How to overcome resistance to automating security questionnaires
Share This Article

Understanding Security Questionnaires
Security questionnaires play a crucial role in evaluating a company's security posture, especially for IT managers, security officers, and SaaS startups aiming for compliance standards such as SOC 2. They help organizations assess and document their security measures, but the process can be cumbersome and time-consuming.
Challenges of Manual Completion
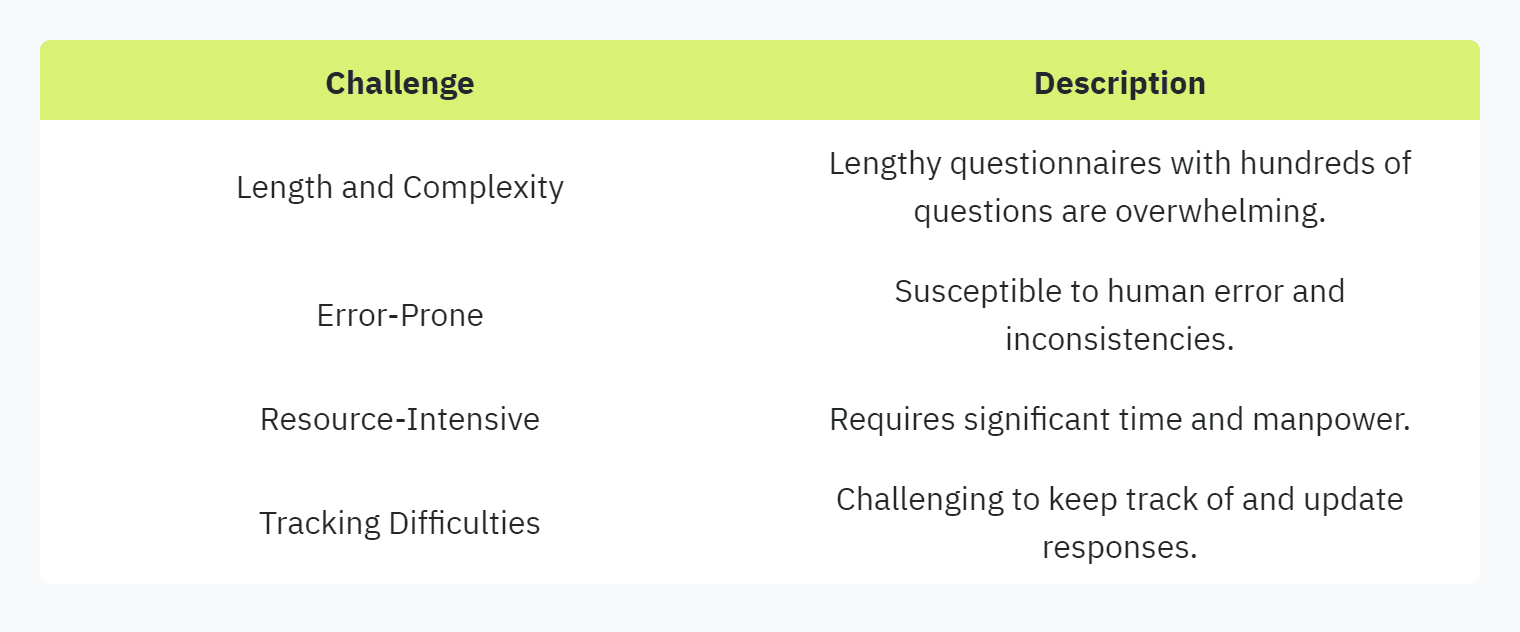
Manual completion of security questionnaires presents several challenges. Firstly, these questionnaires can be extremely lengthy and complex, often consisting of hundreds of questions that require detailed responses. This makes the process overwhelming for vendors, especially when dealing with multiple questionnaires from different clients.
Secondly, manual completion is prone to human error. Inaccuracies and inconsistencies can easily occur, leading to incomplete or misleading responses. This not only affects the quality of the assessments but also raises the risk of non-compliance.
Thirdly, the process is often resource-intensive. Organizations need to allocate significant time and manpower to complete these questionnaires, which could otherwise be spent on core business activities. Tracking and updating responses manually also presents difficulties, further adding to the inefficiency.
To summarize the challenges:
For more on the common frustrations of manually completing security questionnaires, visit our article on common frustrations with security questionnaires.
Importance of Automation
Automating security questionnaires mitigates many of the issues associated with manual completion. Automation tools can significantly enhance efficiency and accuracy by streamlining the process and reducing the likelihood of errors. These tools rely on advanced technologies such as Natural Language Processing (NLP) and Artificial Intelligence (AI) to process and generate responses quickly and accurately.
Moreover, automation provides organizations with a proactive approach to risk management. Tools can flag areas needing immediate attention and optimize resource allocation through automatic risk scoring (Vendict). This ensures a continuous real-time monitoring and updating of data security infrastructure, keeping responses consistent with current practices.
Additionally, automating security questionnaires facilitates better compliance tracking. Automated systems can rapidly adjust to new compliance requirements and ensure that responses reflect the latest security measures, which is crucial for retaining a competitive edge in the marketplace (Strike Graph).
Key advantages of automating security questionnaires:

To learn more about the benefits and technologies involved in automating security questionnaires, visit our guide to automating security questionnaires.
Benefits of Automating Security Questionnaires
Automating security questionnaires offers several advantages, particularly when confronting the resistance to automating security questionnaires. Let's explore two critical benefits: efficiency and accuracy, and proactive risk management.
Efficiency and Accuracy
Security questionnaires can be lengthy and complex, and manual completion is often time-consuming, prone to human errors, and inconsistent (Vendict). Automation transforms this cumbersome process into an efficient and dependable system.
Advantages of Automation:
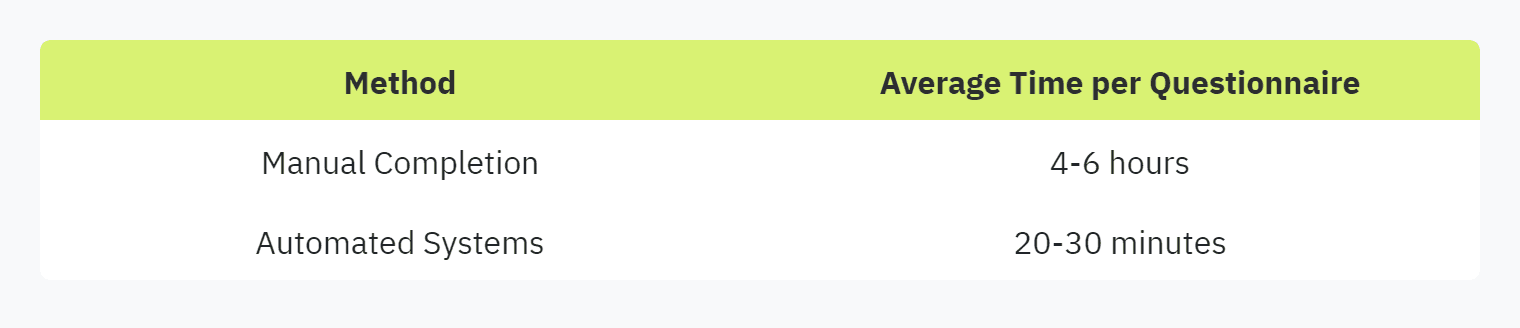
Time-Saving: Automated systems significantly reduce the time spent filling out questionnaires. What took hours or even days manually can now be completed in minutes.
Reduced Human Error: Automation minimizes errors due to fatigue or oversight by ensuring consistent, accurate data entry.
Resource Efficiency: Automation enables human resources to focus on more strategic, value-added tasks rather than repetitive data entry.
The following table highlights the time saved through automation:
For more details on enhancing the efficiency of security questionnaires, visit our guide on efficient security questionnaires.
Proactive Risk Management
Automating security questionnaires provides a proactive approach to risk management. By streamlining the questionnaire process, organizations can stay ahead in identifying and mitigating potential risks (Vendict).
Proactive Features:
Real-Time Analysis: Automated systems can analyze responses in real-time, quickly identifying areas of concern or non-compliance.
Consistent Updates: Automation ensures that questionnaires are consistently updated with the latest security standards and practices.
Improved Tracking: Automation offers better tracking of questionnaire responses and performance metrics, aiding in ongoing risk assessment.
Enhanced risk management capabilities ensure that organizations not only comply with industry standards but also maintain a robust security posture.
For a comprehensive understanding of automating security questionnaires, refer to our article on proactive risk management.
By integrating automation into the completion of security questionnaires, organizations can address common frustrations with security questionnaires and improve overall efficiency and risk management. Dive deeper into the technical aspects and further benefits by exploring our resources on tools to simplify security questionnaires and streamlining security questionnaires.
Tools and Technologies for Automation
The shift to automating security questionnaires can lead to greater efficiency and accuracy, allowing organizations to manage risks more proactively. Exploring the tools and technologies available can provide a clearer understanding of how to overcome resistance to automating security questionnaires.
Natural Language Processing (NLP) Solutions
Natural Language Processing (NLP) solutions have significantly transformed the way security questionnaires are handled. By understanding and processing human language, NLP tools can complete security questionnaires much faster than manual methods.
For example, Vendict's tool leverages NLP to complete security questionnaires 50 times faster while ensuring precise and accurate answers (Vendict). This speed and precision are essential for reducing the time and effort required, allowing organizations to focus on core business tasks.
NLP solutions parse the questions and automatically generate appropriate responses based on a pre-built knowledge base. This approach helps in:
Reducing inconsistencies in responses
Accelerating the turnaround time for questionnaires
Enhancing the overall efficiency of the security compliance process
Here’s a table illustrating the potential time savings with NLP solutions:

For tips on streamlining the completion process, visit our guide on streamlining security questionnaires.
Artificial Intelligence (AI) Integration
Another technology driving the automation of security questionnaires is Artificial Intelligence (AI). AI integration can provide even more sophisticated methods for automating tedious tasks associated with these questionnaires.
Strike Graph, for example, has developed an AI-based solution that utilizes Machine Learning Processing technology to streamline the security questionnaire process. This AI solution can:
Automate the association of existing IT controls with questionnaire answers
Deliver accurate responses within two business days
Enable delegation of questionnaire completion tasks
Moreover, AI can help in building and maintaining a comprehensive knowledge base. Effective AI solutions ensure that generated responses are relevant, consistent, and up-to-date, which aligns with the company's overall security posture and documented policies (Scytale).
Here’s an example of how AI integration impacts the efficiency and accuracy of security questionnaire responses:
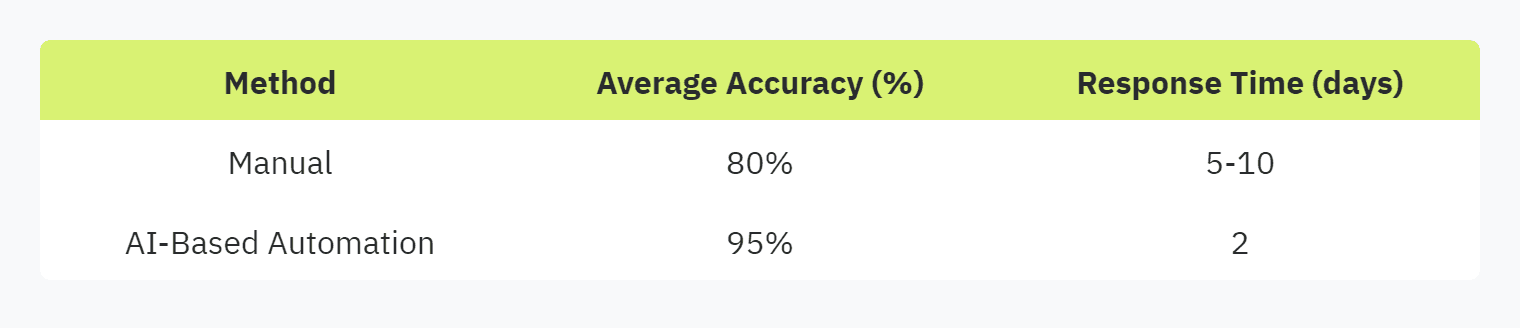
Organizations looking to integrate AI into their security questionnaire processes can read more about the benefits in our article on ai and automation in security questionnaires.
By leveraging NLP and AI technologies, security and compliance officers, IT managers, and SaaS startups can overcome resistance and embrace the benefits of automating security questionnaires. For further reading, consider exploring tips and best practices for reducing time to complete security questionnaires and ensuring compliance in security questionnaires.
Overcoming Resistance to Automation
The transition towards automating security questionnaires presents several challenges, often leading to resistance. Addressing concerns about validity, reliability, and accuracy is crucial for overcoming barriers to adoption.
Validity and Reliability Concerns
A major concern among organizations is the validity and reliability of automated security questionnaires. Security and compliance officers fear that automated tools may not capture all necessary details, leading to incomplete or inaccurate assessments. These concerns stem from the belief that automation might overlook nuances and complexities inherent in manual completion.
However, modern tools incorporate advanced technologies like Natural Language Processing (NLP) and Artificial Intelligence (AI) to enhance accuracy. By leveraging these technologies, automated systems can interpret open-ended responses, identify relevant information, and provide consistent results.
Addressing Validity and Reliability Concerns:
Regular Updates and Audits: Ensure that the automated tools are frequently updated to reflect current security standards and compliance requirements. Conduct regular audits to validate the information collected.
Hybrid Approaches: Combine automated processes with manual reviews. This ensures that critical areas are double-checked by human experts.
User Training: Provide thorough training on how to effectively use and interpret the outputs of automated systems (TrustCloud Community).
Learn more about why security officers face challenges with security questionnaires here.
False Positives and Self-Reporting Challenges
Another critical issue is the potential for false positives and the reliance on self-reporting. Automated systems may flag non-critical issues or generate misleading alerts, leading to unnecessary investigations and resource allocation. Additionally, these systems often depend on self-reported data from third parties, which can sometimes be inaccurate or incomplete.
Despite these challenges (ScienceDirect), there are strategies to mitigate their impact:
Mitigating False Positives and Self-Reporting Challenges:
Calibration and Threshold Setting: Adjust the sensitivity of automated systems to reduce the incidence of false positives. Establish thresholds that differentiate between critical and non-critical issues.
Cross-Verification: Implement mechanisms to cross-verify self-reported data. Use corroborative methods such as third-party assessments or internal audits to validate the information provided.
Feedback Mechanisms: Develop feedback loops to refine and improve automated systems based on user experiences and detected errors (Deloitte Study).
To explore more strategies and techniques, visit our guide on best practices for security questionnaires and automating security questionnaire responses.
By addressing these concerns head-on and implementing robust strategies to ensure accuracy and reliability, organizations can significantly reduce resistance and embrace the efficiency of security questionnaire automation. For more insights, read about data insights in security questionnaires and the role of AI in security questionnaires.
Enter your email to start accelerating your sales today.
















