Tracking and analyzing responses to make security questionnaires easier
Share This Article

Understanding Security Questionnaires
To ensure robust cybersecurity, organizations use security questionnaires as a key aspect of their vendor risk assessment processes. This section will delve into the purpose of these questionnaires and their importance in evaluating vendor risk.
Purpose of Security Questionnaires
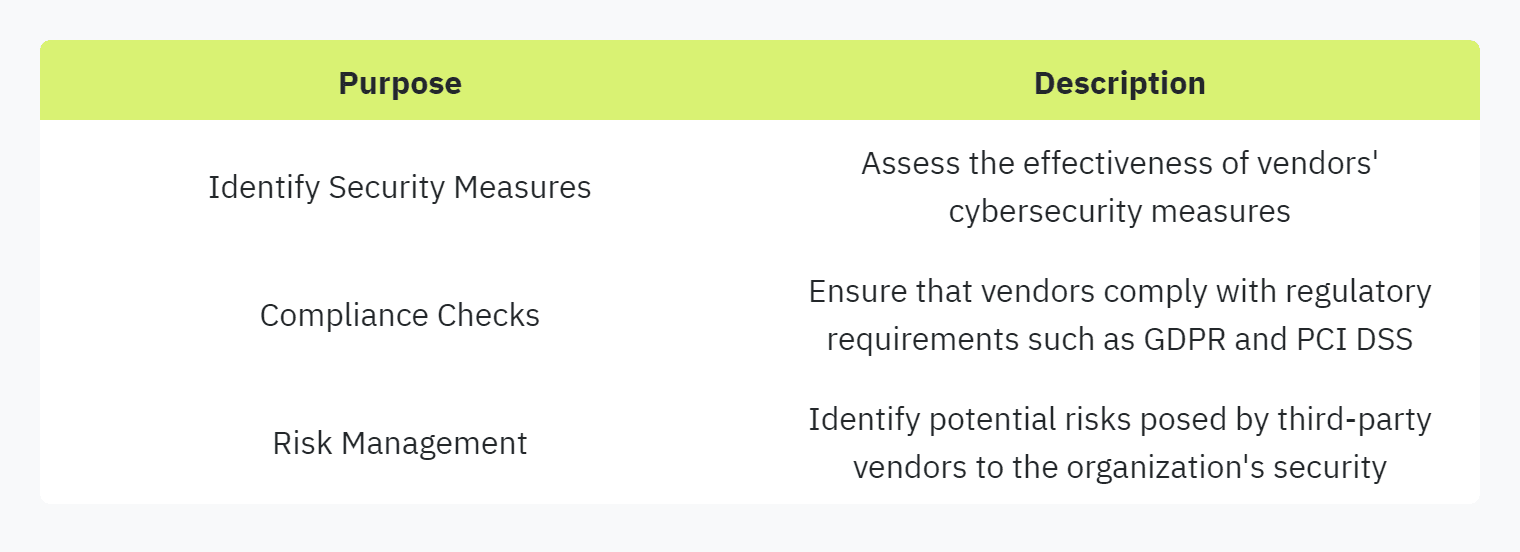
Security questionnaires are instrumental in gathering detailed insights into the security posture of third-party vendors (UpGuard). These questionnaires are essential tools for understanding various security aspects, such as information security policies, data protection measures, and compliance with industry standards.
Importance of Vendor Risk Assessment
Vendor risk assessment is a critical component of the due diligence process. Organizations send security questionnaires to vet third parties before onboarding and at various stages of the vendor lifecycle. These assessments help identify potential threats across the entire supply chain attack surface.
By thoroughly evaluating vendors through security questionnaires, organizations can ensure that their partners' cybersecurity measures align with both internal policies and external regulatory requirements. For strategies to streamline this process, check our guide on automating security questionnaires.
Understanding the purpose and importance of security questionnaires lays the foundation for a comprehensive vendor risk management strategy. For further reading on efficient questionnaire practices, visit our section on streamlining security questionnaires.
Key Components of Security Questionnaires
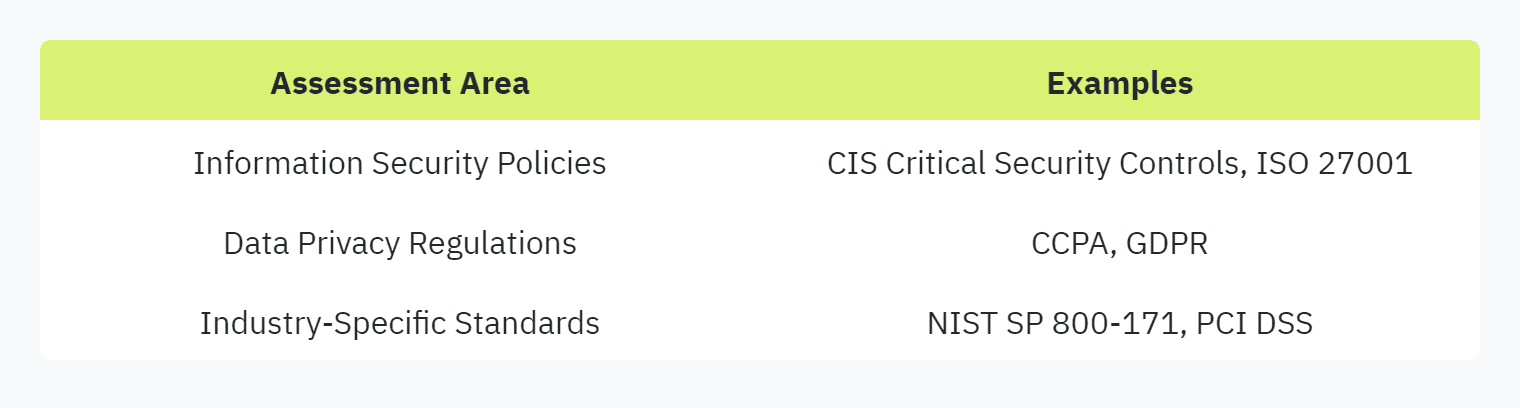
Security questionnaires are essential for evaluating the security and compliance posture of organizations, particularly vendors. These documents typically cover three critical areas: information security policies, data protection measures, and compliance with industry standards. Each component plays a vital role in ensuring robust cybersecurity practices.
Information Security Policies
Information security policies are a cornerstone of any effective cybersecurity strategy. These policies outline how an organization manages, protects, and distributes its information assets. In security questionnaires, questions related to information security policies often aim to assess the maturity and effectiveness of an organization's security measures.
Key aspects evaluated include:
Existence and regular updates of comprehensive security policies.
Employee training programs on security protocols.
Guidelines for data access control and user authentication.
For detailed practices on tracking security questionnaire responses, consider consulting our resources on integrating security questionnaires and collaboration in security questionnaires.
Data Protection Measures
Data protection measures ensure that sensitive information remains confidential, integral, and available. In security questionnaires, this section typically includes questions on how an organization safeguards its data from unauthorized access, breaches, and other security incidents.
Important factors assessed include:
Encryption standards for both data at rest and in transit.
Regular backups and disaster recovery plans.
Protocols for data deletion and sanitization.
Questions about data protection measures help identify whether an organization can maintain the integrity and confidentiality of its data even amidst potential threats. For additional insights on this aspect, check out our article on data privacy in security questionnaires.
Compliance with Industry Standards
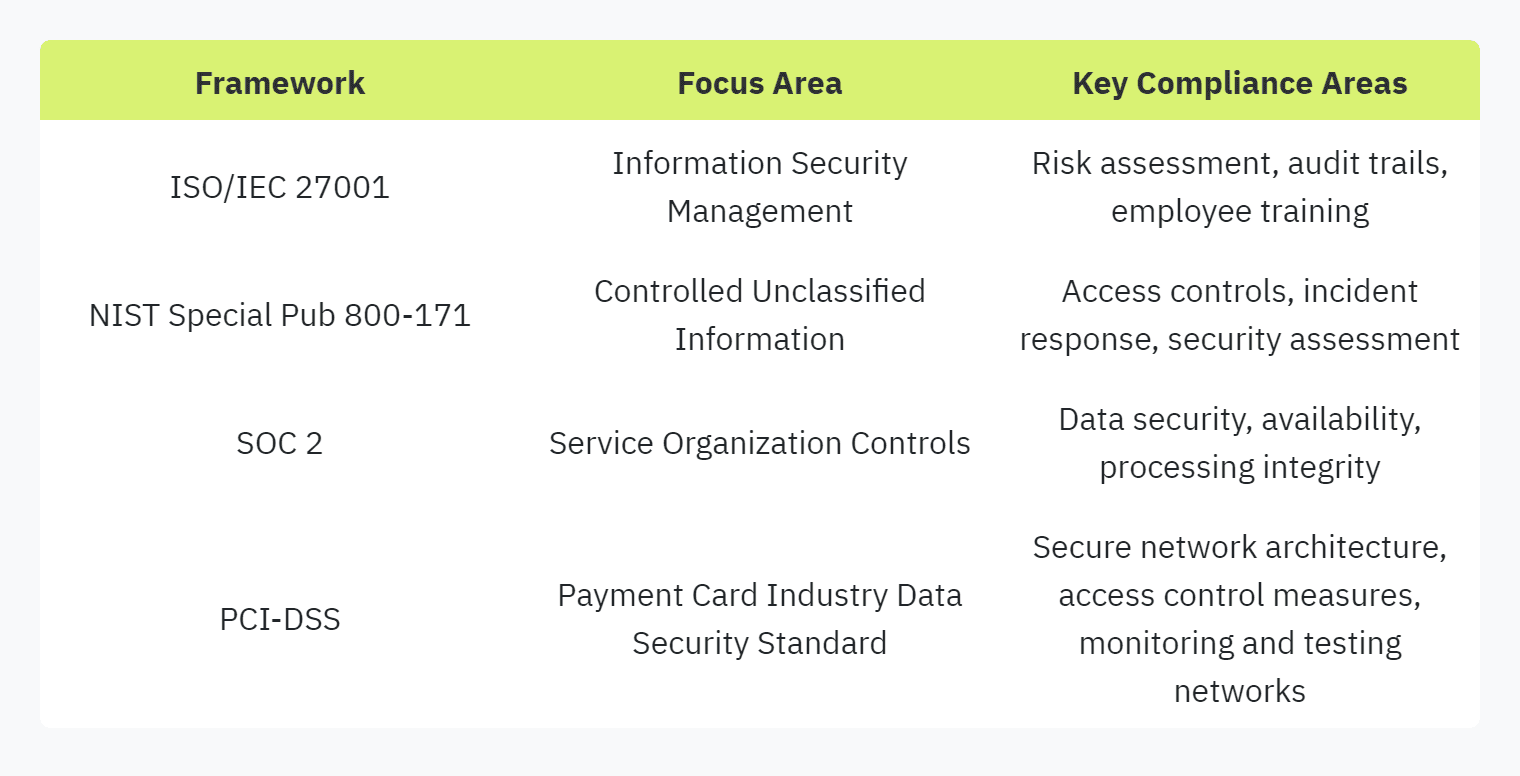
Compliance with industry standards is crucial for organizations to demonstrate their commitment to maintaining high security and privacy levels. Security questionnaires often include questions aimed at understanding how well an organization adheres to established frameworks and regulations, such as:
CIS Critical Security Controls.
Consensus Assessments Initiative Questionnaire (CAIQ).
NIST Special Publication 800-171.
Standardized Information Gathering (SIG) / SIG-Lite.
ISO/IEC 27001.
By adhering to these standards, organizations can ensure their security practices align with both internal requirements and external legal regulations. This alignment helps in mitigating risks throughout the supply chain. For more information on compliance topics, refer to our article on compliance in security questionnaires.
For a comprehensive understanding of why security questionnaires are a nightmare and how to streamline responses, explore our resources on automating security questionnaires and the best practices for security questionnaires.
Streamlining Security Questionnaire Responses
Responding to security questionnaires can be a daunting task for security and compliance officers and IT managers. However, streamlining the process is achievable through effective strategies such as providing relevant answers, creating a knowledge base, and developing remediation plans.
Providing Relevant Answers
Accuracy and relevance are key when responding to security questionnaires. Providing concise and pertinent answers ensures that the recipient gets the necessary information without wading through extraneous details.
Organizations should classify and format their responses according to the questionnaire requirements. Using a "trust profile" to showcase strong security practices can save time and effort (OneTrust). To achieve this, it's beneficial to automate the response process, as explored in our section on automating security questionnaire responses.
Creating a Knowledge Base
A centralized repository for all security assessment answer content is essential for consistency and speed in responding to security questionnaires. The creation of a comprehensive knowledge base can include frequently asked questions, standardized responses, and relevant documentation (Hyperproof).
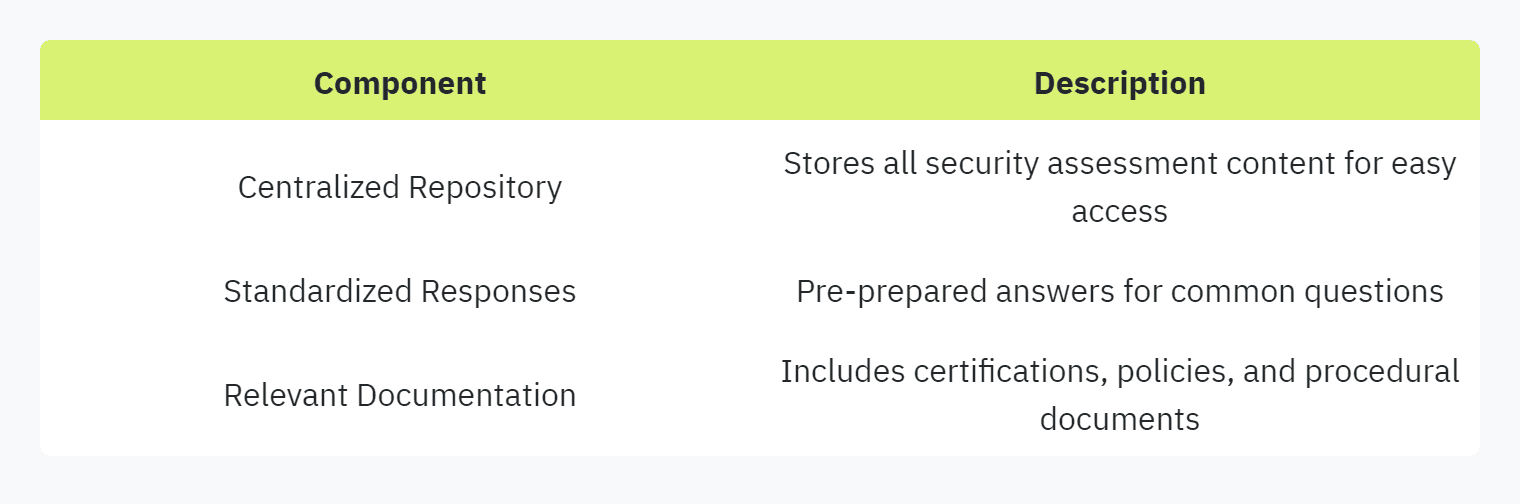
Having a well-maintained knowledge base ensures that all team members provide uniform responses, reducing errors and discrepancies. For more tips on improving the security questionnaire experience, visit our guide on improving security questionnaire experience.
Developing Remediation Plans
A proactive approach in addressing identified security gaps is critical. Developing remediation plans involves outlining steps to resolve any deficiencies highlighted in the security assessments. These plans should be detailed and actionable, demonstrating a commitment to continuous improvement in security practices (UpGuard).
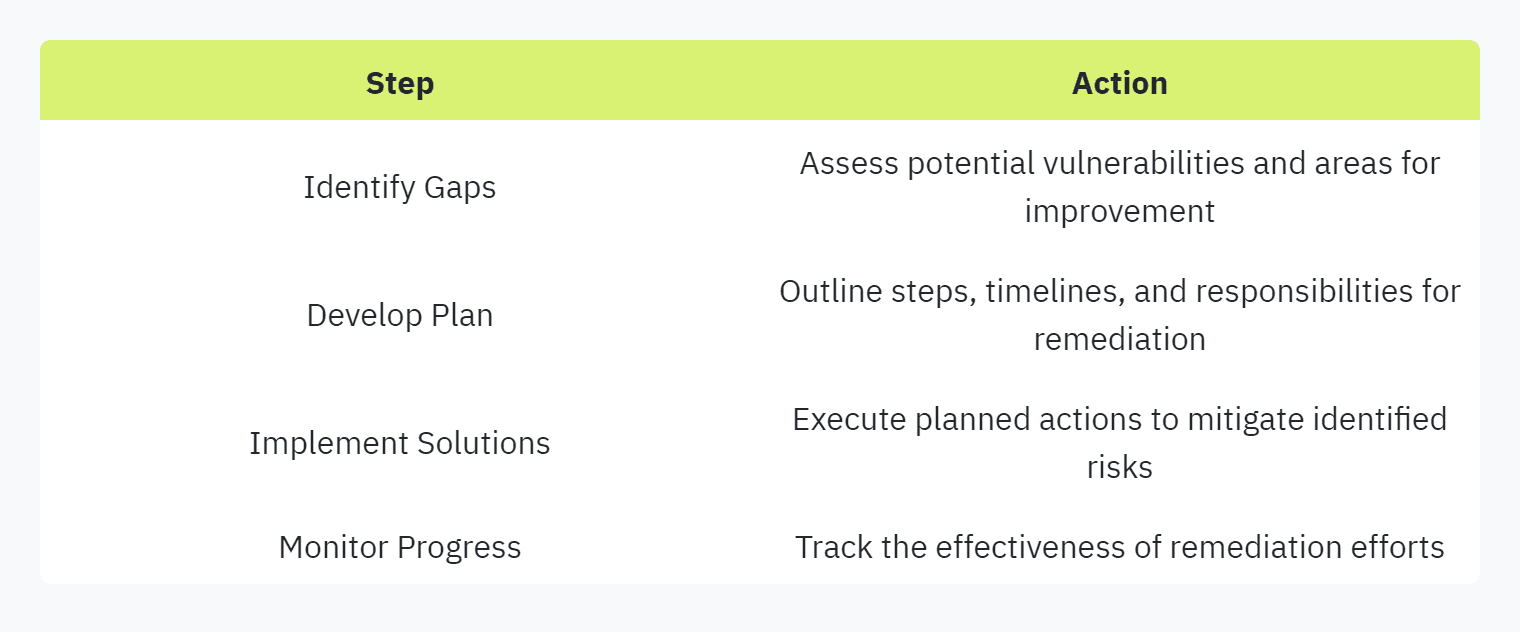
Being prepared with these remediation plans can significantly enhance trust with potential clients and partners. Check out our in-depth article on continuous improvement in security questionnaires for more insights.
Tracking security questionnaire responses and employing automation can further streamline the process, as highlighted in our piece on tracking security questionnaire responses. Implementing these strategies will not only save time and resources but also lead to more effective and efficient management of security questionnaires.
Enhancing Security Practices
Enhancing security practices is essential for managing and mitigating risks in today’s interconnected technology landscape. This involves managing security risks, leveraging automation solutions, and understanding the role of certifications.
Managing Security Risks
Managing security risks is crucial for protecting data integrity and ensuring compliance with industry standards. Security questionnaires help organizations identify third-party and fourth-party risks across the entire supply chain (UpGuard). By proactively addressing these risks, security and compliance officers can safeguard their organization from potential breaches.
Key practices in risk management include:
Conducting regular assessments: Periodic evaluations help identify and address vulnerabilities.
Maintaining an audit trail: An audit trail preserves data integrity by tracking the source of data breaches, allowing timely resolutions.
Implementing remediation plans: Developing and executing plans to address identified security gaps reduces the likelihood of exploitation (UpGuard).
Automation Solutions
Automation solutions play a pivotal role in streamlining the security questionnaire process. By automating repetitive tasks, organizations can reduce the time and effort required to complete these responses. Automation also ensures consistency and accuracy, which is critical for compliance and risk management.
Benefits of automation in security questionnaires include:
Reducing manual workload: Automation minimizes the need for repetitive data entry, freeing up resources for other tasks.
Improving response accuracy: Automated systems ensure consistent and accurate answers, reducing the risk of human error.
Enhancing efficiency: Automated solutions speed up the questionnaire response process, enabling quicker turnaround times (Scytale).
For a deeper understanding of automating security questionnaires, visit our guide here.
Role of Certifications
Certifications are essential in demonstrating an organization's compliance with industry standards and best practices. They provide assurance to vendors and partners that the organization adheres to rigorous security protocols.
Popular certifications for enhancing security practices include:
ISO/IEC 27001: Internationally recognized standard for information security management systems.
SOC 2: Framework for managing customer data based on five "trust service principles": security, availability, processing integrity, confidentiality, and privacy.
GDPR Compliance: Ensures that organizations handling EU citizens' data adhere to stringent data privacy and protection requirements.
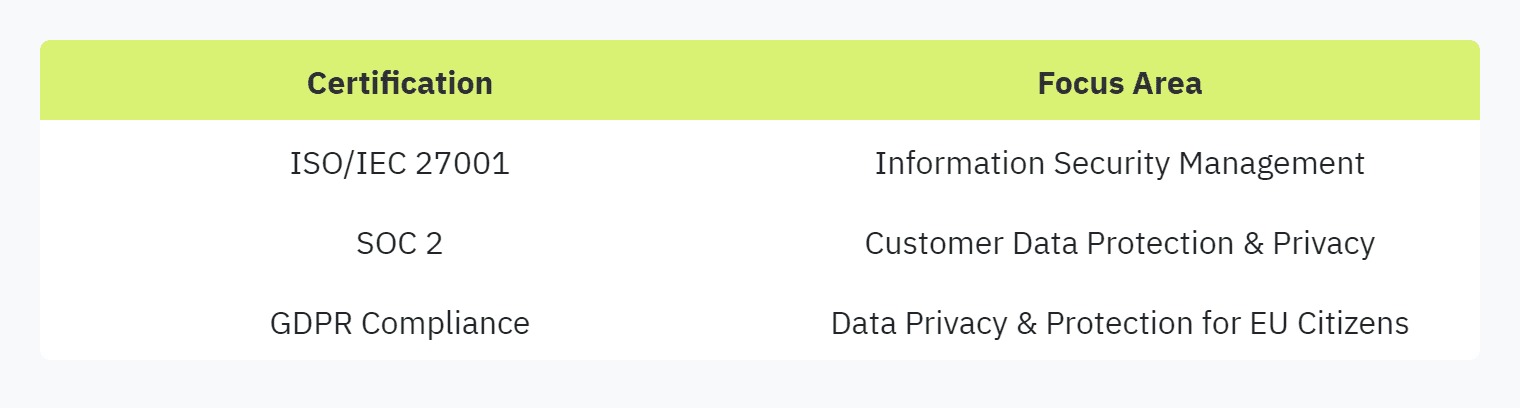
Investing in these certifications helps organizations build trust with stakeholders and demonstrates a commitment to maintaining high security standards (Scytale). For more information on integrating certifications into your security practices, visit compliance in security questionnaires.
By managing security risks, leveraging automation, and achieving relevant certifications, organizations can enhance their security practices and ensure a robust, secure environment. For more tips on best practices, explore our section on best practices for security questionnaires.
Enter your email to start accelerating your sales today.
















