance.
Cost Savings: Early identification of security vulnerabilities can prevent costly disruptions, legal issues, and reputational damage in the long run.
For more details on the importance and challenges of these questionnaires, visit our article on why security questionnaires are a nightmare.
Key Topics Covered
Security questionnaires encompass a wide array of topics that collectively provide a comprehensive evaluation of a vendor's security measures. These topics typically include:
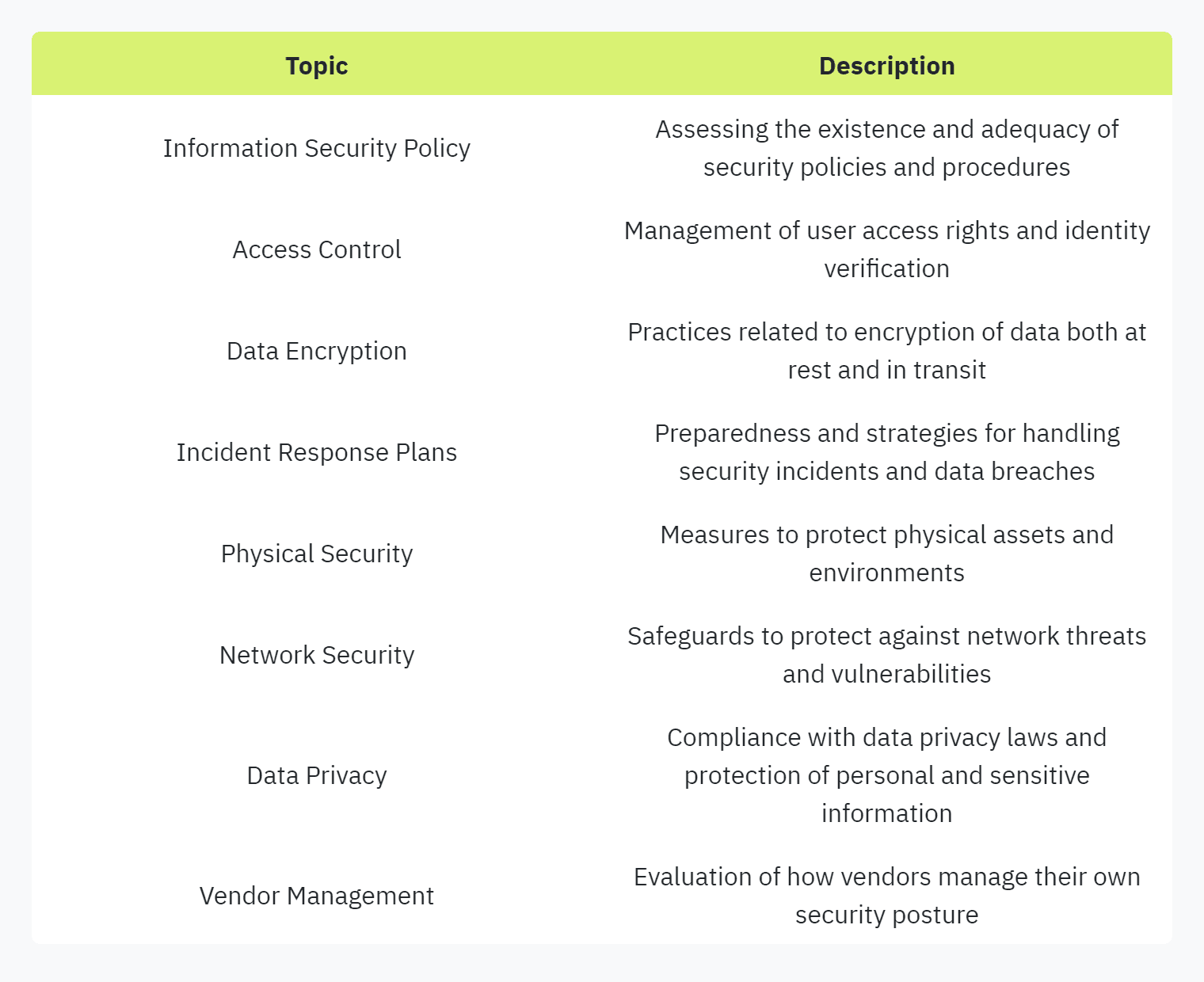
For a more in-depth understanding of the components and their implications, please refer to our section on common frustrations with security questionnaires.
Security questionnaires provide a structured approach to evaluating the cybersecurity measures of vendors, helping organizations build trust and ensure their data remains secure. For comprehensive strategies on automating and streamlining this process, readers might find our guide to automating security questionnaires useful.
Benefits of Security Questionnaire Automation
Automating the security questionnaire process offers several significant advantages for organizations, especially for security and compliance officers, IT managers, and SaaS startups. This section explores how automation enhances efficiency and mitigates risks.
Enhancing Efficiency
Automating security questionnaires can significantly improve efficiency by streamlining the entire process. AI-powered tools can generate responses, suggest answers based on past responses, and pre-fill questionnaires with relevant information (Arphie). As a result, the time and effort required to complete each questionnaire is greatly reduced.
Benefits of automation include:
Faster Response Times: Automation tools can quickly pull relevant data and generate responses, reducing the time taken to complete questionnaires.
Accuracy and Consistency: Automated systems ensure that the information provided is accurate and consistent across multiple questionnaires.
Reduces Manual Work: Automation minimizes the manual effort involved in filling out repetitive and complex security questionnaires.
A clear comparison of the efficiency gains from automating security questionnaires is shown below:
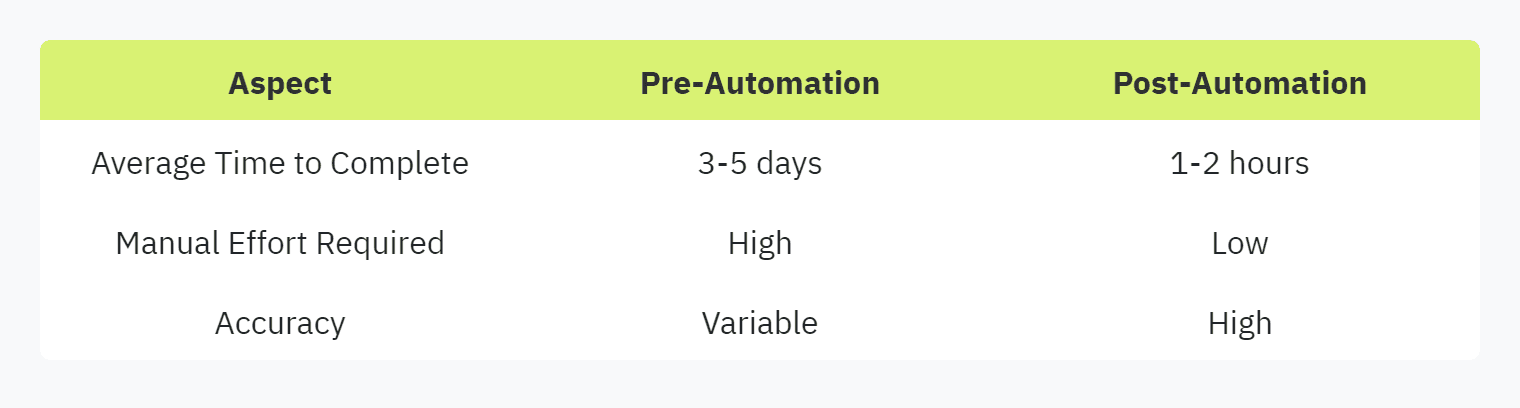
For more details on increasing efficiency in security questionnaires, visit our page on efficient security questionnaires.
Mitigating Risks
Automated security questionnaires offer substantial risk mitigation benefits. By using AI-powered solutions, organizations can address security vulnerabilities and prevent costly disruptions later on (Scytale).
Risk mitigation benefits include:
Early Identification of Vulnerabilities: Automated tools can identify and flag potential security issues early, allowing for proactive remediation.
Consistent Compliance Adherence: Automation ensures that questionnaires are completed in alignment with security and compliance standards, reducing the risk of non-compliance.
Quality Control: Built-in checks and balances within automation tools help maintain a high level of quality and accuracy, reducing the risk of errors.
A summary of risk reduction through automation:
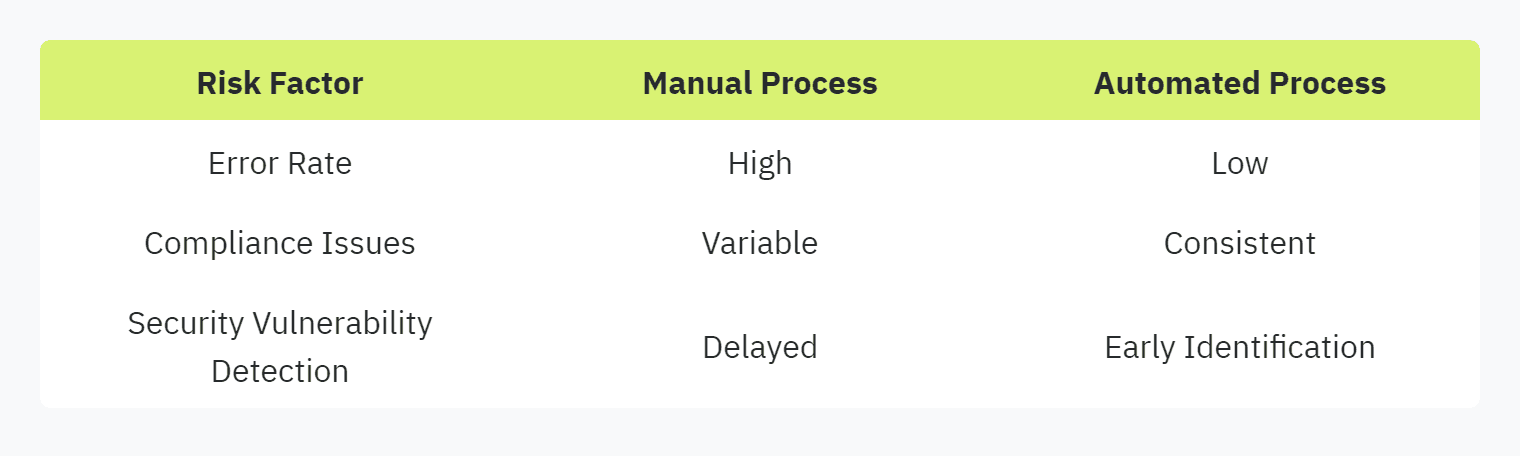
For insight into the potential risks and how to handle them effectively, see our guide on compliance in security questionnaires.
Implementing security questionnaire automation can lead to numerous benefits, from enhancing efficiency to mitigating risks. These improvements can support better collaboration in security questionnaires and ultimately protect organizational credibility and sensitive information. Explore more about automating these processes in our article on automating security questionnaires.
Best Practices for Security Questionnaires
Adopting best practices for security questionnaires can significantly enhance the efficiency and effectiveness of the process, building trust and transparency between parties. The following sections outline strategies such as building trust profiles and staying current with trends in security questionnaires.
Building Trust Profiles
Building trust profiles can reduce the need for completing extensive questionnaires, easing the assessment process and establishing credibility upfront. This proactive approach demonstrates a commitment to strong security, privacy, and compliance measures.
Key elements of a trust profile may include:
Security and privacy policy
Internal policies
Recent audit reports
Compliance certifications
By proactively demonstrating a robust security, privacy, and compliance program, organizations can alleviate customer concerns and foster transparency. Trust profiles help set a foundation for long-term trust in vendor relationships, reducing the need for repetitive information gathering. According to OneTrust, building a trust package is a strategic approach, showcasing the organization's commitment to security.
Trends in Security Questionnaires
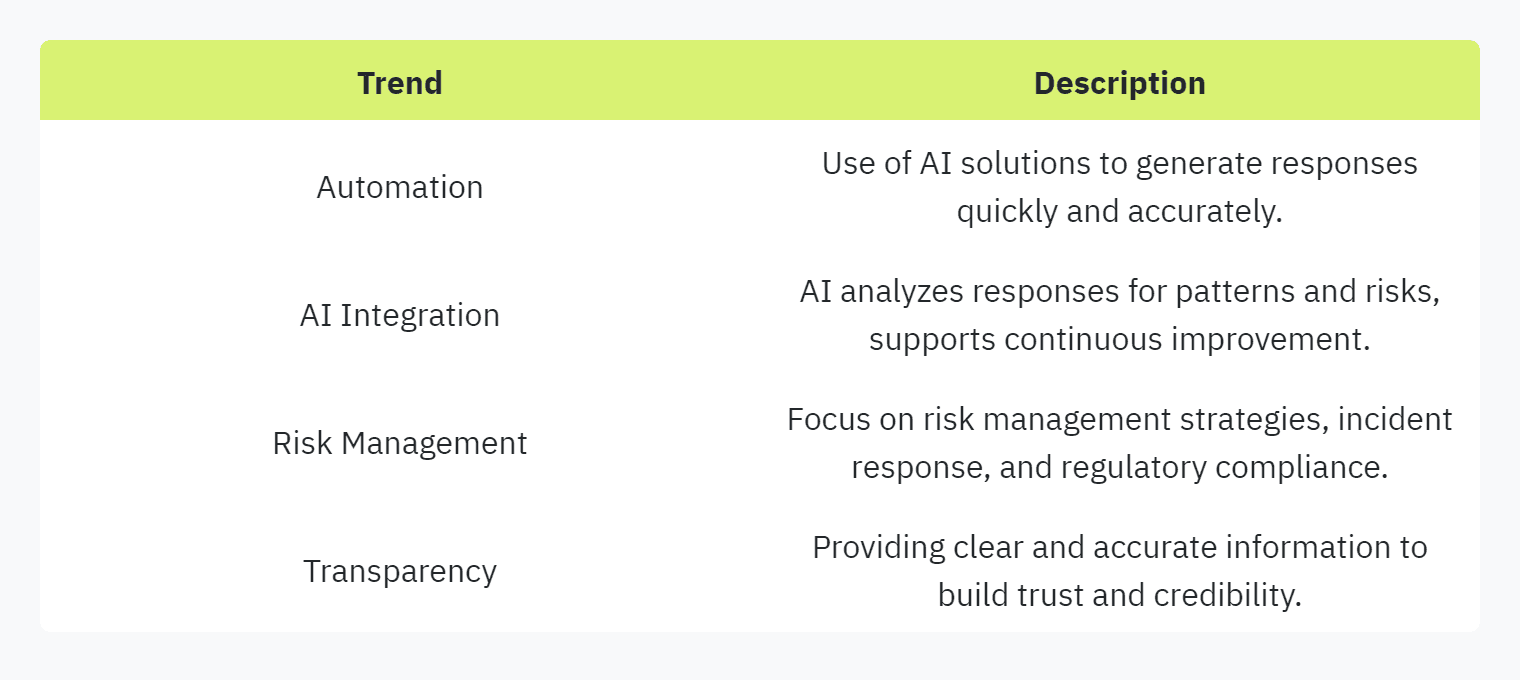
Keeping up with the trends in security questionnaires ensures that your organization remains competitive and compliant. Current trends include:
Automation: Leveraging AI solutions to automate the completion of security questionnaires enhances efficiency and accuracy. Automation tools help to quickly generate responses based on predefined data sets, reducing the manual effort involved. For more information on automation, visit our page on automating security questionnaires.
AI Integration: AI in security questionnaires can analyze responses to identify patterns and risks, providing insights for continuous improvement. This technology also helps to better manage large volumes of questionnaires by streamlining the process. Explore more about AI and automation on our AI in security questionnaires page.
Risk Management: Organizations are adopting more sophisticated risk management strategies. Security questionnaires facilitate discussions on risk management plans, incident response protocols, and regulatory compliance, enhancing due diligence (Scytale).
Transparency: Ensuring transparency in responses fosters a secure business environment. Providing clear and accurate information in security questionnaires builds trust and credibility between parties, setting a firm foundation for vendor relationships (Responsive).
Here is a table summarizing key trends in security questionnaires:
Applying these trends and best practices for security questionnaires will help your organization streamline processes, reduce administrative burdens, and foster stronger, trust-based relationships with vendors and partners. For additional tips and guidelines, explore our best practices for security questionnaires.
Streamlining Vendor Relationships
Managing vendor relationships efficiently is crucial for organizations aiming to ensure compliance and robust security in their operations. This section explores the impact of security questionnaires on vendor relationships and how leveraging AI solutions can enhance collaboration in security questionnaires.
Impact of Security Questionnaires
Security questionnaires are essential tools for assessing the security and privacy measures of potential vendors. They streamline the process of data gathering and ensure that vendors align with industry-relevant regulatory frameworks (OneTrust). These questionnaires help organizations evaluate if potential vendors comply with cybersecurity frameworks, proactively manage cyber risks, and implement appropriate data protection measures.
By accurately and promptly completing security questionnaires, organizations can establish a positive and enduring vendor relationship. Ensuring compliance with standardized security measures, such as the ISO 27001 self-assessment questionnaire or the Common Security Questionnaire used by the Cloud Security Alliance, builds trust and reliability (Vendict). For more insights on maintaining compliance, refer to our guide on compliance in security questionnaires.
Leveraging AI Solutions
Incorporating AI-powered solutions in the completion of security questionnaires significantly transforms and enhances the process. AI automation addresses the increasing complexity and volume of security questionnaires, making it easier to manage and complete them efficiently. Here are a few benefits of leveraging AI solutions:
Efficiency: AI streamlines the questionnaire process, providing faster and more accurate responses. This efficiency helps organizations handle the growing volume of questionnaires effectively (Trustcloud).
Real-Time Collaboration: AI-powered platforms offer live and self-sustaining security portals that showcase an organization's security status. This feature enables real-time collaboration among team members, enhancing the overall efficiency of handling security questionnaires.
Automation: Automated responses through AI reduce the time and effort needed to complete security questionnaires. Automation ensures consistency and accuracy in the responses provided.
Simplified Workflow: AI solutions simplify the collaboration in security questionnaires, aiding in better communication and coordination between teams. For more on improving the workflow, refer to our section on automating security questionnaire responses.
Exploring the potential of AI in security questionnaires can significantly improve the overall process. For further reading on this topic, check out our article on AI and automation in security questionnaires.
By leveraging AI solutions, organizations can enhance the efficiency and accuracy of their security questionnaire process, strengthen vendor relationships, and better manage compliance and security standards. For more strategies, visit our page on streamlining security questionnaires.
Enter your email to start accelerating your sales today.
















